An AES Algorithm-Oriented Anti-Power Attack Method Based on Random Delay
A random delay and anti-power consumption technology, applied in countermeasures against encryption mechanisms, encryption devices with shift registers/memory, digital transmission systems, etc., can solve the problem of large impact on performance and hardware resource overhead, high implementation cost, Solve problems such as cumbersome solutions, achieve low cost of anti-attack, good anti-attack effect, and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The technical solution of the present invention will be further introduced below in combination with specific embodiments.
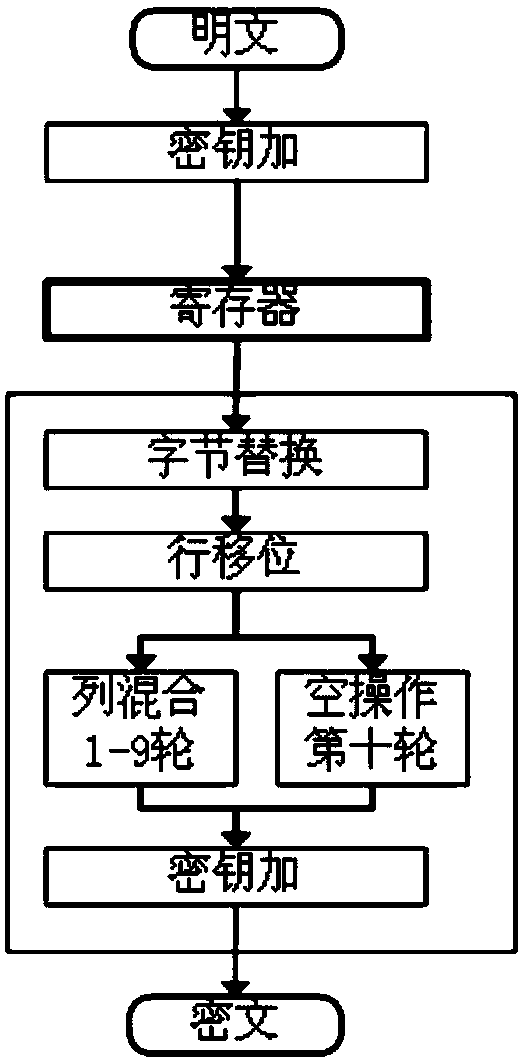
[0022] The traditional AES algorithm consists of 3 parts, which are the initial key addition, 9 rounds of the same round operation, and the 10th