Non-intrusive PLC abnormality detection method based on power consumption analysis
A technology of power consumption analysis and anomaly detection, applied in the identification of patterns in signals, measuring devices, measuring electrical power, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Further illustrate the present invention below in conjunction with accompanying drawing.
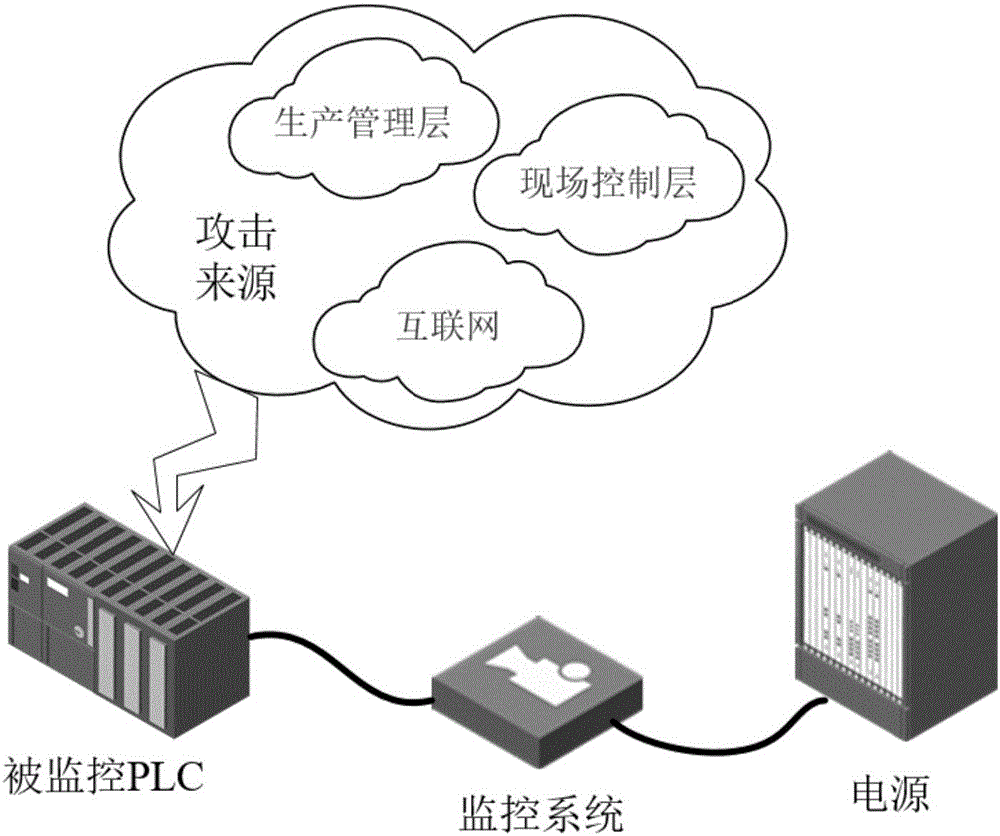
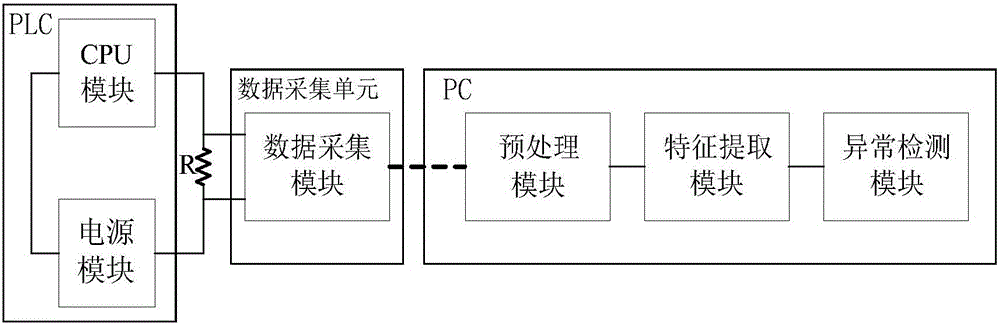
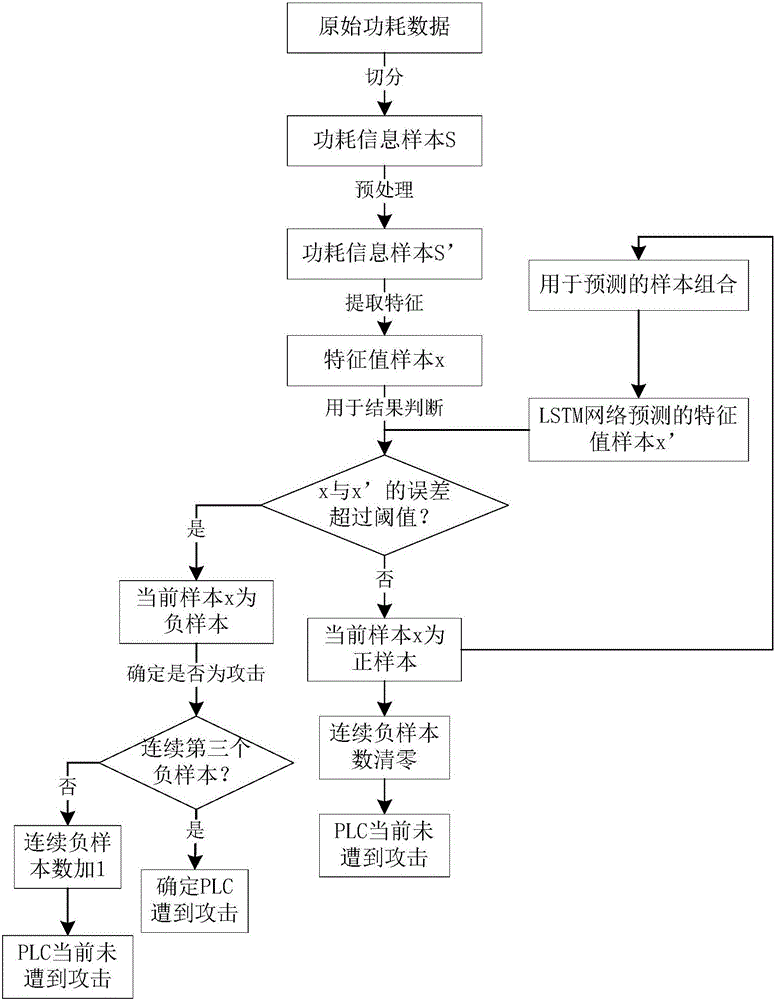
[0044] Such as figure 1 As shown, PLC, as a key device in the industrial control system, will face various attacks. These attacks may come directly from the production management layer and field control layer, and may also come from the Internet. These attacks will obtain the control authority of the PLC, and then let the PLC run some malicious instructions, thereby destroying the control process on the site. While the anomaly detection system we proposed does not change the software and hardware structure of the PLC itself, a small 0.1 ohm resistor is connected to its power supply end. The connection of this resistor will neither affect the operation of the PLC nor give it pose potential risks. The anomaly detection system works by transmitting the voltage drop across the resistor to the host computer, so the entire anomaly detection system is equivalent to operating independen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com