A file encryption and decryption method and device
A file encryption and file technology, applied in the field of information security, can solve problems such as high consumption of terminal systems, inability to strictly distinguish file sensitivity, waste of terminal system resources, etc., and achieve the effect of narrowing the scope of monitoring
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0043] This embodiment will be described from the perspective of an encryption device. Specifically, the encryption device may be integrated in a terminal or other devices that need to encrypt files.
[0044] There are many ways that the encryption device is integrated on the terminal, for example, it is installed in the terminal in the form of a client or other software.
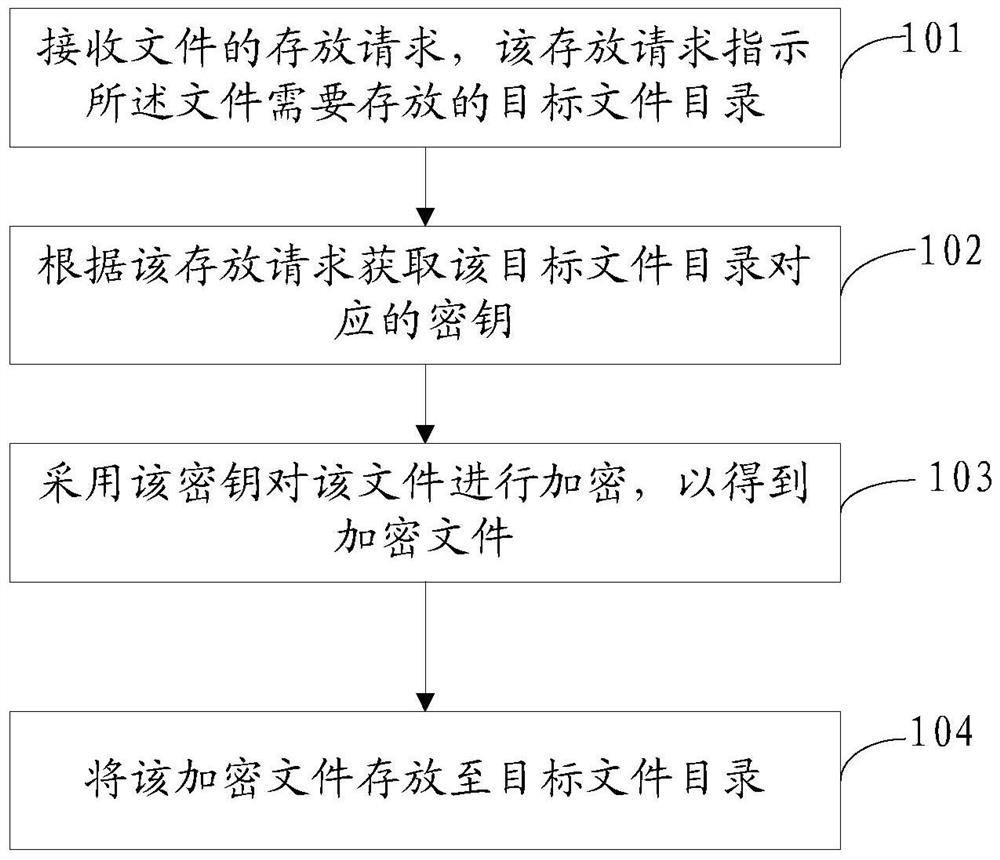
[0045] A file encryption method, characterized in that it includes: receiving a storage request for a file, the storage request indicating a target file directory where the file needs to be stored, obtaining a key corresponding to the target file directory according to the storage request, and using the key The file is encrypted to obtain an encrypted file, and the encrypted file is stored in the target file directory.
[0046] Such as figure 1 As shown, the specific process of this file encryption can be as follows:
[0047] 101. Receive a file storage request, where the storage request indicates a targe...
Embodiment 2
[0092] Correspondingly, this embodiment provides a file decryption method. This embodiment will describe the method from the perspective of a decryption device. The decryption device may be integrated into a terminal or other devices that need to decrypt files.
[0093] There are many ways that the decryption device is integrated on the terminal, for example, it is installed in the terminal in the form of a client or other software.
