Method and device for detecting abnormal behavior of internal users in an enterprise
An internal user and detection method technology, applied in the field of network security, can solve the problems of ignoring user behavior details, over-reliance on manual determination and extraction of user behavior characteristics, and failure of internal threat detection to achieve the effect of solving the lack of details
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
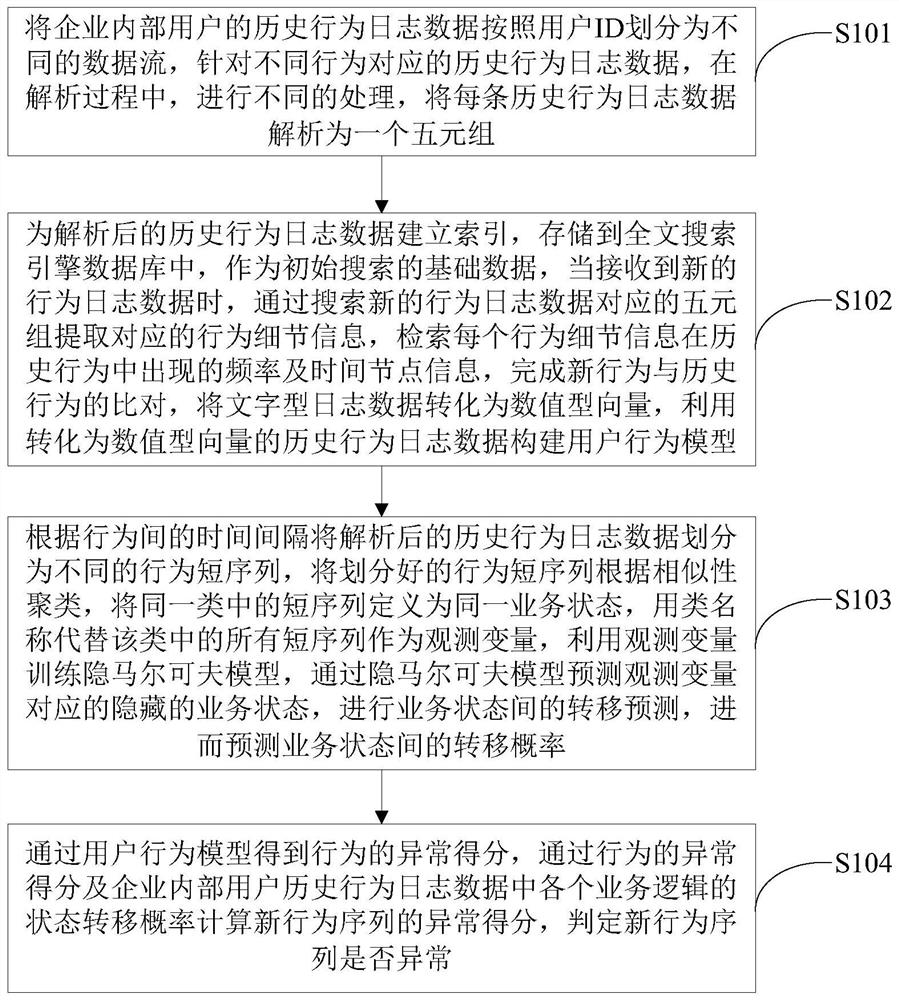
[0063] like figure 1 As shown, a method for detecting an abnormal behavior of an enterprise internal user of the present invention includes the following steps:
[0064] Step S101: Divide the historical behavior log data of internal users in the enterprise into different data streams according to the user ID, and perform different processing in the analysis process for the historical behavior log data corresponding to different behaviors, and analyze each historical behavior log data as a five-tuple.
[0065] Step S102: Build an index for the analyzed historical behavior log data and store it in the full-text search engine database as the basic data for the initial search. When new behavior log data is received, search for the five-element corresponding to the new behavior log data The group extracts the corresponding behavior detail information, retrieves the frequency and time node information of each behavior detail information in the historical behavior, completes the com...
