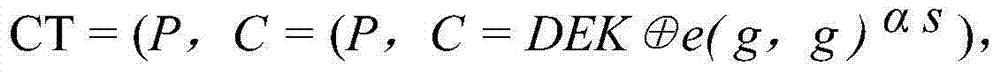A Key Encryption Method Based on File Attributes
A key encryption and file attribute technology, applied in electrical components, digital transmission systems, secure communication devices, etc., can solve problems such as low efficiency of distributed storage systems, unguaranteed key security, and cumbersome user verification certificates , to achieve the effects of reducing time complexity, protecting security, and efficiently encrypting data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
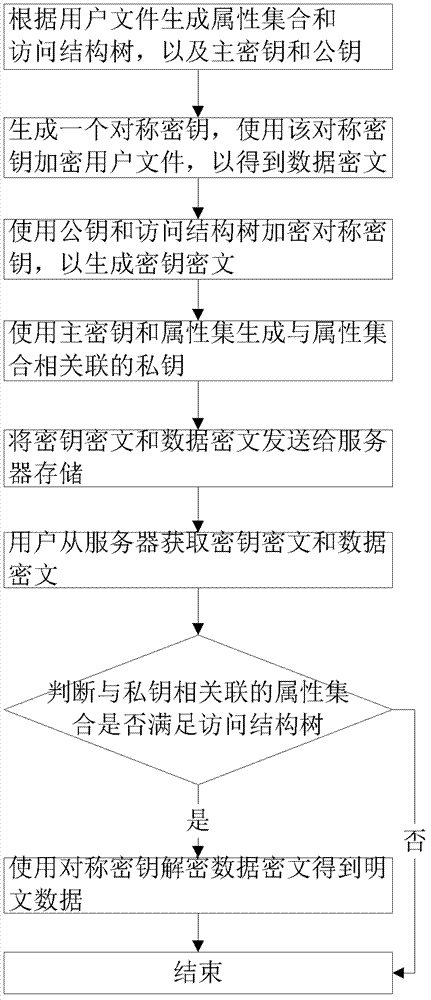
[0026] Such as figure 1 Shown, the inventive method comprises the following steps:
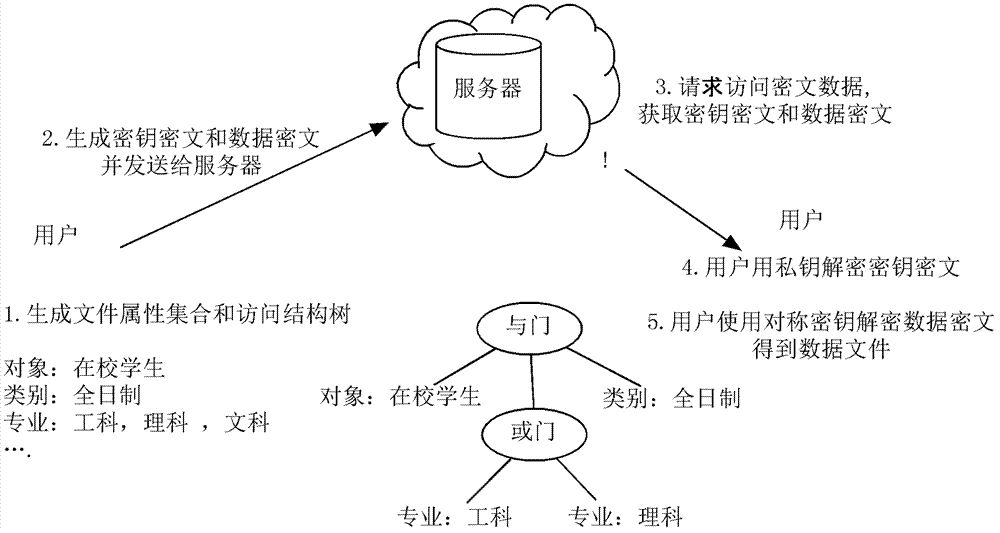
[0027] (1) Receive user files, generate attribute set S={s according to user files 1 ,s 2 ,...,s n}, access structure tree P, master key MK and public key PK;
[0028] The access structure tree is used to describe an access control strategy, each leaf node of the tree represents an attribute item, and each internal node represents a relation function, and the relation function is AND or OR threshold. PK=G 0 , g; MK=(β, g α ), where g is a generator, G 0 is the prime number order group whose generator is g, and α and β are two randomly generated natural numbers;
[0029] (2) Randomly generate a symmetric key DEK, and use the symmetric key DEK and the Advanced Encryption Standard (AES for short) symmetric encryption algorithm to encrypt user files to obta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com