Improved SIM card and mobile communication identification method and system
A technology of identity recognition and mobile communication, applied in the field of mobile communication, can solve the problem of cracking SIM card confidential communication, etc., and achieve the effect of preventing the risk of being cracked and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
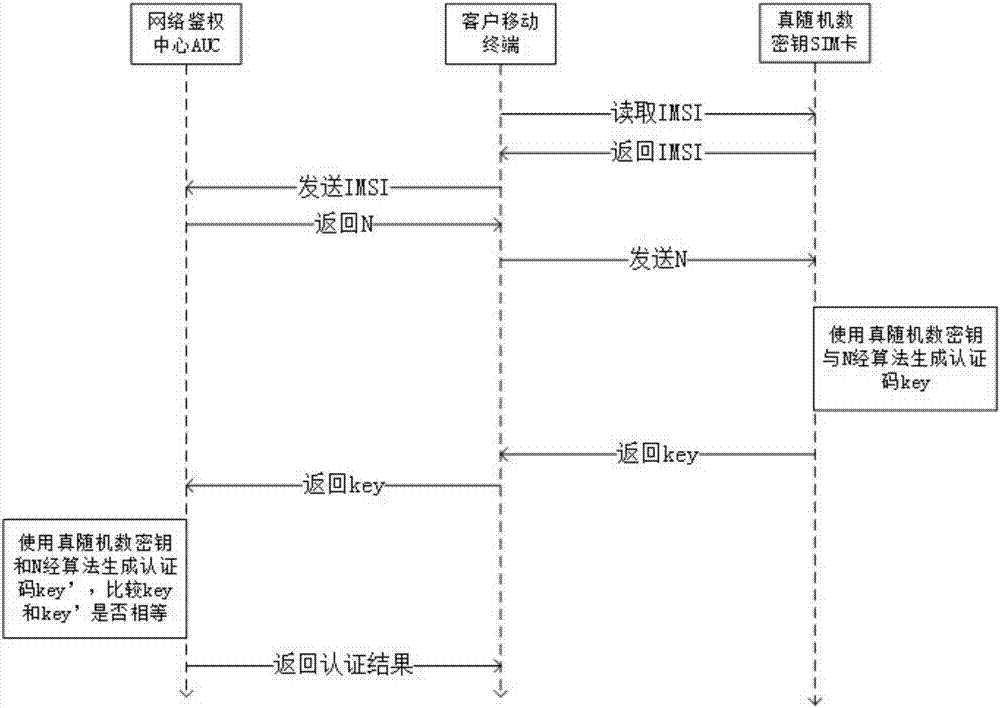
[0054] In the mobile communication identification system based on the improved SIM card in this embodiment, when the customer goes to the mobile communication network to handle network access, the customer is assigned a customer telephone number (MSISDN), an International Mobile Subscriber Identity (IMSI) and a SIM Card. Write the IMSI and other customer information such as various cryptographic algorithms into the customer's SIM card through the card writer.
[0055] A key issuing server is set in the mobile communication network, and a true random number generator is set in the key issuing server, and a specified number of true random number keys are taken out from the true random number generated by the true random number generator. The number key is the true random number key issued this time. And write this true random number key in the SIM card of the customer. The true random number key is directly stored in the SIM card in the form of plain text, and cannot be taken ...
Embodiment 2
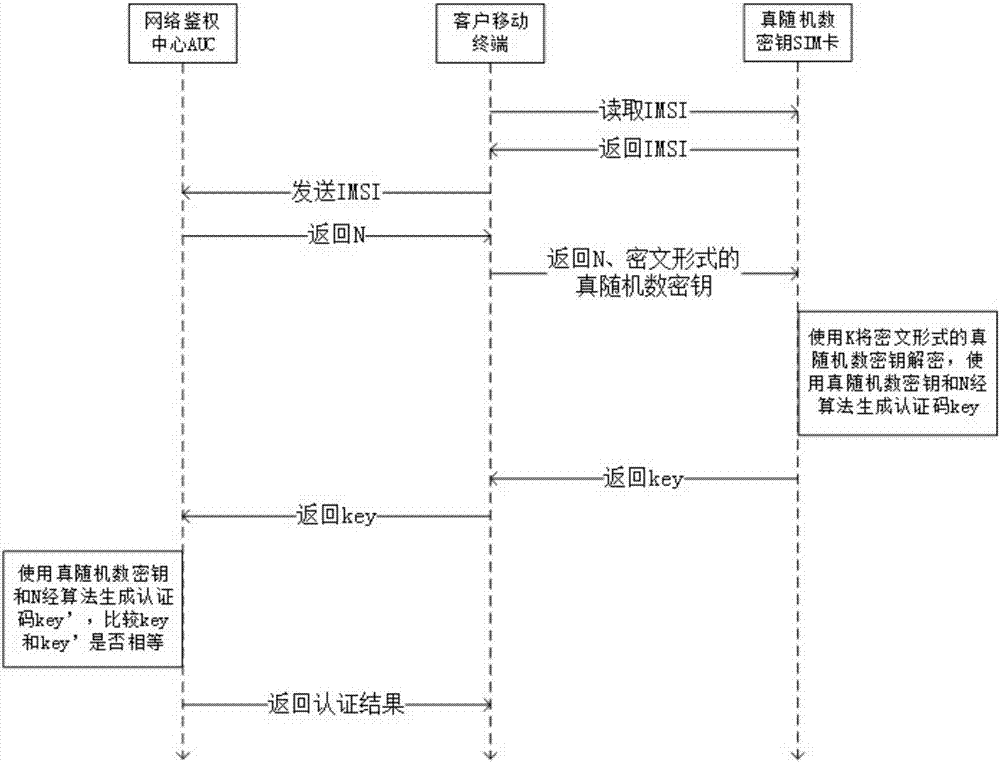
[0066] With respect to embodiment 1, the inside of the SIM card in this embodiment is provided with a true random number generator chip, and after the SIM card receives the true random number key from the mobile communication network, it generates A true random number encryption key K, and use the true random number encryption key K to encrypt the true random number key into a true random number key in ciphertext form. The true random number key in the form of cipher text can be stored in the memory of the mobile terminal or the extended storage area of the mobile terminal can also be stored in the data storage area in the SIM card. At the same time, the true random number encryption key K will be saved in the SIM card for use in decryption.
[0067] The following will give the authentication process of the mobile communication network to the client SIM card according to the traditional authentication method, and the authentication process of the client SIM card to the mobil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com