Embodiment 2
[0069] Another method for detecting abnormal behavior of internal users in an enterprise of the present invention includes the following steps:
[0070] Step S201: Divide the historical behavior log data of internal users in the enterprise into different data streams according to the user ID, and perform different processing in the analysis process for the historical behavior log data corresponding to different behaviors, and analyze each historical behavior log data is a five-tuple;
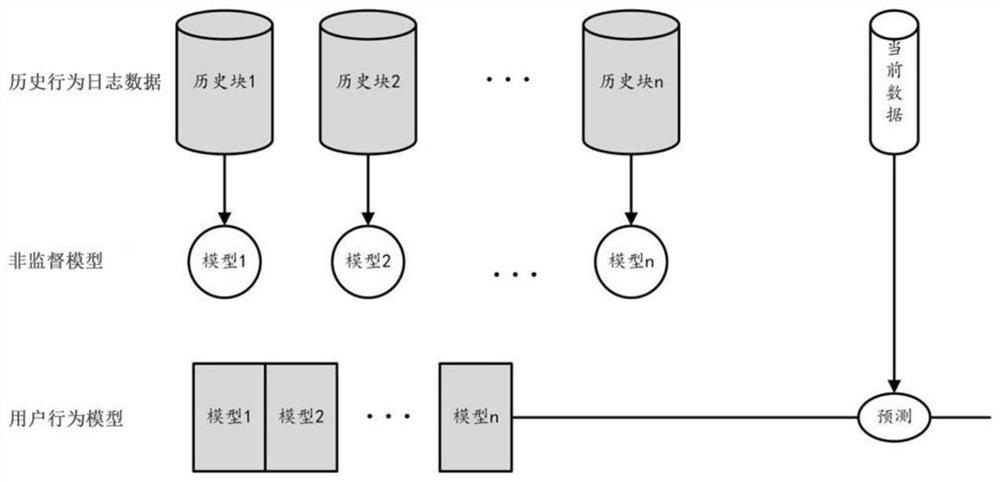
[0071] In order to ensure that legitimate users can effectively access protected resources, prevent unauthorized access by illegal users, and retain user behavior records for violation investigation, log analysis and auditing have become important means to protect enterprise information security and monitor internal user behavior compliance. In the audit system, various sensors deployed in the enterprise will continuously record user operation behaviors, generate relevant logs, and store them in...
Embodiment 3
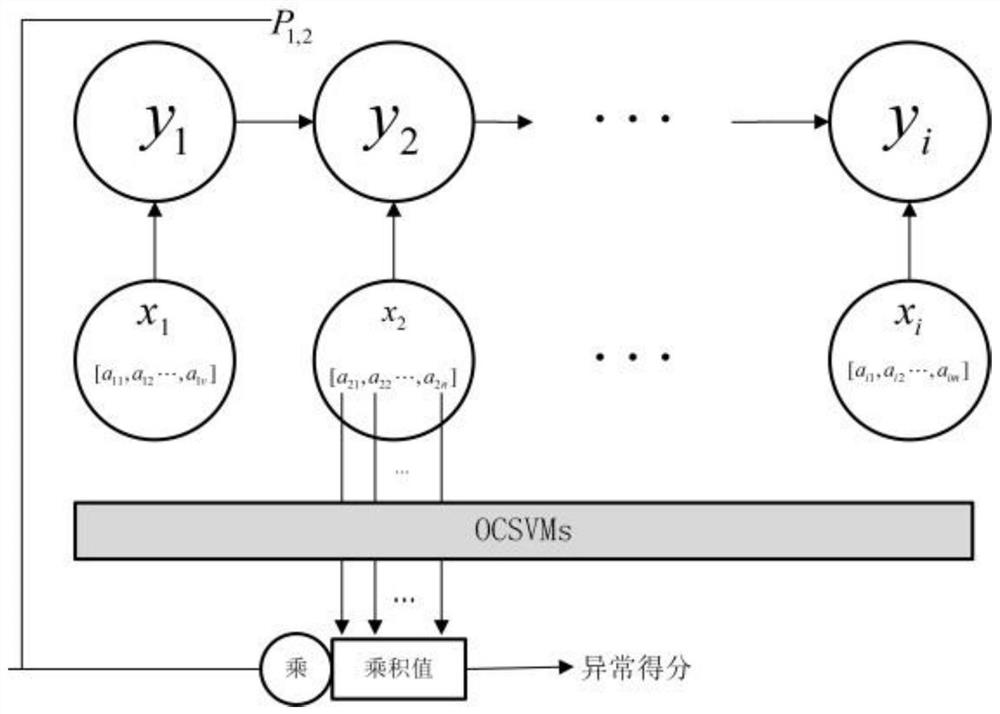
[0109] like Image 6 As shown, a device for detecting abnormal behaviors of internal users in an enterprise of the present invention includes:
[0110] The behavior log acquisition and preprocessing module 301 is used to divide the historical behavior log data of the internal users of the enterprise into different data streams according to the user ID, and perform different processing in the parsing process for the historical behavior log data corresponding to different behaviors, Parse each piece of historical behavior log data into a five-tuple;
[0111] Behavior detail modeling module 302, used for building an index for the historical behavior log data after analysis, storing in the full-text search engine database, as the basic data of initial search, when receiving new behavior log data, by searching new behavior log data The five-tuple corresponding to the log data extracts the corresponding behavior details, retrieves the frequency and time node information of each beh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com