Encryption protection system and method for neural network model relating to iteration and random encryption
A neural network model and random encryption technology, applied in the field of artificial neural network protection mechanism, to achieve the effect of developer rights protection, use and release
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
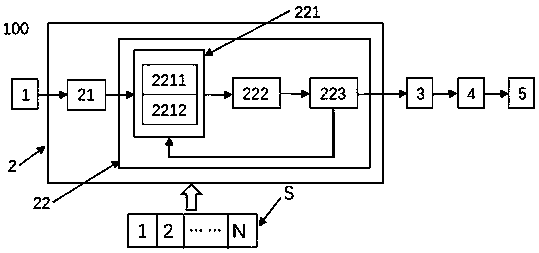
[0052] For a system structure diagram of a neural network model encryption protection system 100 involving iterative and random encryption, please refer to the appendix figure 1 For the encryption principle of the encryption module 2 of the encryption protection system 100, please refer to the appended figure 2 , the encryption protection system 100 includes a data input module 1 , an encryption module 2 , an encrypted data input module 3 , an artificial neural network model module 4 and a data output module 5 . The data input module 1 is connected to the signal of the encryption module 2, the signal of the encryption module 2 is connected to the signal of the encrypted data input module 3, the signal of the encrypted data input module 3 is connected to the signal of the artificial neural network model module 4, and the signal of the artificial neural network model module 4 is connected to the signal of the data output module 5 connected.
[0053] Further, the data input mod...
Embodiment 2
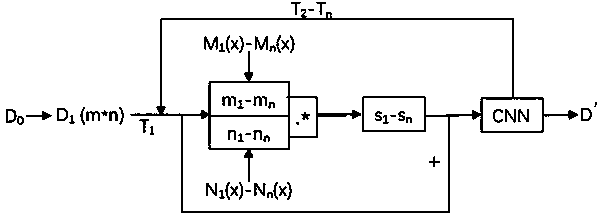
[0068] For the method flow chart of a neural network model encryption protection method involving iterative and random encryption, please refer to the appendix Figure 4 , the method includes the following steps:
[0069] Step S1. Provide raw data D 0 ;
[0070] Step S2. For the original data D 0 Perform encryption processing to generate encrypted data D';
[0071] Step S3. Input the encrypted data D' into the artificial neural network model, and the artificial neural network model calculates the encrypted data D' to obtain a result;
[0072] Step S4. Output the calculated result.
[0073] Wherein, step S2 specifically includes:
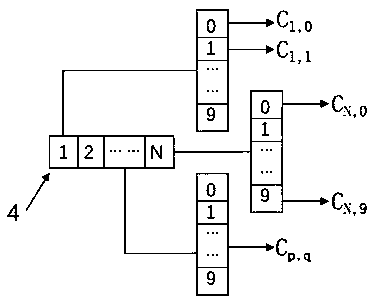
[0074] Step S21. Provide a group of keys S with N digits as the control amount, the keys S specifically define the 0 Encryption processing; wherein, the length of the key S is limited by the encryption method and encryption requirements in the encryption process; each of the N digits of the key S is selected from one of Arabic numerals 0-9;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com