Server evidence-obtaining method based on virtual machine introspection
A virtual machine and server technology, applied in the information field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0084] The embodiments of the present invention will be described in detail below with reference to the accompanying drawings, but the present invention can be implemented in various ways defined and covered by the claims.
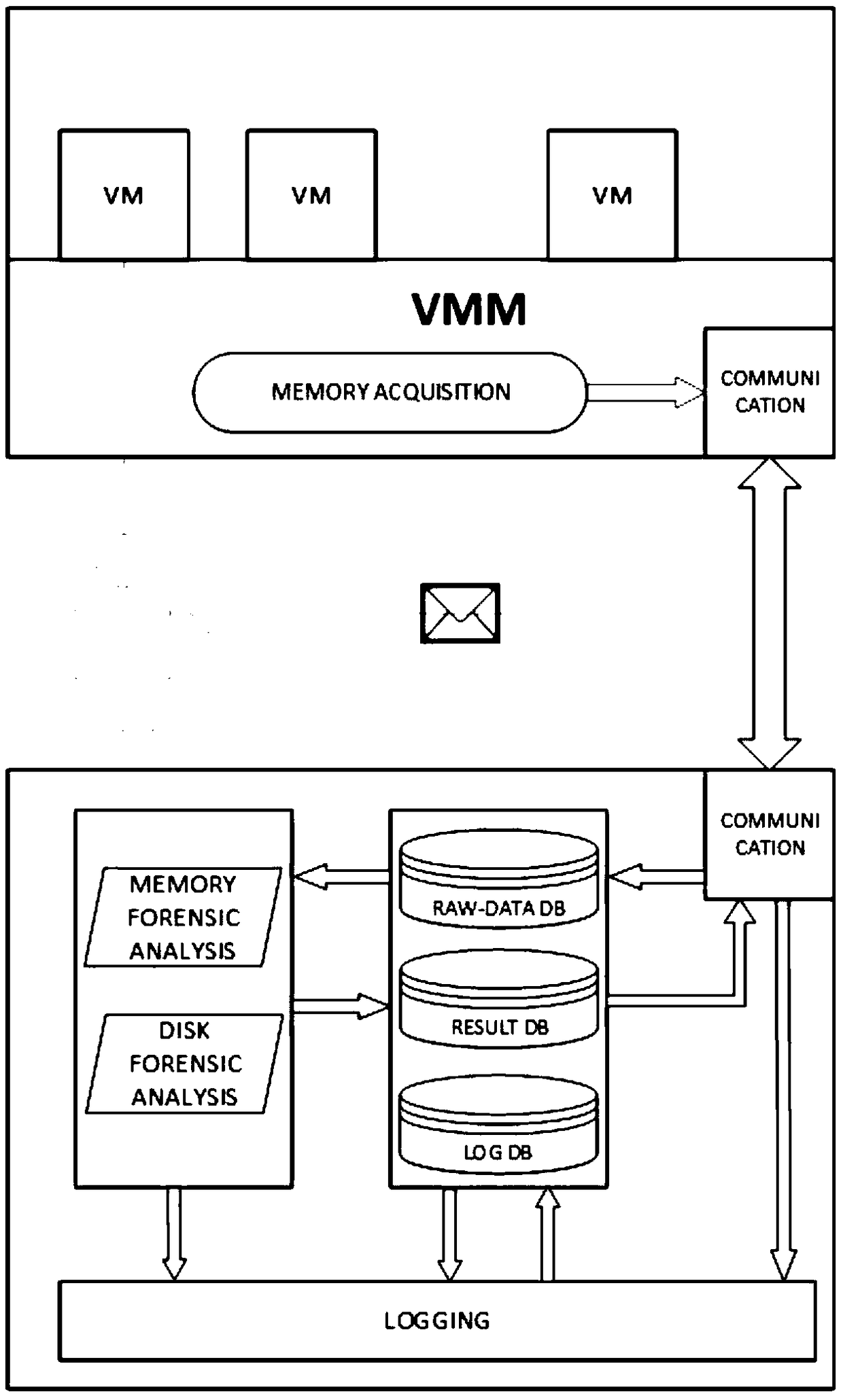
