Method for encrypting bit-level synchronous promiscuous diffusion images and pixel-level annular diffusion images
An encryption method, a pixel-level technology, applied in the field of image processing, which can solve the problems of low plaintext sensitivity of encryption method and weak ability to resist differential attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
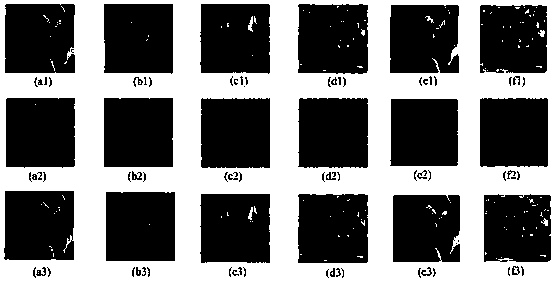
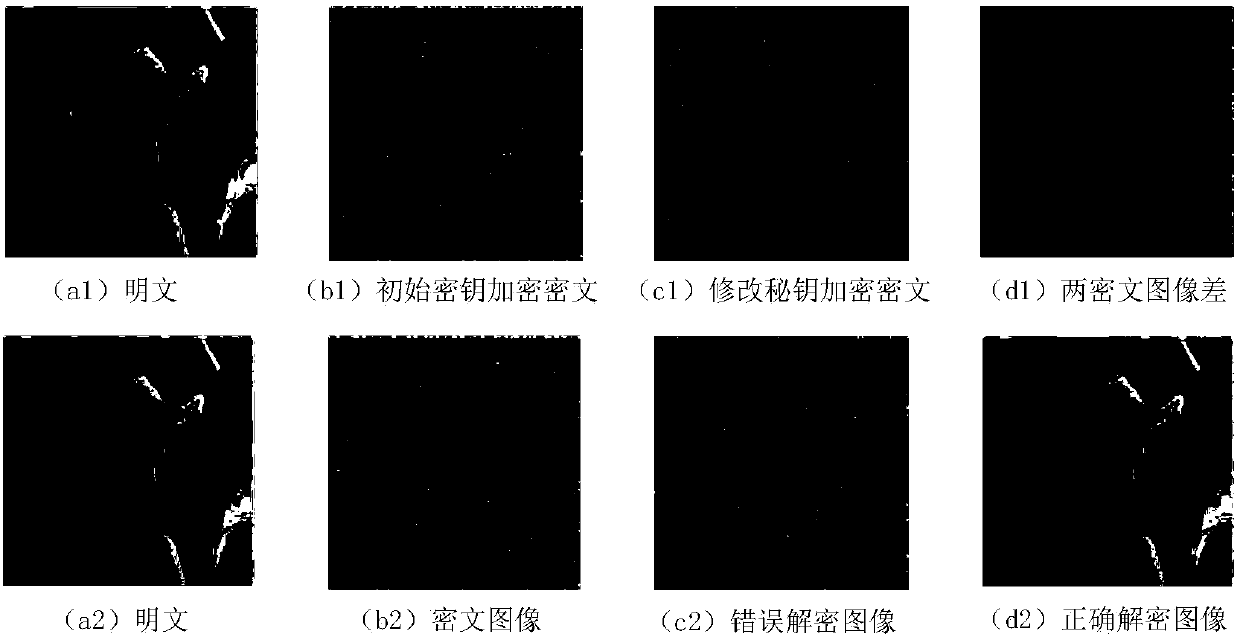
[0055] On a desktop computer with Intel(R) core(TM) i5-2400@3.10GHz and 4GB memory, based on the MATLABR2013a platform, four grayscale standard test images of Lena, Baboon, Couple and Peppers with a size of 256×256 and Lena , Peppers 2 color standard test images for encryption simulation experiments.
[0056] Take the Lena image with a size of 256×256 as an example, and set the key to [μ 1 , l 1 ,μ 2 , l 2 ]=[0.0123, 0.1234, 0.2345, 0.0234], explaining the specific encryption steps.
