Intrusion detection independent analysis method and system in cloud calculation environment
A cloud computing environment and intrusion detection technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as limitations of intrusion detection methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
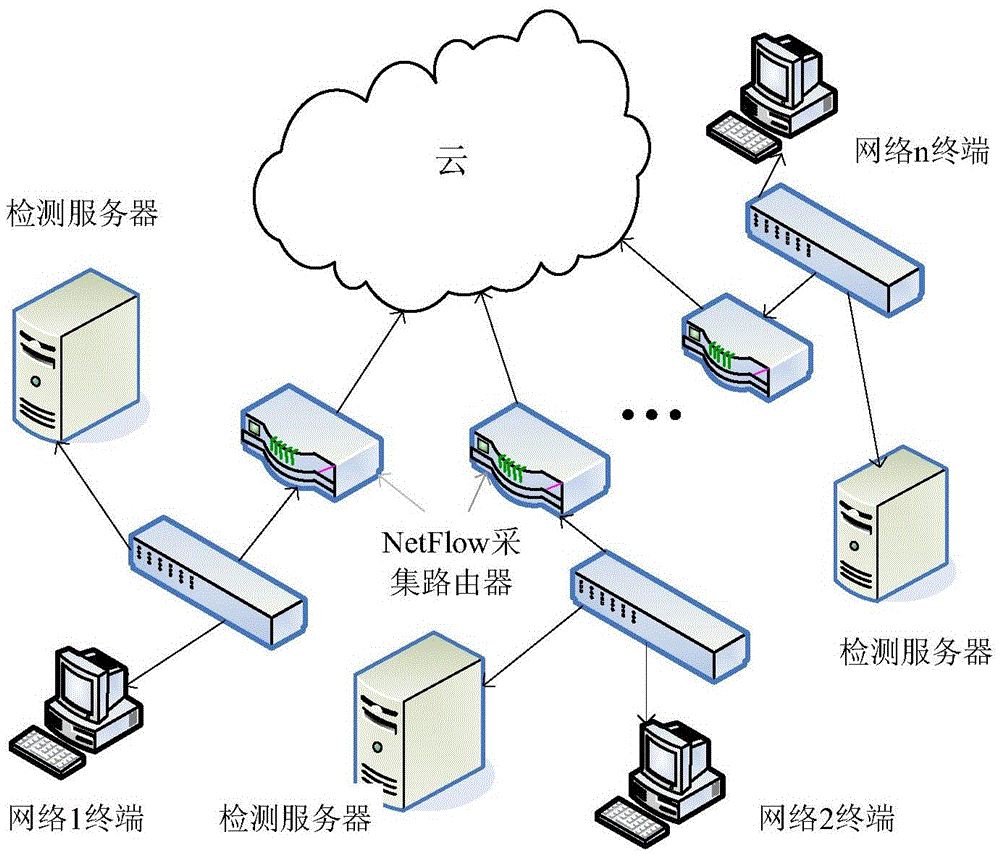
[0056] Such as Figure 1 ~ Figure 3 As shown, in this embodiment, the autonomous analysis intrusion detection system in the cloud computing environment is installed in the detection service when it is in use, and the detection server is connected to the edge device of the network and set at the edge of the network, that is, deployed on each main network segment entry port.
[0057] The autonomous analysis intrusion detection system includes a data acquisition module 1 , a data preprocessing module 2 , an intrusion detector 3 , a resource scheduling module 4 , a response and alarm module 5 , a database 6 and a fault tolerance module 7 .
[0058] Wherein the data collection module 1 promptly is arranged on the network entrance end, is used for monitoring the network traffic of the network entrance end, when the network traffic is abnormal, then...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com