DCR-based dynamic vulnerability detection method and system
A vulnerability mining and dynamic technology, applied in the direction of instrumentation, electronic digital data processing, platform integrity maintenance, etc., can solve the problems of high algorithm complexity, time-consuming, large amount of calculation, etc., achieve parallelization and automation, increase effective Sexuality and efficiency-enhancing effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
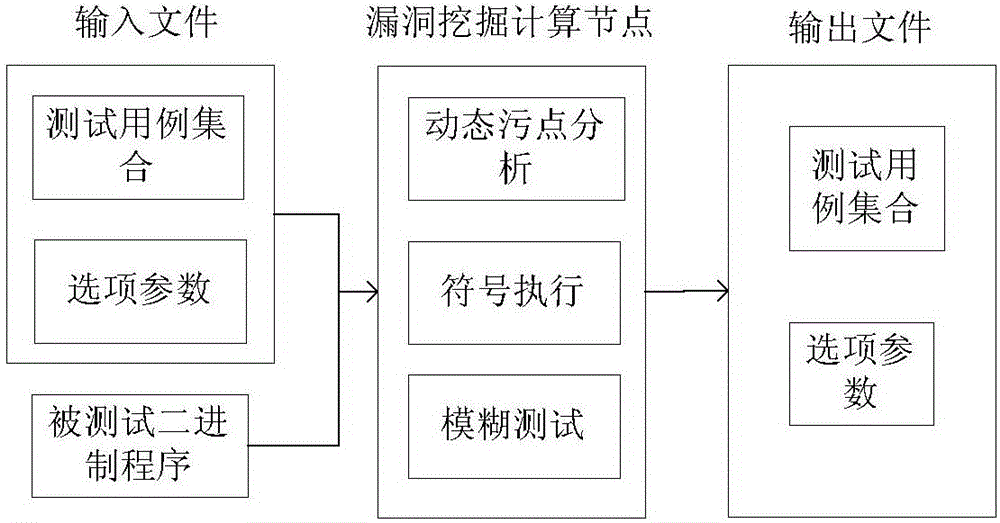
[0043] Combining dynamic vulnerability mining technology with DCR parallel computing technology, it is first necessary to analyze the characteristics of dynamic vulnerability mining, and then extract functional modules that can be parallelized, that is, design a vulnerability mining calculation model, and extract a test execution process. The dynamic vulnerability mining system is implemented by combining three methods: dynamic taint analysis, symbolic execution and fuzz testing. By using dynamic taint analysis, the execution path of the input data in the program under test is obtained, and then the path is symbolized and the execution path is extracted using symbolic execution technology. Constraints in , solve and calculate the set of constraints and generate new test cases. The newly generated test cases are re-passed as input ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com