A secure retrieval method for large-scale images in cloud environment
A cloud environment, large-scale technology, used in computer security devices, character and pattern recognition, special data processing applications, etc., can solve the problems of security, accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
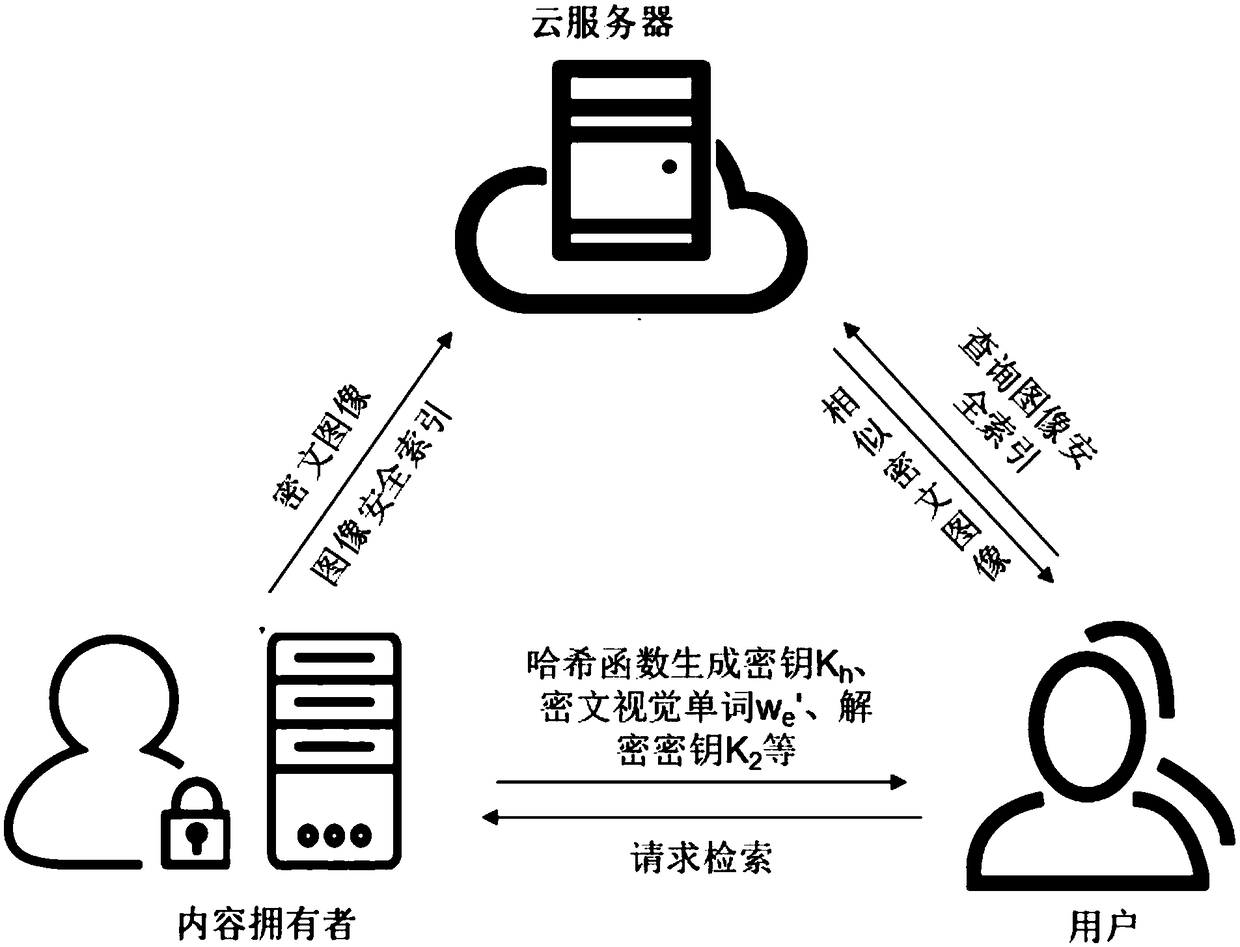
[0064] The present invention provides an image security retrieval method based on the bag-of-words model in a cloud environment. The specific implementation steps are as follows:
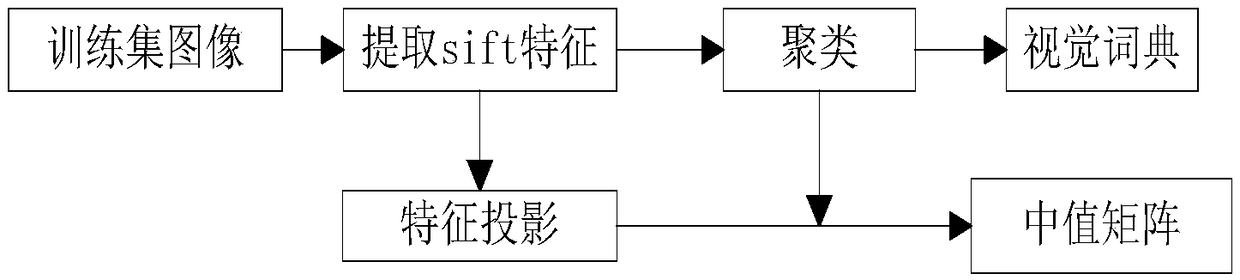
[0065] Step 1. Establish a bag-of-words model based on the image database to generate a visual dictionary and a median matrix. Specifically include the following sub-steps:
[0066] Step 1.1, local feature extraction: for each image in the image library, use the sift feature extraction algorithm to extract image features and generate feature point descriptors;
[0067] Step 1.2, build a visual dictionary: use the k-means clustering algorithm to train the feature points in the image training data set to generate k cluster centers, and each cluster center is represented as a visual word, which constitutes a k-dimensional visual dictionary W ;
[0068] Step 1.3, construct the median matrix: calculate the median value in each dimension for the image feature vectors belonging to the c(c∈[1,k])th cluste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com