SQL loophole detecting method based on artificial neuron network
A neural network and vulnerability detection technology, applied in the field of computer software, can solve problems such as poor time response, long time, and poor classification performance, so as to reduce detection time, reduce false alarm rate, and facilitate debugging and the modified effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
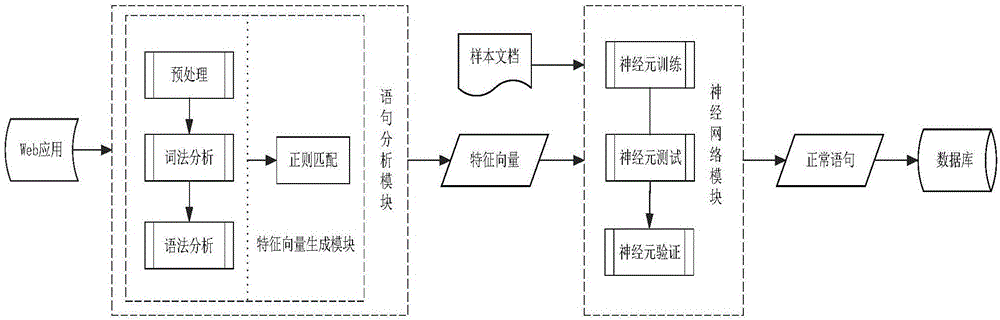
[0031] The system is composed of two parts: SQL statement analysis module and artificial neural network module. System architecture such as figure 1 shown.
[0032] SQL statement analysis module
[0033] The main function of the SQL statement analysis module is to convert the SQL statement submitted by the Web application into a feature vector group r, where r is a feature vector composed of 0 and 1. By classifying SQL injection attack statements, this module designs r to consist of 12 r i Composition, i represents the number. if r i =1, it means that the SQL statement contains keywords; if r i =0, it means that the SQL statement does not contain a certain keyword. If C represents whether a statement is a SQL injection statement, and defines: if the statement is a SQL injection statement, the value of C is 1, and if the statement is not an SQL injection attack statement, the value of C is 0. In this way, each SQL query statement can be represented by feature vectors r a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com