round of final transformation. Each round requires a round key to complete the key addition operation, and there are eleven subkeys in total, denoted as Kn (n=0,...,10). The subkey is obtained by expanding the initial key. The 9-cycle round operation in the middle of the AES algorithm includes four operations: byte replacement, row shift, column mixing, and key addition. The transformation at the end of the tenth round includes three operations: byte replacement, row shift and key addition. AES will generate an intermediate value data at the end of each round, which can be recorded as Dn (n=0,...,10) and stored in the register, where D10 is the ciphertext output.
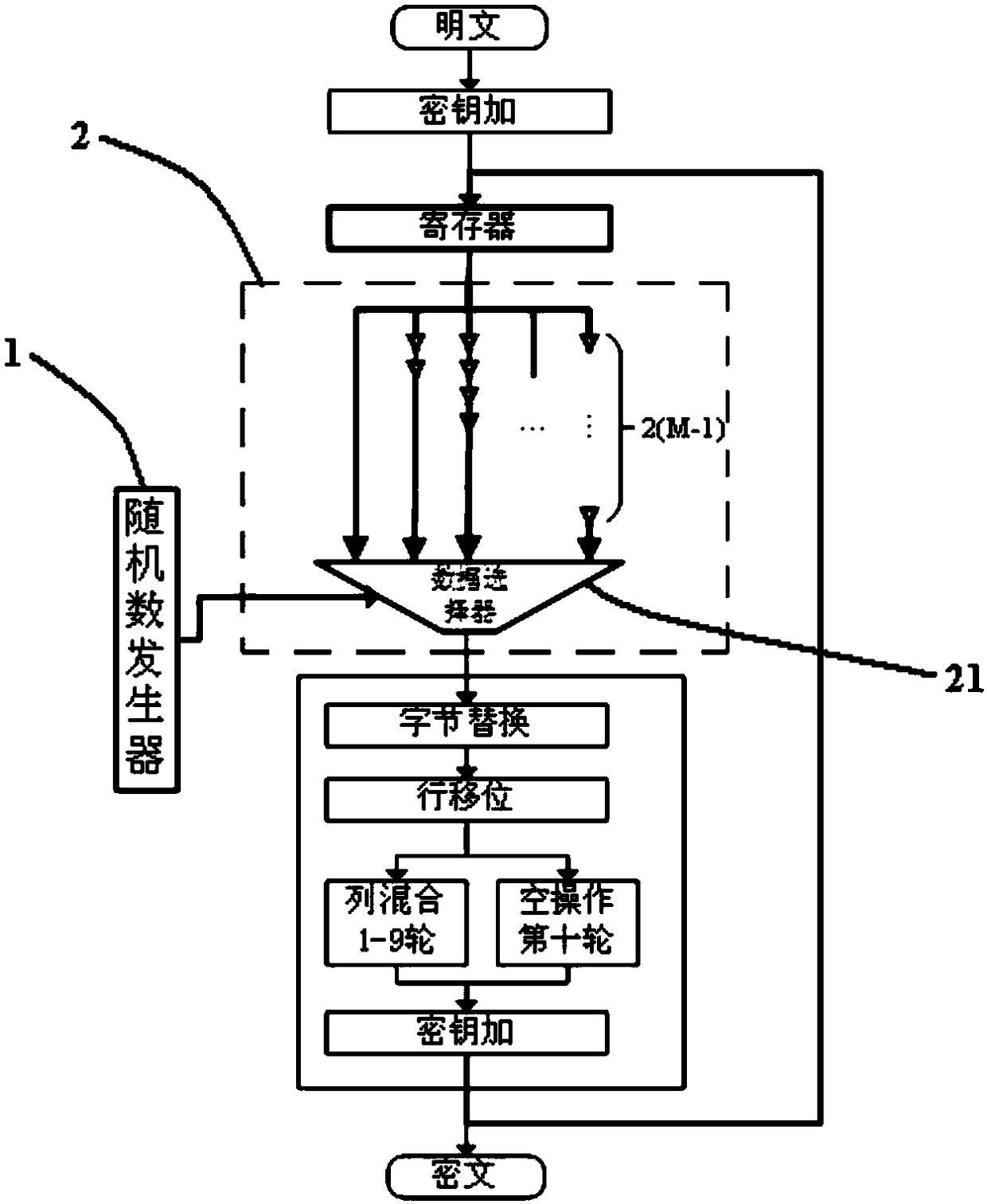
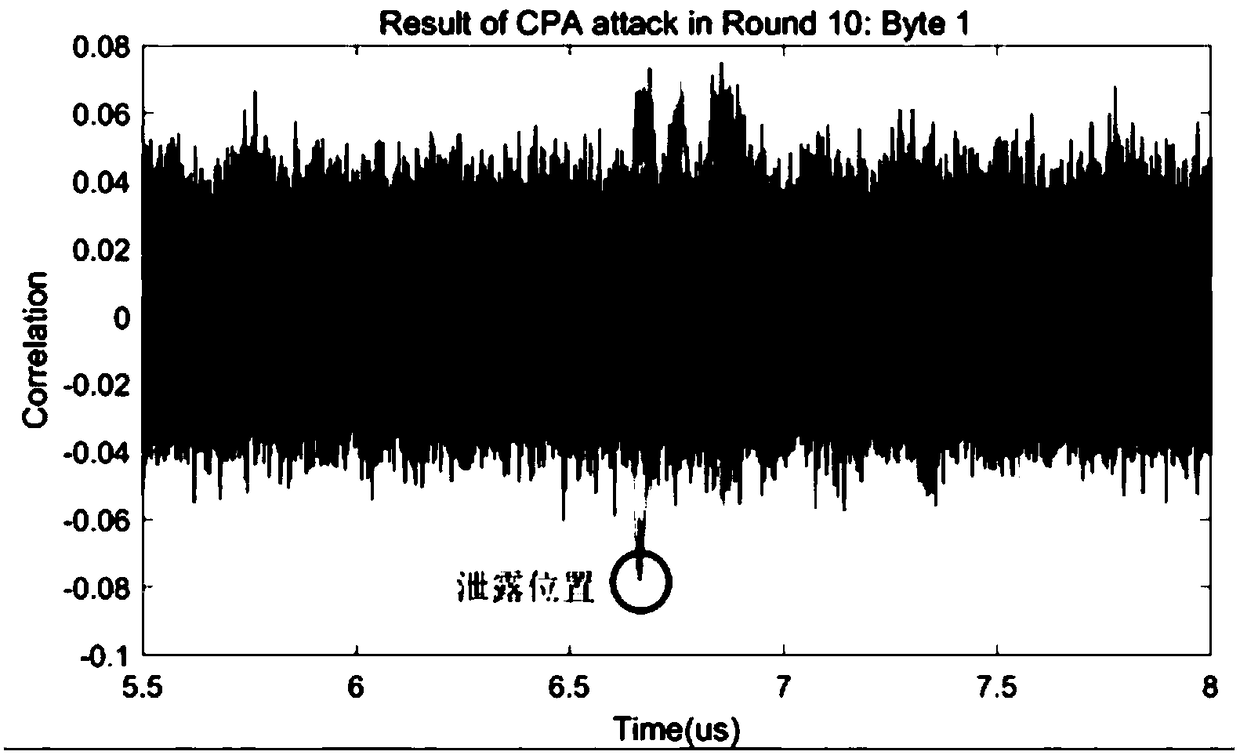
[0023] Such as figure 1 As shown, ta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com