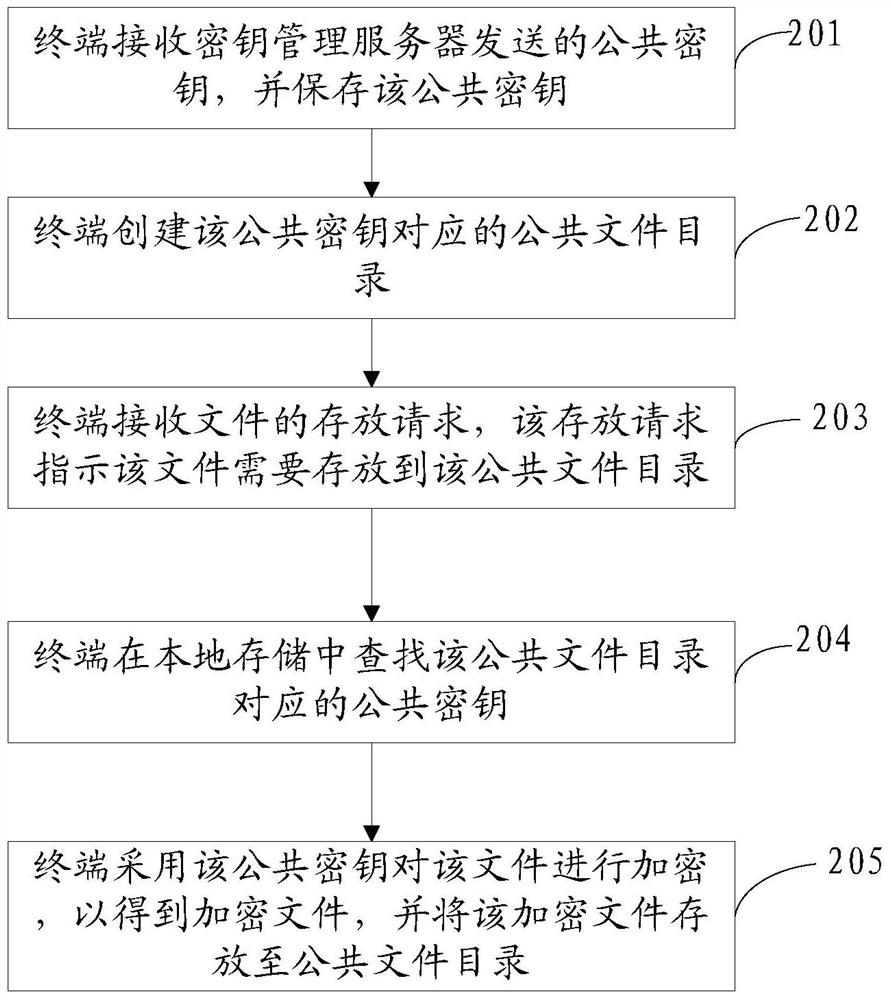
[0094] Such as Figure 4 As shown, the specific flow of the file encryption method can be as follows:
[0095] 401. Receive a read request of an encrypted file, where the read request carries encryption attribute information corresponding to the encrypted file.
[0096] The decryption device can be integrated in the encryption terminal that forms the encrypted file, for example, the terminal that encrypts the file to form the encrypted file using the method described in Embodiment 1, or it can also be integrated in other non-encrypted terminals,...
Embodiment 3
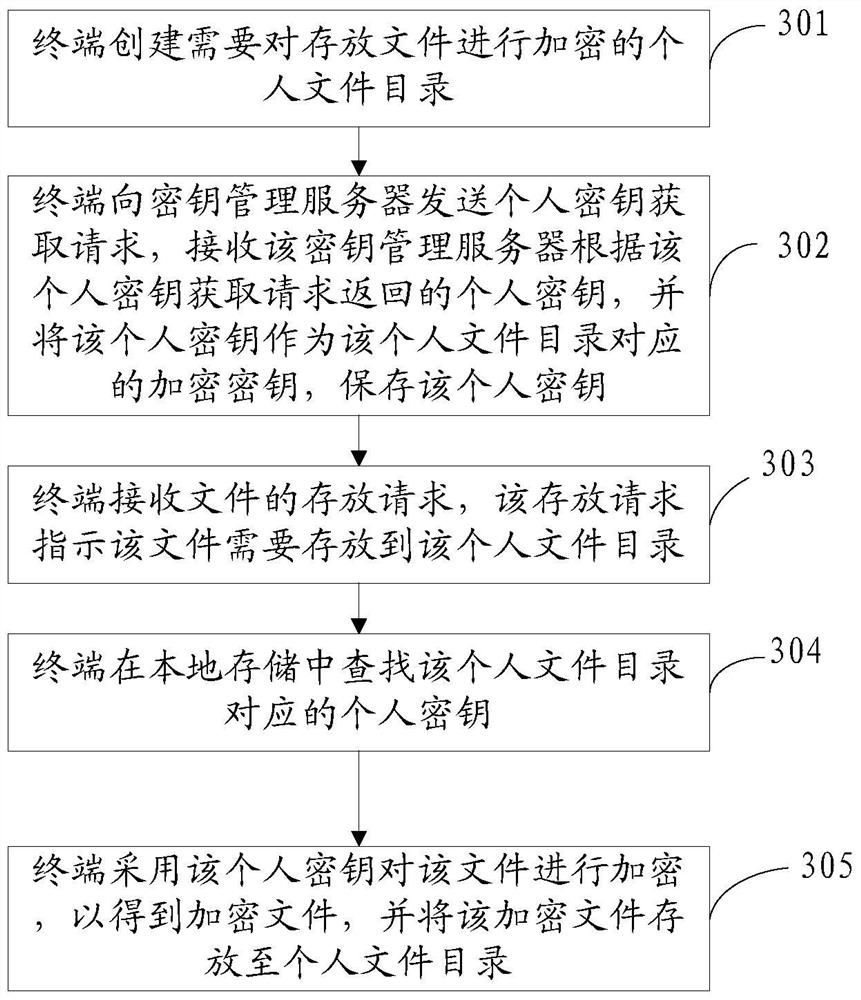
[0137] In order to better implement the above method, the embodiment of the present invention also provides a file encryption device, such as Figure 7a As shown, the identity verification device may also include a receiving module 701, a key acquisition module 702, an encryption module 703 and a storage module 704, as follows:
[0138] The receiving module 701 is configured to receive a storage request of a file, and the storage request indicates a target file directory where the file needs to be stored;
[0139] A key acquisition module 702, configured to acquire the key corresponding to the target file directory according to the storage request;
[0140] An encryption module 703, configured to encrypt the file using the key to obtain an encrypted file;
[0141] The storage module 704 is configured to store the encrypted file in the target file directory.
[0142] For example, refer to Figure 7b , the implementation of the file encryption device can also include a creation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com