An application deployment method, its deployment device and edge data center
A technology for deploying devices and receiving users, which is applied in the computer field, can solve problems such as low security level, and achieve the effect of strong isolation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
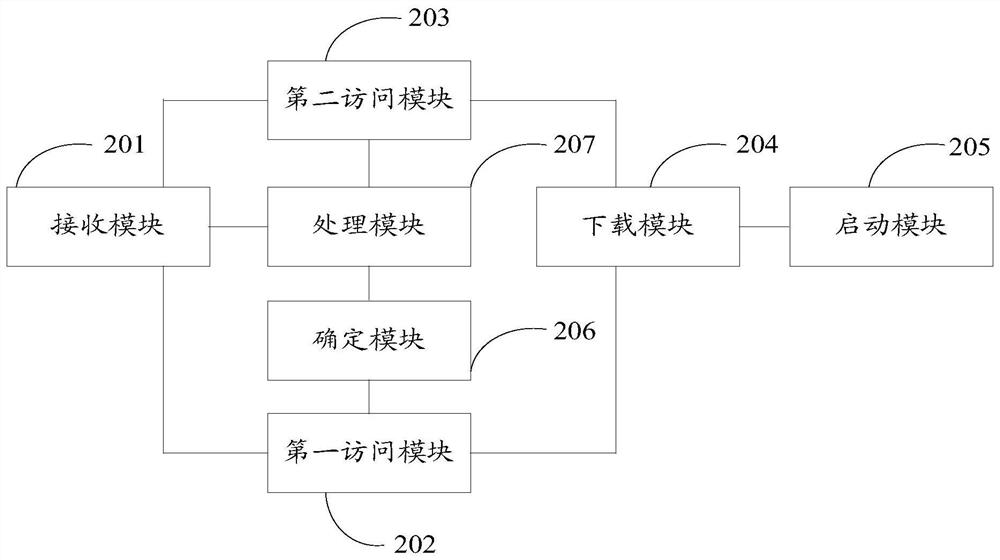
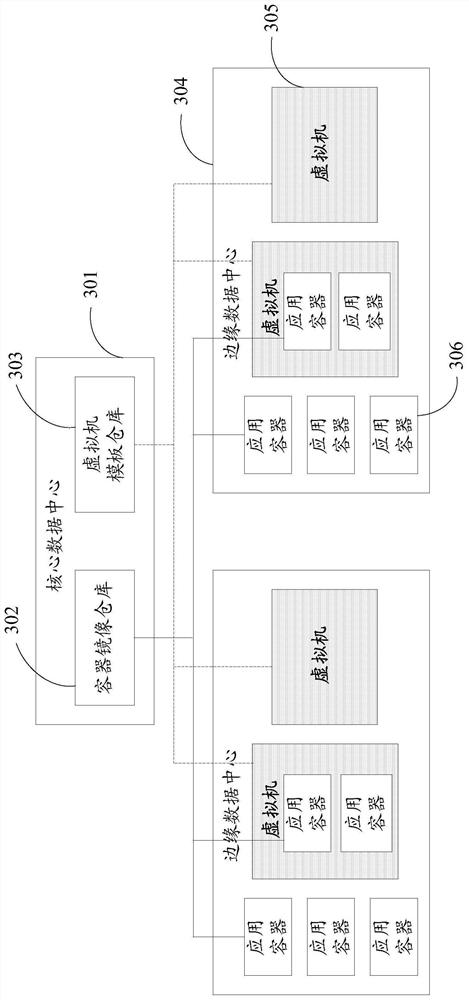
Image
Examples
Embodiment 1
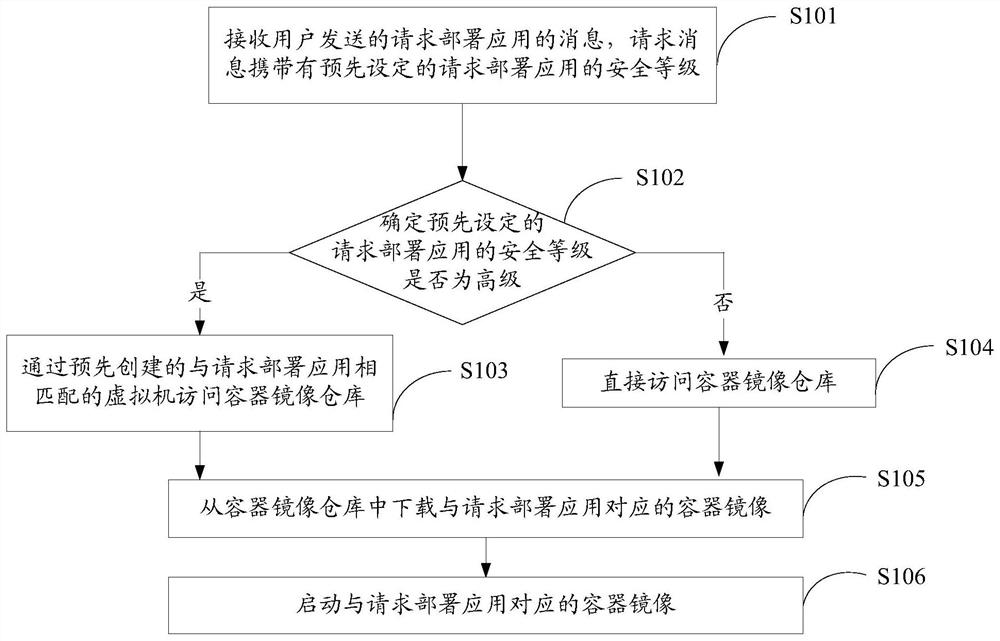
[0089] Example 1: Combining Figure 4 The flow chart of the application deployment method is shown, taking the deployment of an application as an example.
[0090] S401. Receive a message requesting deployment of an application sent by a user;
[0091] S402. Analyzing and processing the received request message;
[0092] S403. According to the result of the analysis and processing, determine whether the preset security level of the requested deployment application is high; if yes, execute step S404; if not, execute step S410;
[0093] S404. Determine whether there is a created virtual machine; if yes, execute step S405; if not, execute step S407;
[0094] S405. Determine whether the nature of the created virtual machine matches the nature of the requested deployment application; if yes, execute step S406; if not, execute step S407;
[0095] S406. Determine that there is no need to create a virtual machine that matches the requested deployment application; execute step S409;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com