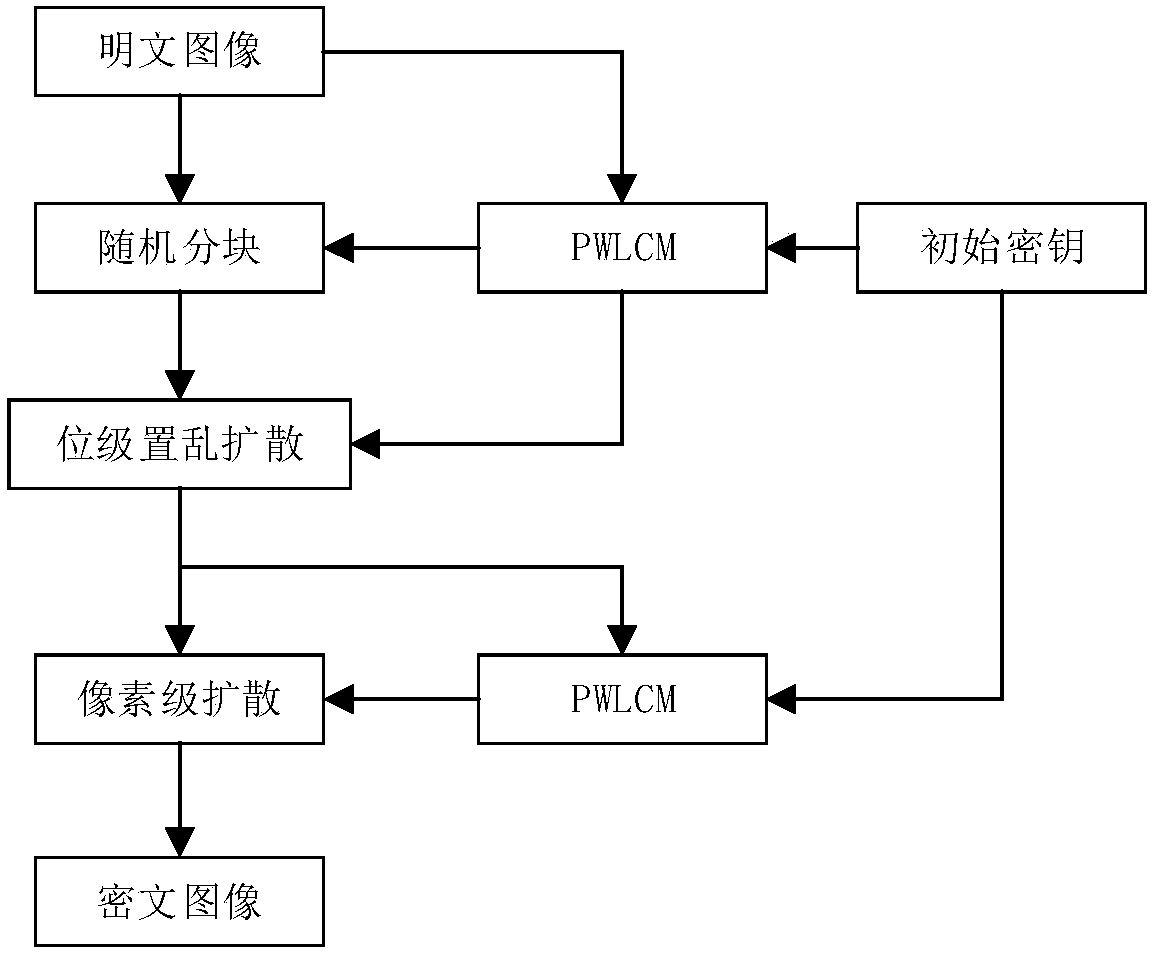
[0057] Step 1: Plaintext Image Preprocessing
[0058] 1) Convert the pixel matrix of the plaintext image Lena into a one-dimensional vector P={136, 136, 137, 132, ...} in the order of raster scanning. Given that M=N=256, calculate Therefore, M×N=S×S, no image reshaping is required.
[0059] 2) With Lena image pixel sum(I)=6401503, pixel XOR value xor(I)=3 as perturbation factor, perturb initial key μ according to formula (1) 1 , calculate μ 1 '=0.3027.
[0060] 3) Let the initial value...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com