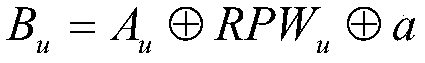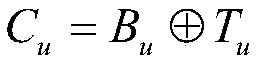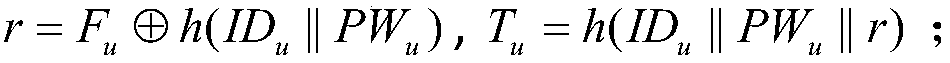A security authentication method based on smart home
A technology of security authentication and smart home, which is applied in the field of security authentication based on smart home, and can solve problems such as security, increased information leakage, and the risk of being intercepted and unsafe
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The following is a further detailed description in conjunction with the present invention.
[0042] The present invention proposes an improved security authentication protocol under the smart home, so that the user and the M2M device can realize a secure conversation through the local gateway. The user sends his ID to the local gateway through the secure channel, and the local gateway securely stores the registered user ID. Then proceed to the next stage of the conversation process.
[0043] The present invention includes the following steps:
[0044] Step 1. The user is registered and authenticated in the home gateway;
[0045] Step 2. The home gateway sends a message to the smart terminal;
[0046] Step 3. The smart terminal authenticates and forms the session key reply stage;
[0047] Step 4. The home gateway responds to the user stage;
[0048] Step 5. The user and the smart terminal form a session key stage.
[0049] Parameter description: ID u ,PW u Respectively represent th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com