Method and device for scanning plug-in and determining rule scheduling sequence in plug-in
A scheduling sequence and rule technology, applied in the field of Internet security, can solve the problems of low overall scanning performance of vulnerability scanners, waste of time and computer resources, and reduce scanning speed and efficiency, so as to improve the overall scanning performance, improve scanning speed and efficiency , the effect of saving computer resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings. Obviously, the described embodiments are only some embodiments of the present invention, rather than all embodiments . Based on the embodiments of the present invention, all other embodiments obtained by persons of ordinary skill in the art without making creative efforts belong to the protection scope of the present invention.
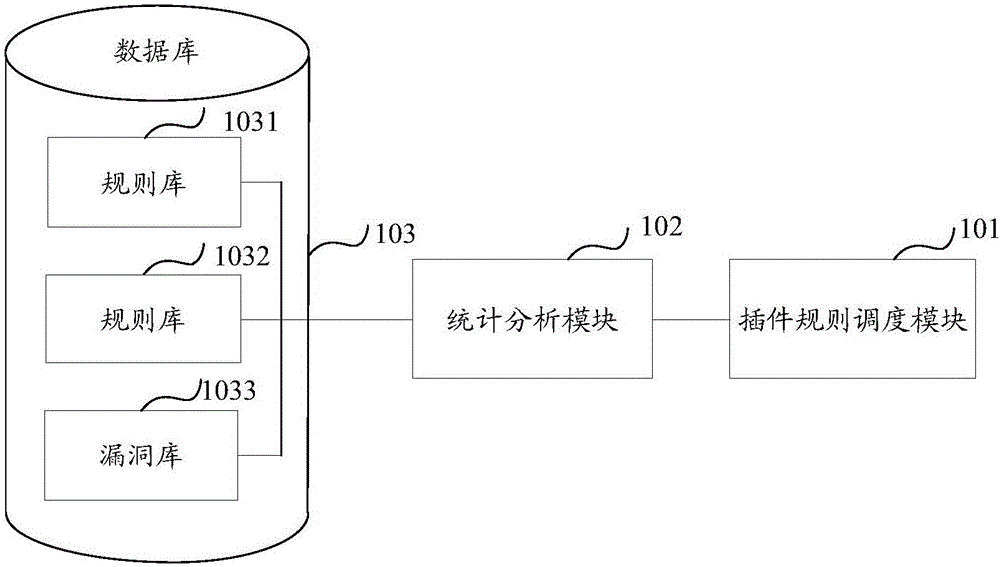
[0060] An embodiment of the present invention provides a vulnerability scanning system, such as figure 1 As shown, it is a schematic structural diagram of a vulnerability scanning system provided by an embodiment of the present invention, including: a plug-in rule scheduling module 101 , a statistical analysis module 102 , and a database 103 . Wherein, the database 103 includes a rule base 1031 , a plug-in base 1032 , and a vulnerability b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com