An attack detection method and device
An attack detection and attack signature technology, applied in the field of network communication, can solve the problems of low efficiency of custom signature attack detection and low query efficiency, and achieve the effects of efficient intrusion prevention, saving storage cost, and improving the efficiency of signature matching.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order for those skilled in the art to better understand the technical solutions in the embodiments of this specification, the technical solutions in the embodiments of this specification will be described in detail below in conjunction with the drawings in the embodiments of this specification. Obviously, the described implementation Examples are only some of the embodiments in this specification, not all of them. All other embodiments obtained by persons of ordinary skill in the art based on the embodiments in this specification shall fall within the scope of protection.
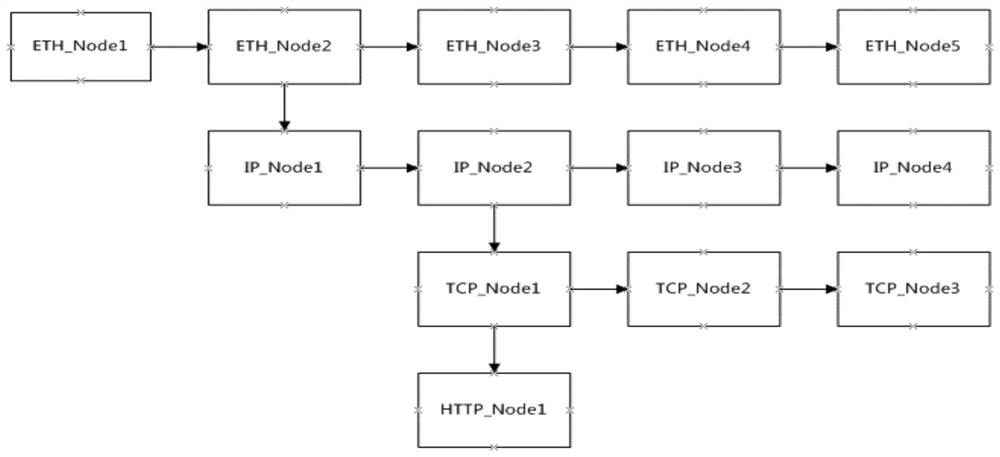
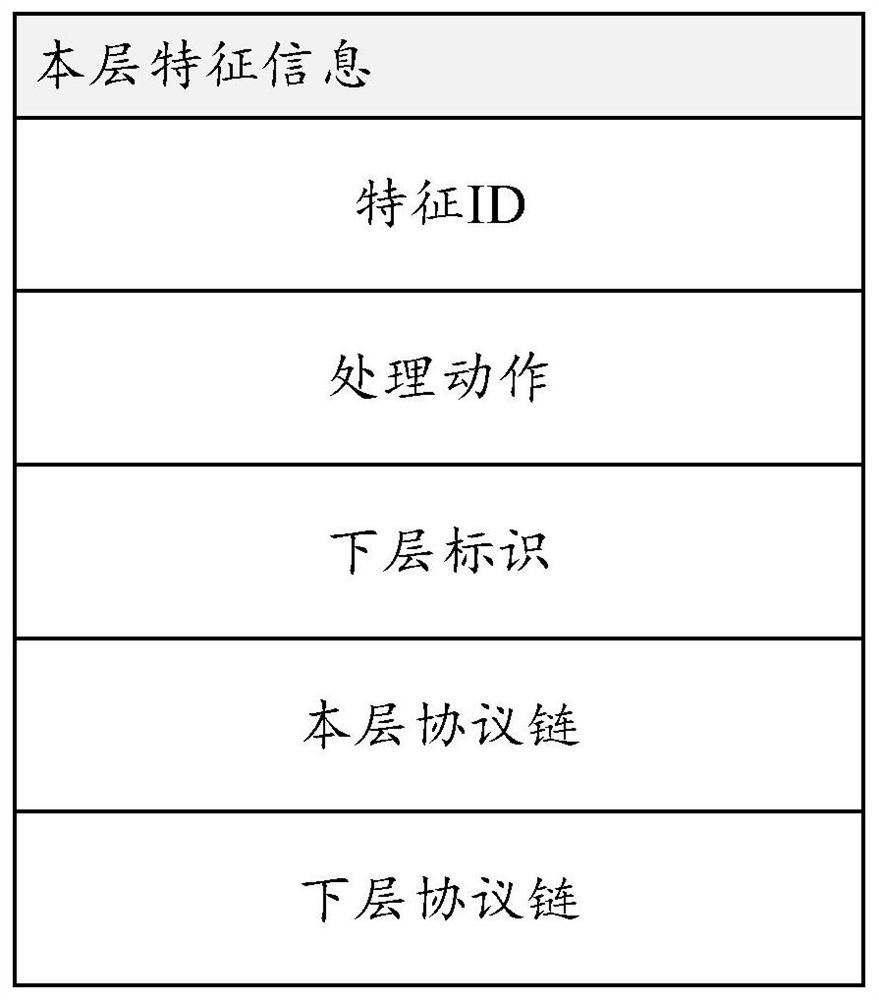
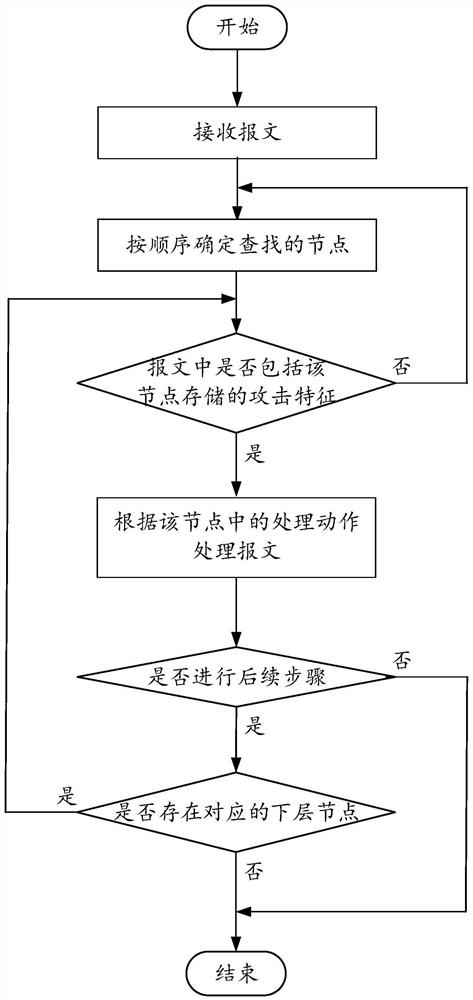
[0025] Among common network packet attack signatures, some signatures are extracted based on specific fields in the header of the protocol, specific strings in the packet, etc. These signatures are generally stored in the signature database of the IPS device. There are also some features, but there are certain rules in some parts, for example, the message is of a specific length, a certain byte of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com