File protection method and system
A file and file header technology, applied in the fields of digital data protection, instruments, computing, etc., can solve the problems of long time, easy to be leaked, and low security of sensitive files.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] Below in conjunction with accompanying drawing, further describe the present invention through embodiment, but do not limit the scope of the present invention in any way.
[0069] The present invention provides a file protection method and system, which provide real-time security protection for files in any format by managing users, monitoring files, generating file keys in layers and a file management method based on a security directory.
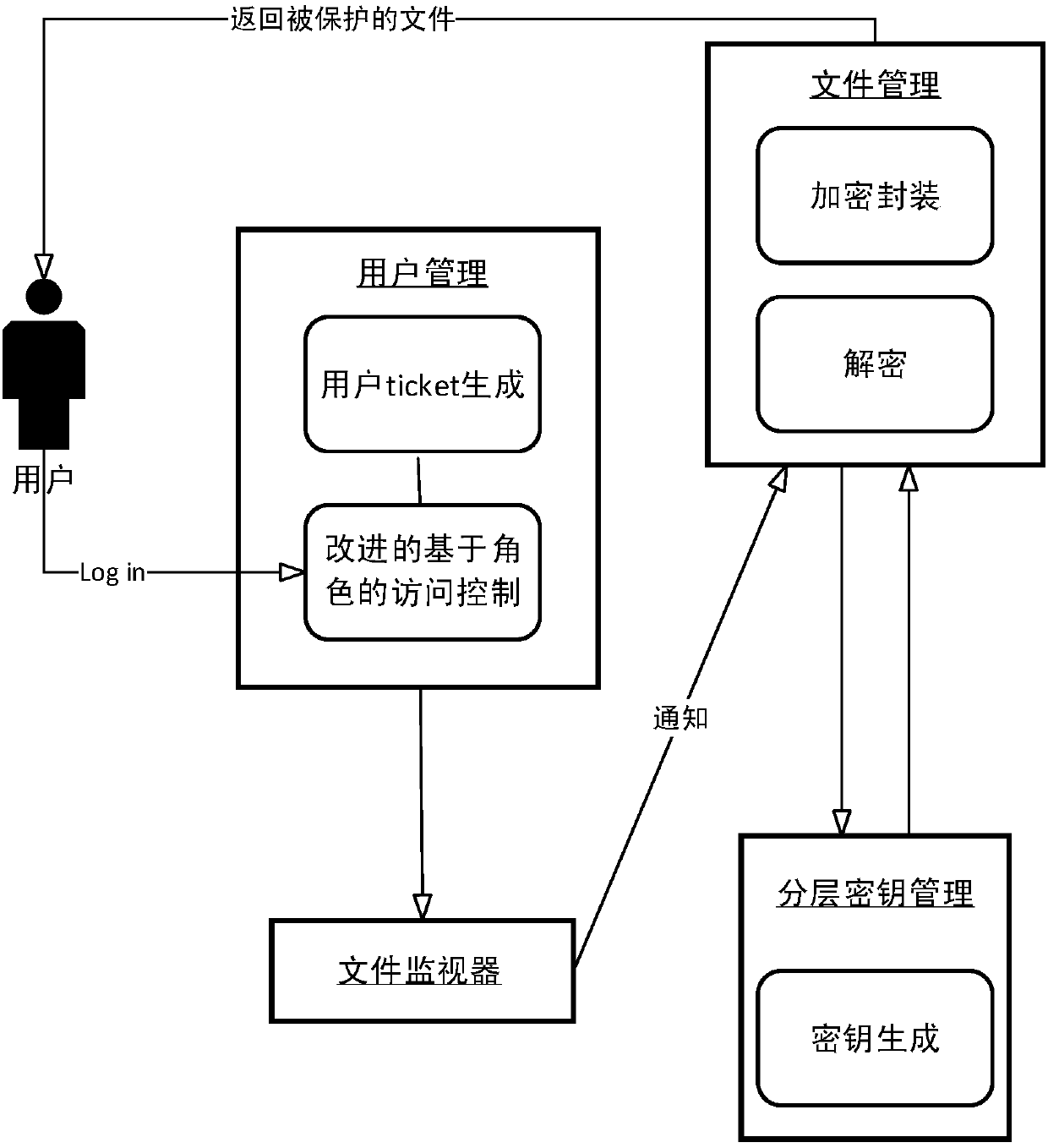
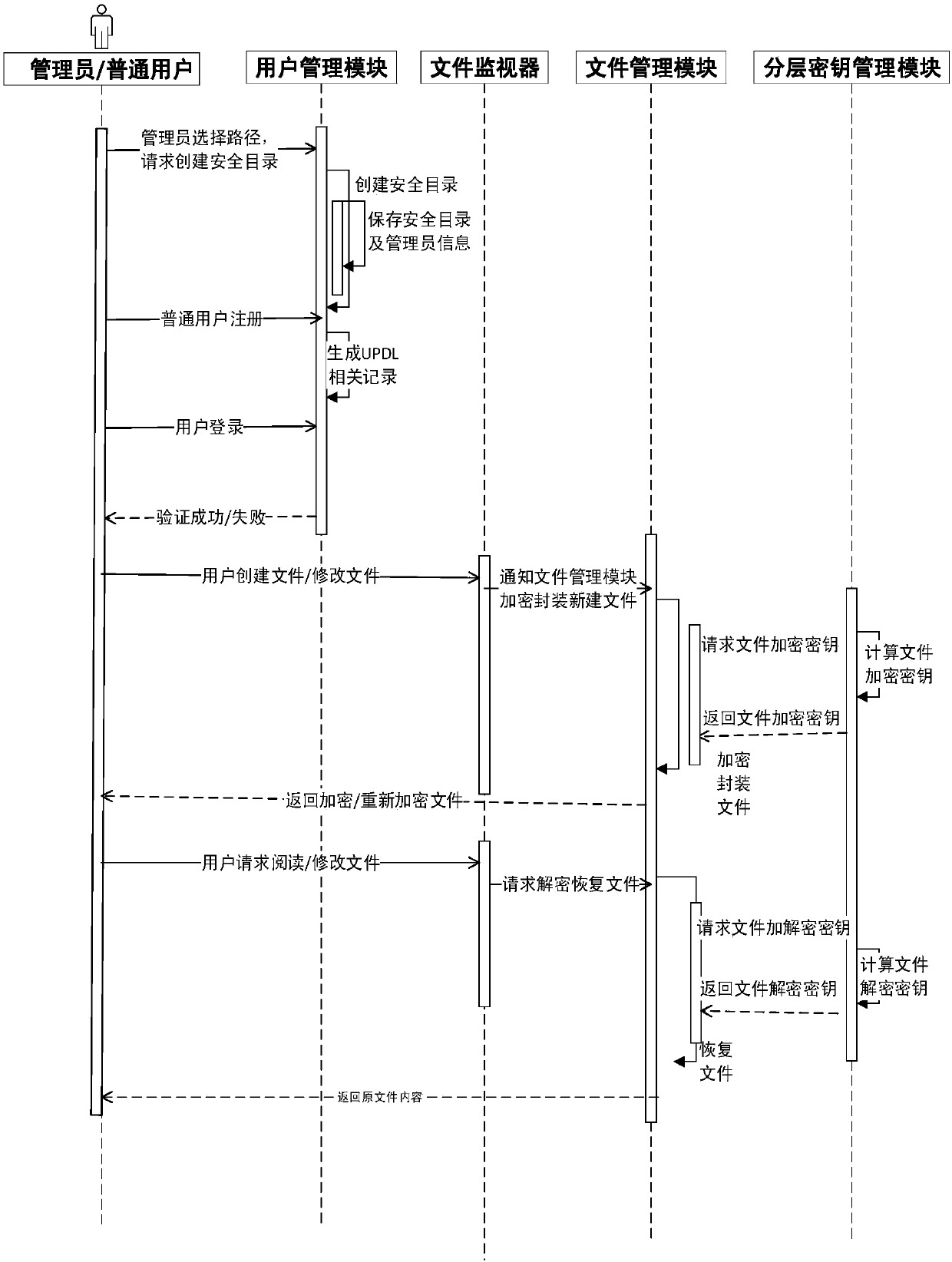
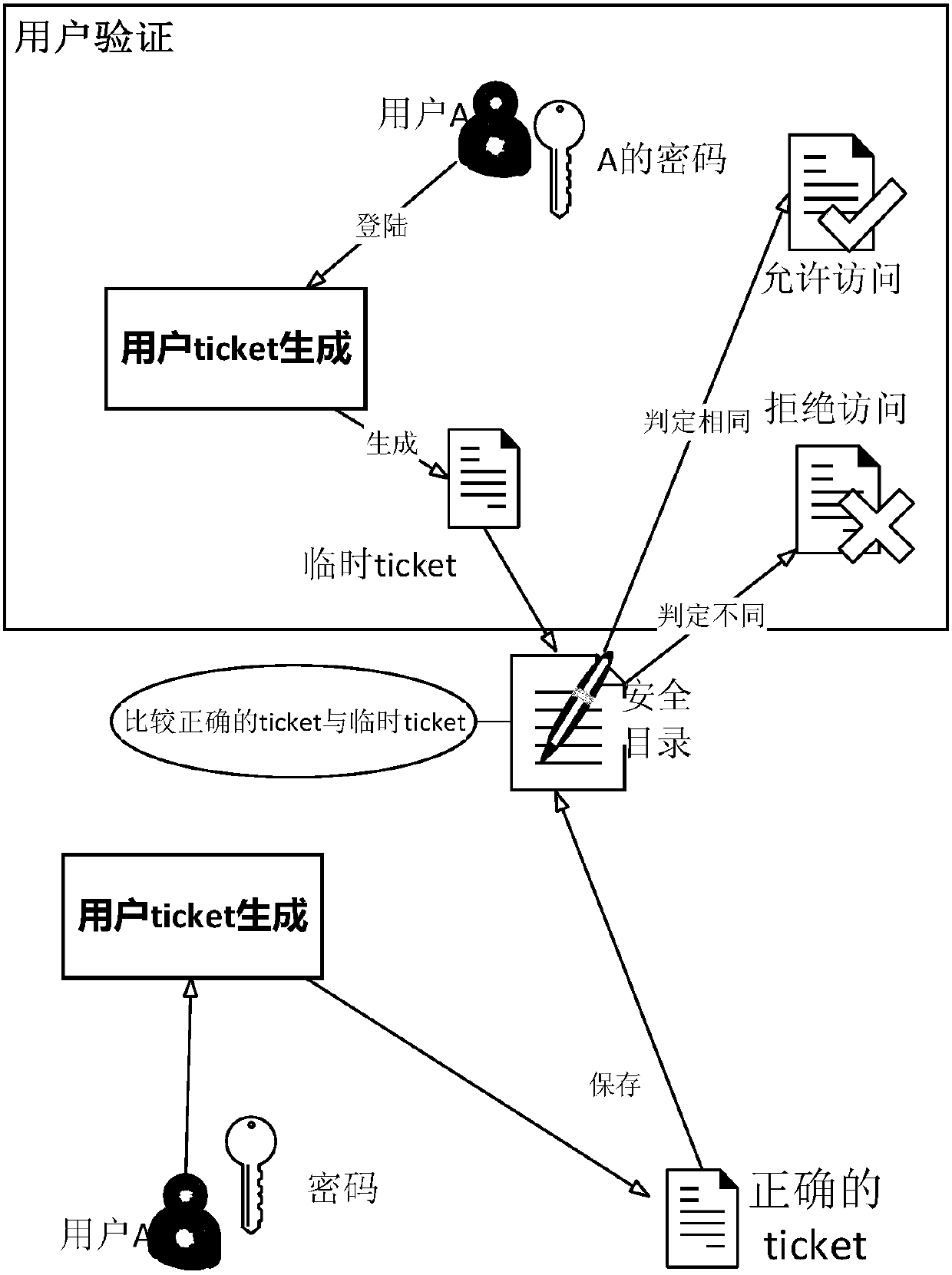
[0070] The present invention will be described in detail below by taking a shared security directory created by a user on a server as an example. figure 1 Shown is the system structure of this embodiment, figure 2 For the file protection method flow and system module relationship diagram provided in this embodiment, the specific implementation of the present invention includes the following steps:
[0071] A1) The administrator creates a security directory
[0072] The administrator enters the account password to enter the file ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com