Method for mobile terminal to access to private network
A mobile terminal and network technology, applied in electrical components, transmission systems, etc., can solve problems such as prominent security problems, poor security, and easy cracking of user name and password information, so as to ensure simplicity, ensure storage security, and ensure safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] Below in conjunction with embodiment the present invention is described in further detail:
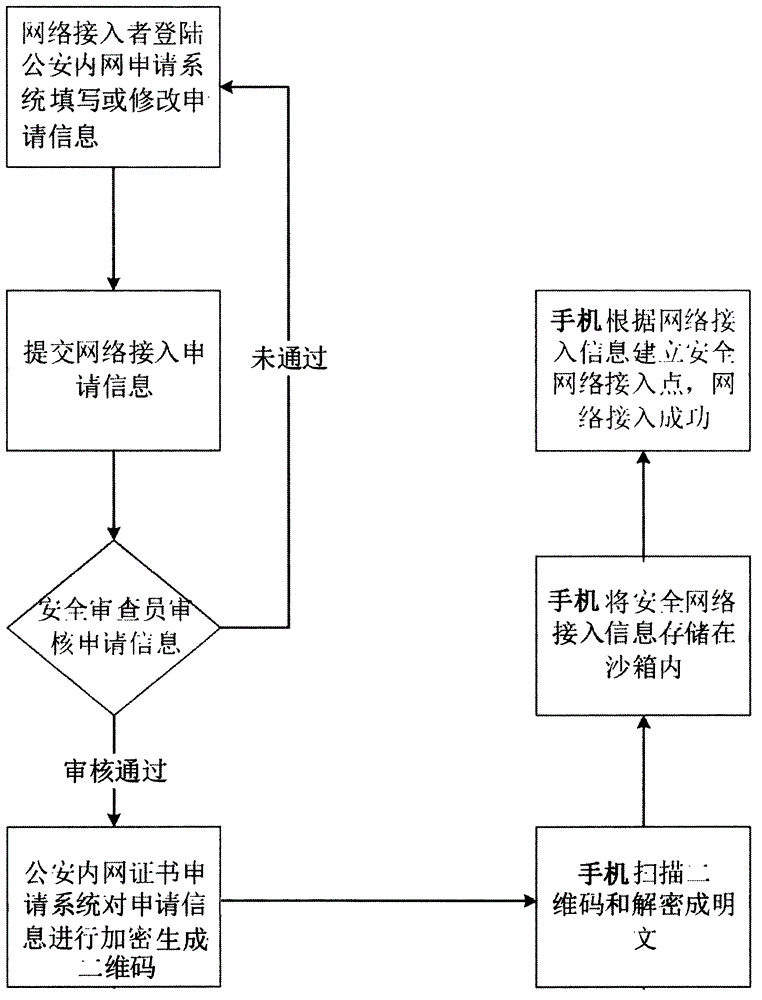
[0020] This network access method is applied to the public security intranet login, and the specific steps are as follows:
[0021] 1) The mobile phone user submits a login application to the public security intranet, filling in information including user information, mobile terminal information, and SIM card information, and the public security intranet manually reviews the login application information;
[0022] 2) After the review is passed, the public security intranet encrypts the application information to generate a QR code;
[0023] 3) The mobile phone scans the QR code and parses it into plain text information and saves it in the sandbox;
[0024] 4) The mobile phone establishes the access point of the public security intranet according to the information saved in the sandbox, and the login is successful.
[0025] After logging in, the user deletes the login applicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com