Proxy blind signature-based anti-scalping sensitive data transaction method
A technology of sensitive data and transaction methods, applied in the field of cryptography, can solve problems such as harming the interests of data providers, and achieve the effects of avoiding data supervision risks, ensuring fairness, and preventing second-hand reselling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be described in further detail below in conjunction with accompanying drawing, but not as any restriction to the present invention
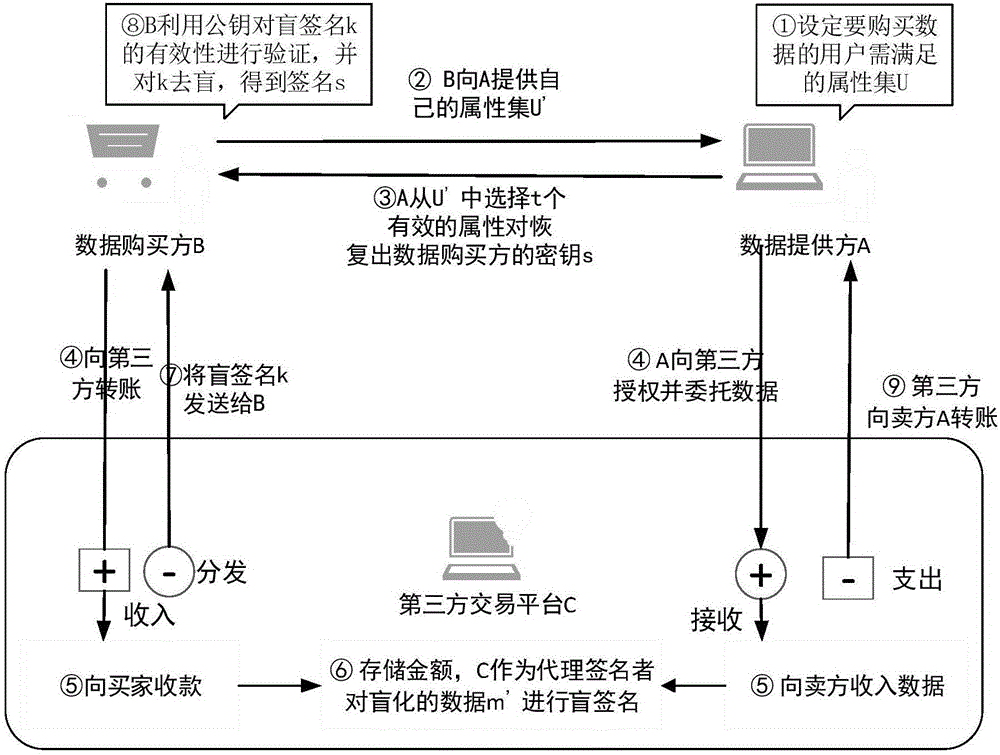
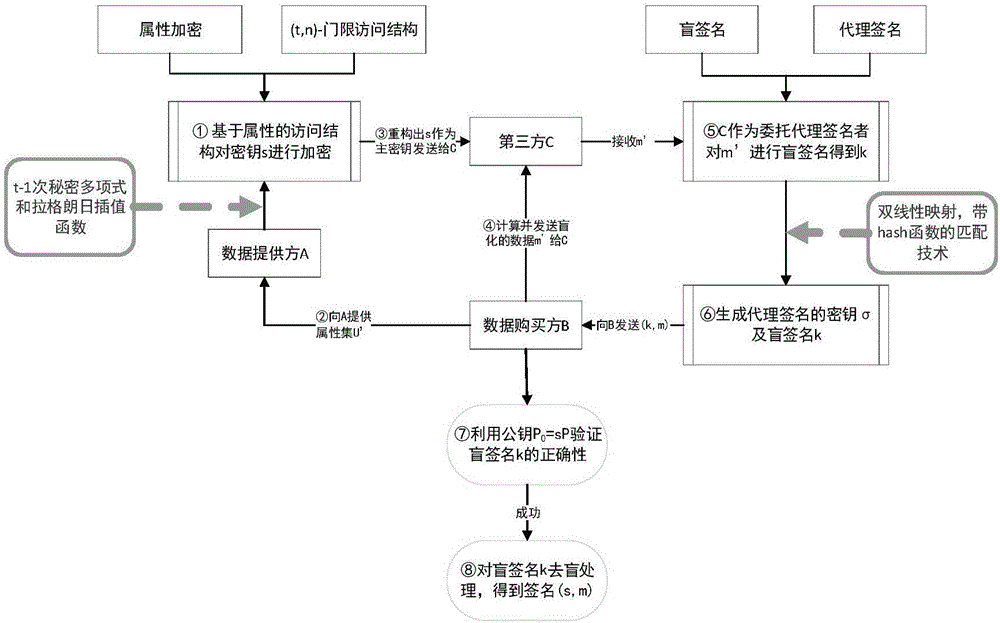
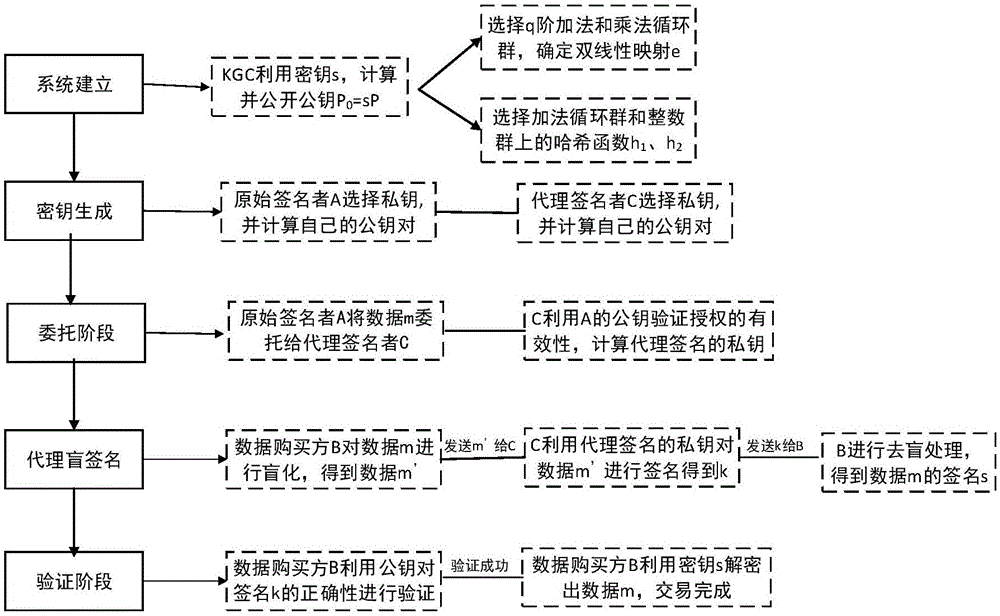
[0043] Embodiment of the present invention: anti-reselling sensitive data transaction method based on proxy blind signature, the system members in this embodiment include data provider A (original signer), data buyer set B, third party C (i.e. proxy signature or), the data to be traded is m, and the IDs of A and C are respectively recorded as ID A and ID C ; Let G 1 , G 2 respectively represent the q-order additive cyclic group and the q-factorial cyclic group, where q is a large prime number. Select the group G using a suitable public key procedure 1 generator P of , and assume that in the group G 1 , G 2 There is a bilinear map e:G between 1 ×G 1 →G 2 ; In addition, there is a hash function h 1 :{0,1} * →G 1 , The specific content of each step will be described in detail below:
[0044] It is div...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com