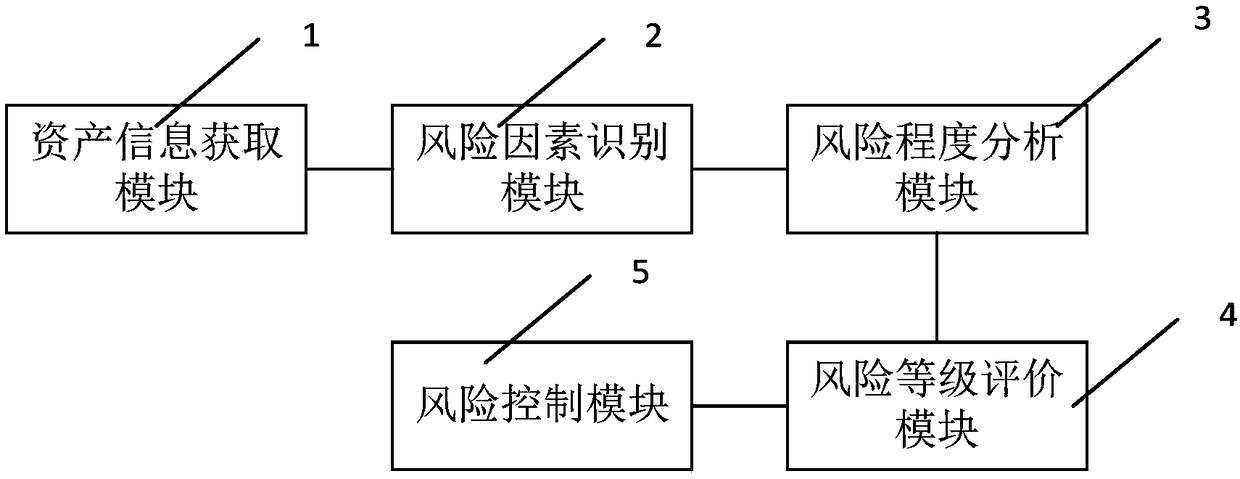
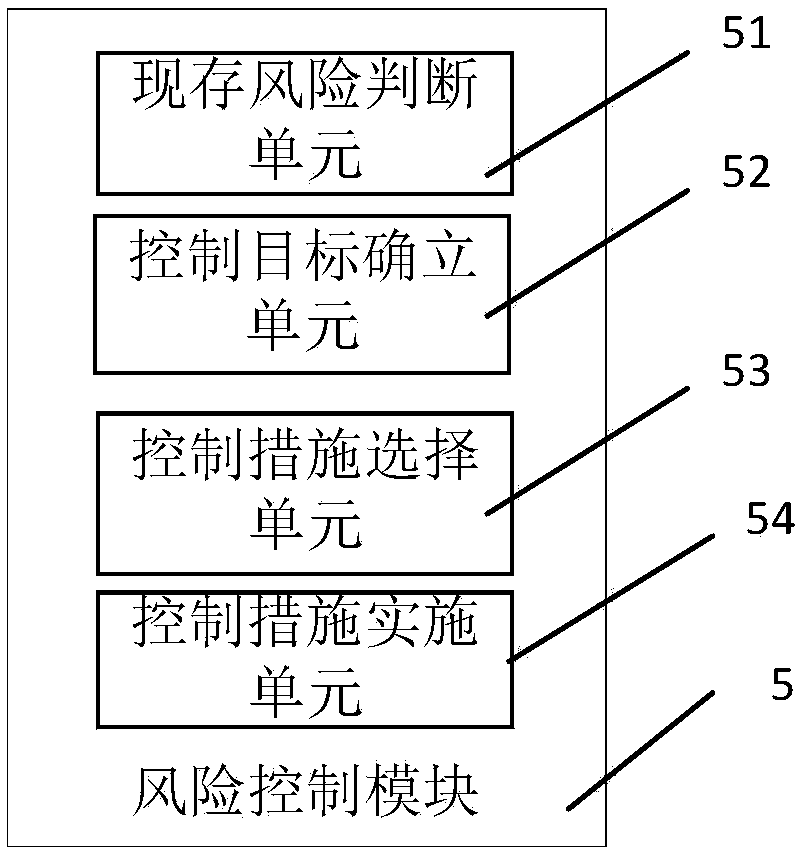
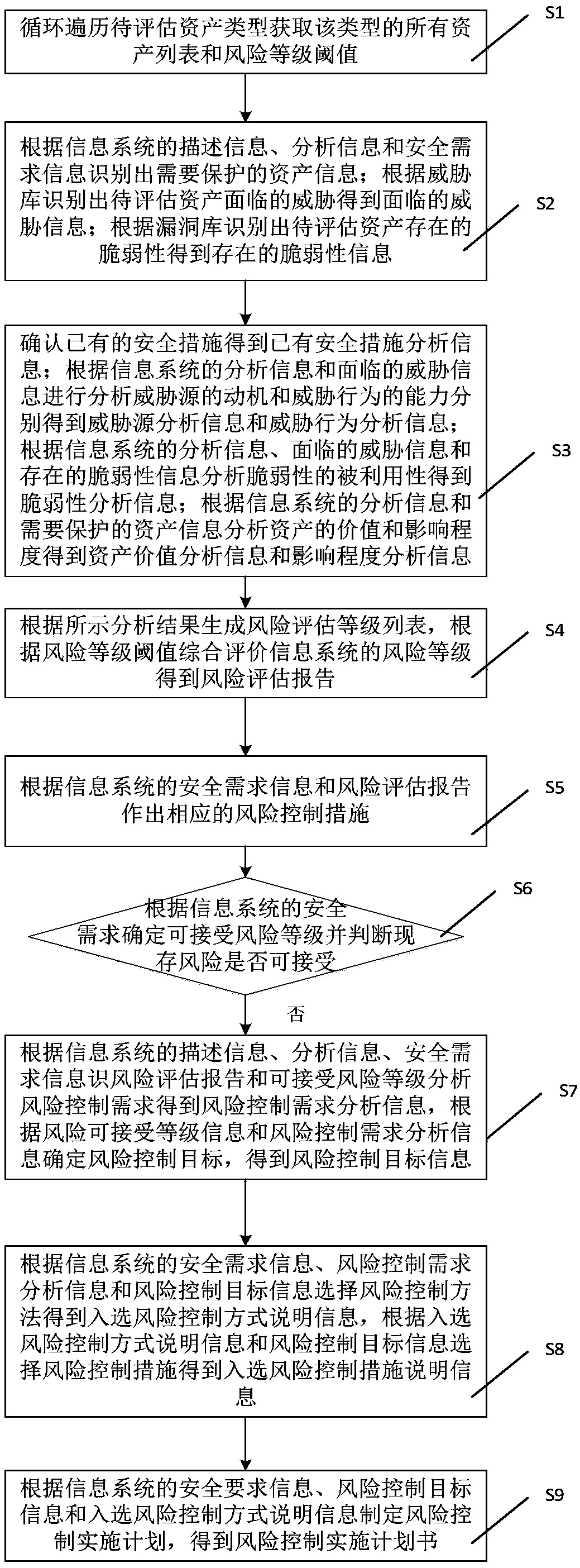
Information security risk assessment system and method
A risk assessment system and information system technology, applied in the direction of instruments, data processing applications, resources, etc., can solve the problems of small assessment scope, single assessment items, ignoring potential threats, etc., and achieve the effect of wide assessment scope
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Embodiments of the technical solutions of the present invention will be described in detail below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, so they are only examples, and should not be used to limit the protection scope of the present invention.
[0030] It should be noted that, unless otherwise specified, the technical terms or scientific terms used in this application shall have the usual meanings understood by those skilled in the art to which the present invention belongs.
[0031] Information security risk (referred to as risk) is a potential and negative thing that has not occurred, and a security incident is an obvious and negative thing that has occurred. Risk is the premise of events, and events evolve from risks under certain conditions. The composition of risk includes five aspects: origin, mode, pathway, receptor and consequence. The source...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com