A vulnerability analysis method based on implicit taint propagation
A technology of taint propagation and vulnerability analysis, which is applied in the field of network security, can solve problems such as failure to achieve analysis results and interruption of the analysis process, and achieve high accuracy and good analysis capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to make the above-mentioned features and advantages of the present invention more comprehensible, the following specific embodiments are described in detail in conjunction with the accompanying drawings.
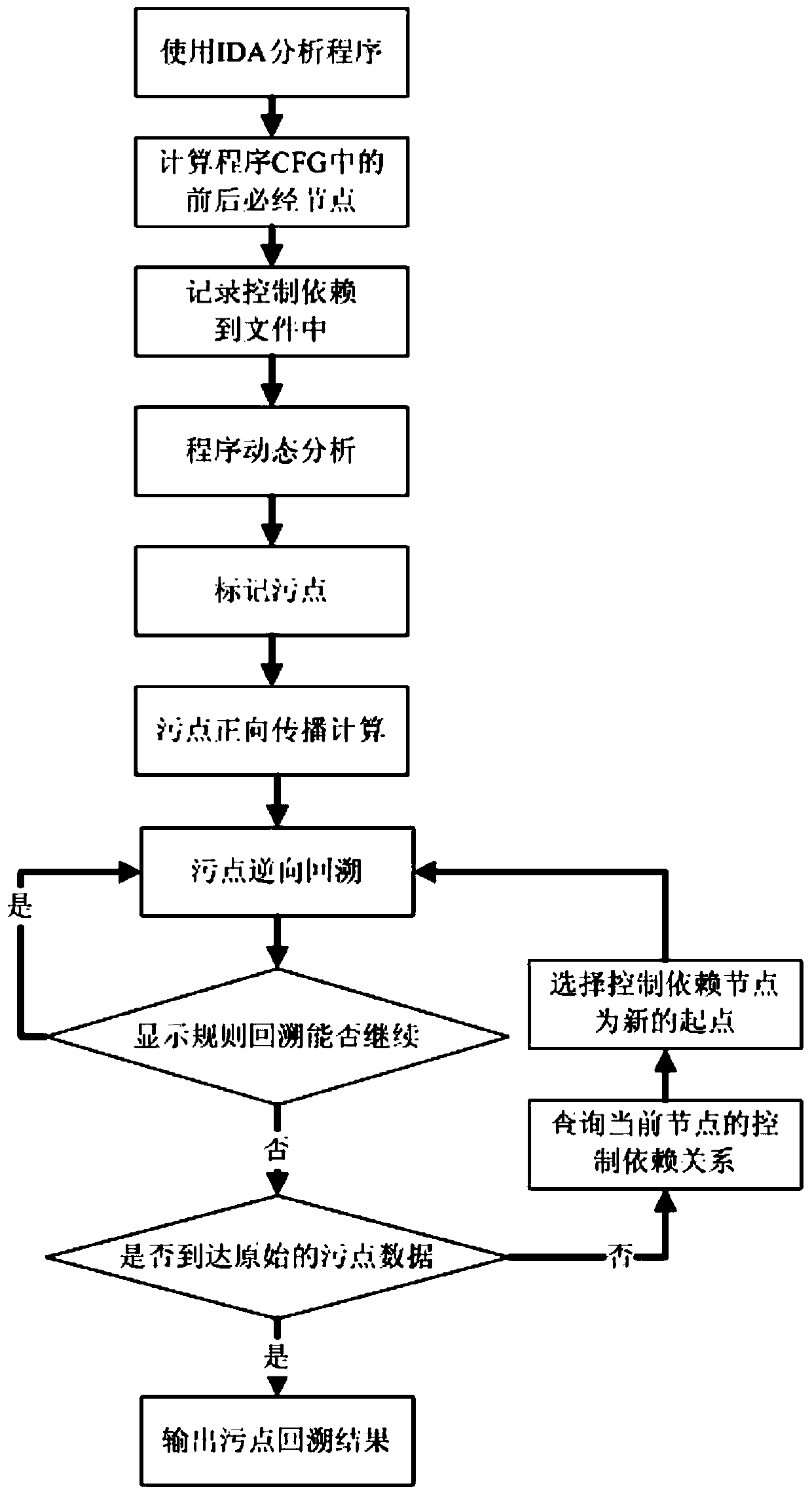
[0033] The present invention provides a vulnerability analysis method based on implicit taint propagation, the flow chart of which is as follows figure 1 shown, including the following steps:
[0034] 1) Use IDA Pro to statically analyze the program to be analyzed to obtain the control flow graph of the program, calculate the control dependency of each instruction in the control flow graph, and store the control dependency in a disk file; The file format can be customized by the user, and it only needs to accurately describe the control dependency.
[0035] The present invention adopts the method of writing IDA Pro plug-in, starts from the entry point of the software executable program, firstly constructs the control flow graph of the program, and there is a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com