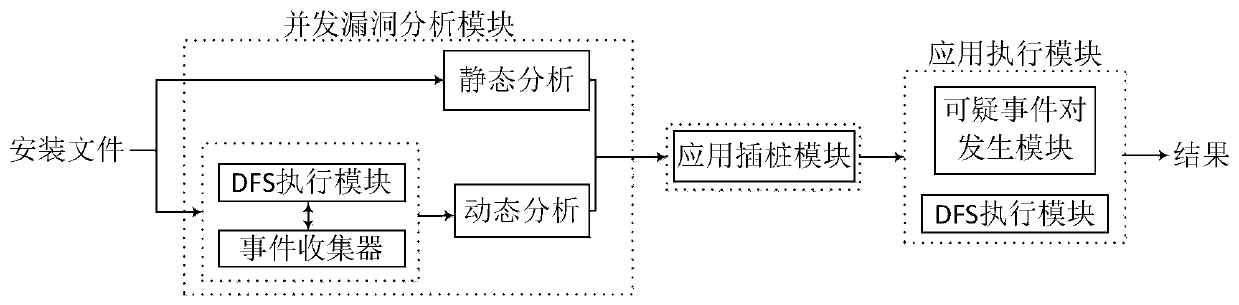
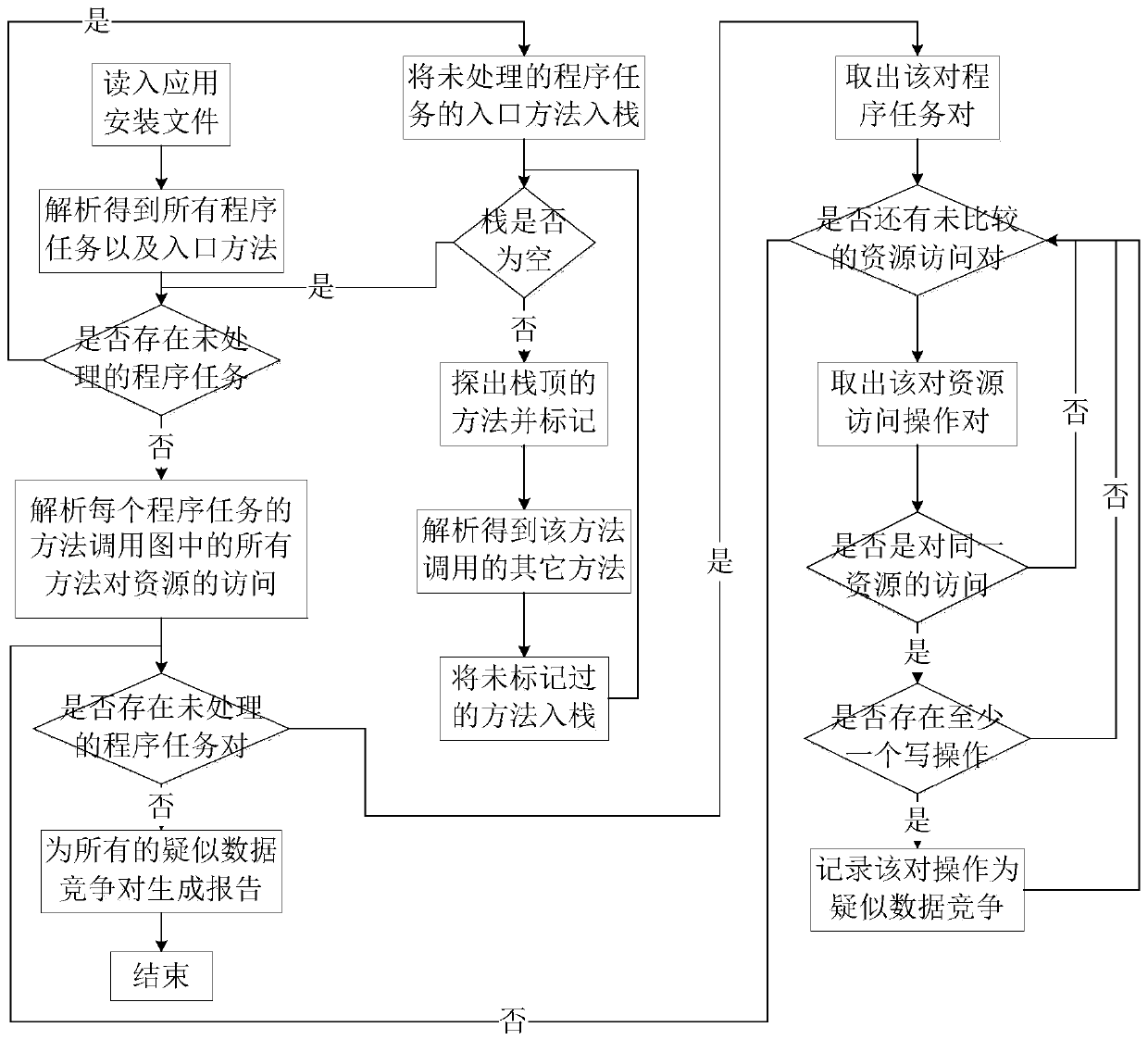
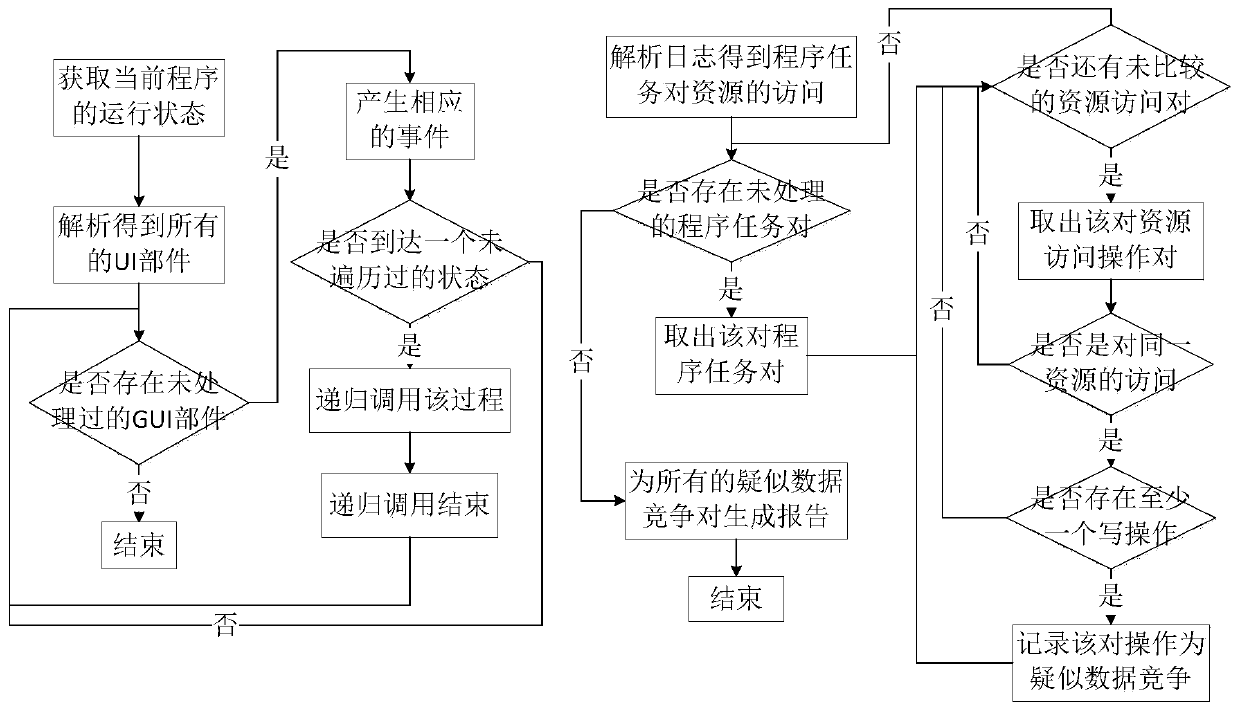
An Android application concurrency vulnerability detection system
A vulnerability detection and Android technology, applied in computer security devices, instruments, computing, etc., can solve the problems of high false positive detection results and undetectable concurrent vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to describe the invention more clearly, first, some terms are explained.
[0026] An Android application refers to an application that can be installed and run on an Android mobile device, and specifically refers to the resource file and bytecode file of the application when it is clearly operated.
[0027] A Java application refers to an application written in the Java language that can run on a computer equipped with a JVM.
[0028] The bytecode of an Android application is the essence of an Android application. It consists of several class files, and each of these classes contains several methods. The methods in these classes cooperate to achieve specific functions.
[0029] The Android virtual machine refers to the executor of the Android application runtime. It is a special JVM that is specially used to interpret and execute the bytecode instructions of the Android application.
[0030] The Android application GUI component refers to the part that can be ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com