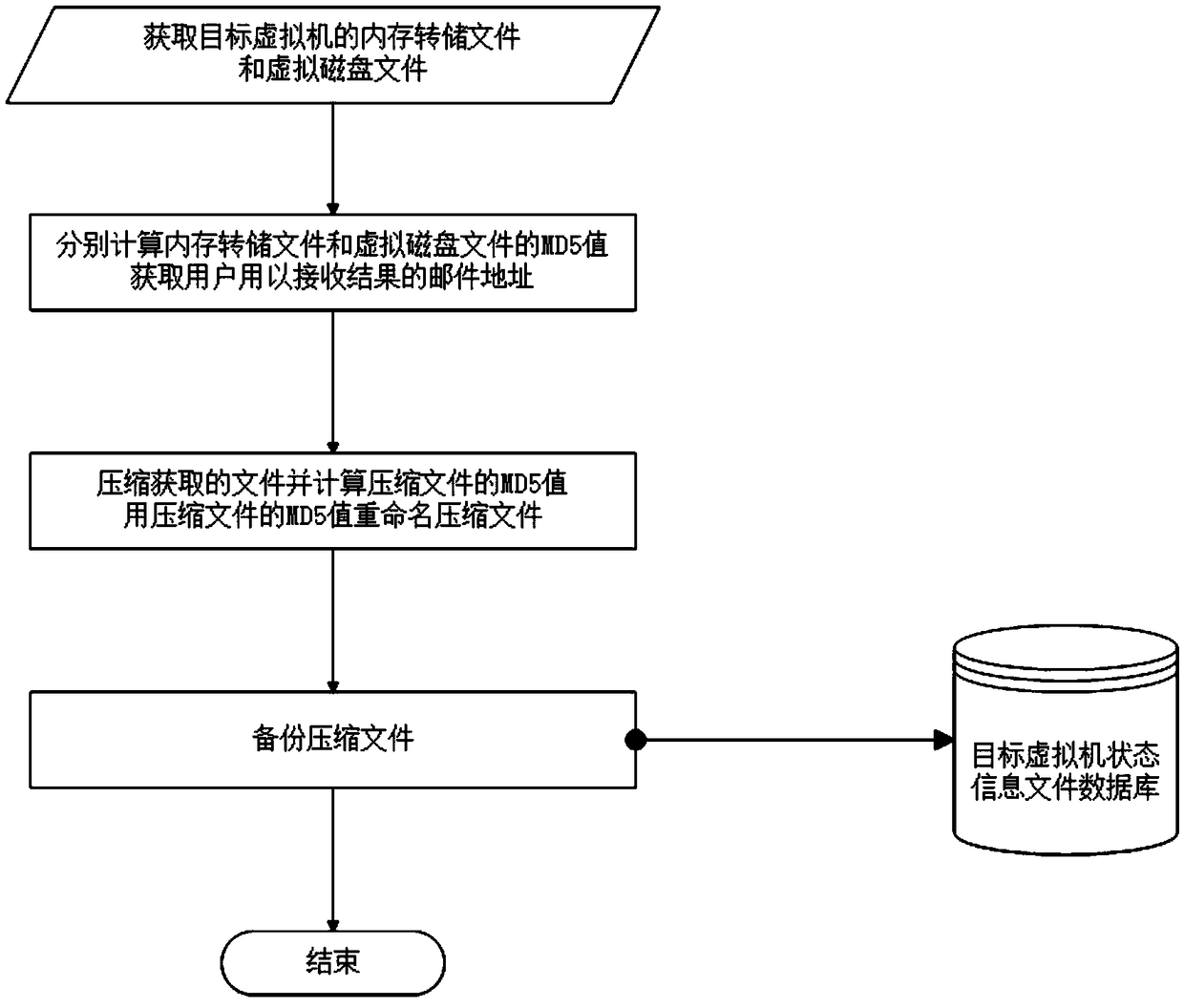
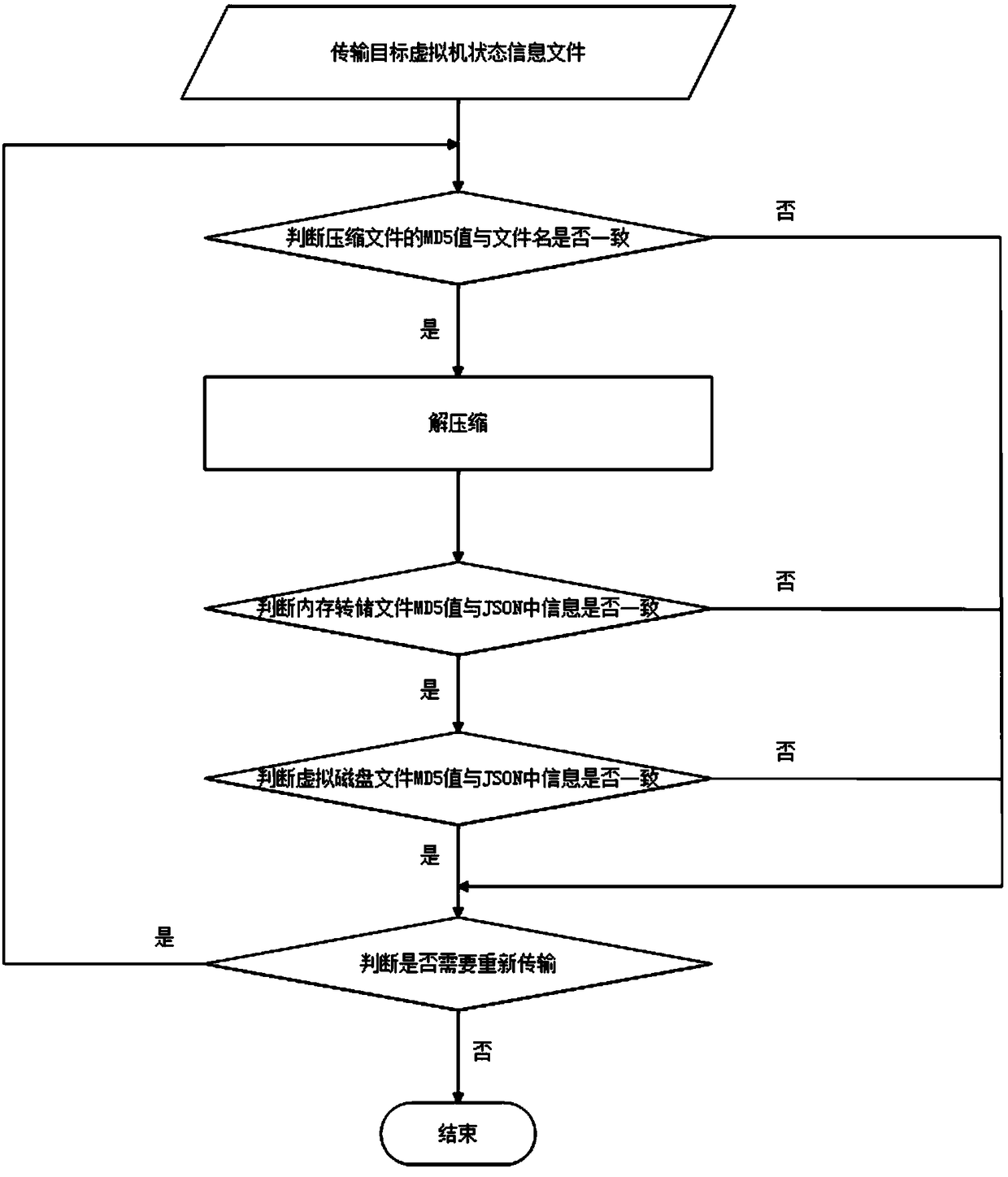
[0085] see Figure 1 to Figure 4 , a server forensics method based on virtual machine introspection, the specific steps are as follows:
[0086] S1. Obtain the status information of the customer virtual machine, store the compressed file of the status information in the database and send it to a third party for forensic analysis;
[0087] S2. Perform forensic analysis on the target virtual machine state information file transmitted by the cloud computing provider;
[0088] S3. Issue a standardized test report and give feedback on the test results.
[0089] Wherein, step S1 utilizes the privileged attributes and built-in functions of the virtual machine monitor to perform a memory dump of the memory of the target virtual machine to generate a memory dump ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com