Method, system and device for management, synchronization and backup of data encryption key
A data encryption key and encryption key technology, which is applied in the fields of synchronization and backup, and data encryption key management, can solve problems affecting technical convenience and achieve the effects of convenient sharing, high security, and simple operation steps
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
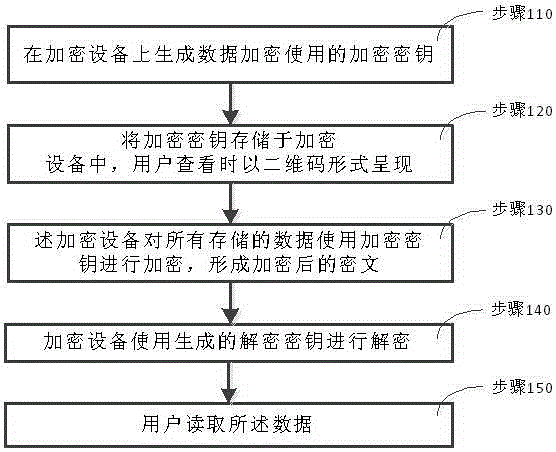
[0087] Such as figure 1 As shown, a method for managing a data encryption key in an embodiment of the present invention includes the following steps:
[0088] Step 110, generating an encryption key used for data encryption on the encryption device;
[0089] Step 120, storing the encryption key in the encryption device, and presenting it in the form of a two-dimensional code when viewed by the user;
[0090] Step 130, the encryption device encrypts all stored data using an encryption key to form encrypted ciphertext;
[0091] Step 140, when the user reads the data, the encryption device uses the generated decryption key to decrypt;
[0092] Step 150: The user reads the data to realize the management of the data encryption key.
[0093] The key used for encryption in this embodiment is the SHA256 key. SHA-256 is a one-way hash algorithm, which converts the plaintext to be transmitted into a message digest through a Hash function operation. Different plaintext corresponds to ...
Embodiment 2
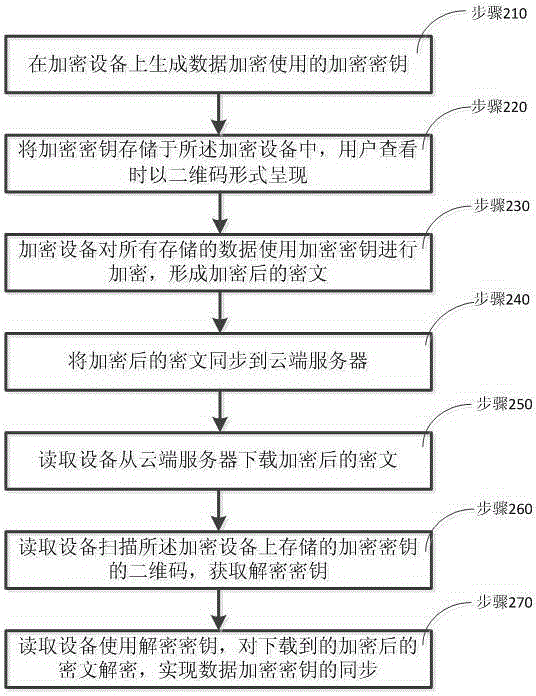
[0096] Such as figure 2 As shown, the present invention also provides a method for synchronizing data encryption keys, comprising the following steps:
[0097] Step 210, generating an encryption key used for data encryption on the encryption device;
[0098] Step 220, storing the encryption key in the encryption device, and presenting it in the form of a two-dimensional code when viewed by the user;
[0099] Step 230, the encryption device encrypts all stored data using an encryption key to form encrypted ciphertext;
[0100] Step 240, synchronizing the encrypted ciphertext to the cloud server;
[0101] Step 250, the reading device downloads the encrypted ciphertext from the cloud server;
[0102] Step 260, the reading device scans the two-dimensional code of the encryption key stored on the encryption device to obtain the decryption key;
[0103] In step 270, the reading device decrypts the downloaded encrypted ciphertext by using the decryption key obtained through scan...
Embodiment 3
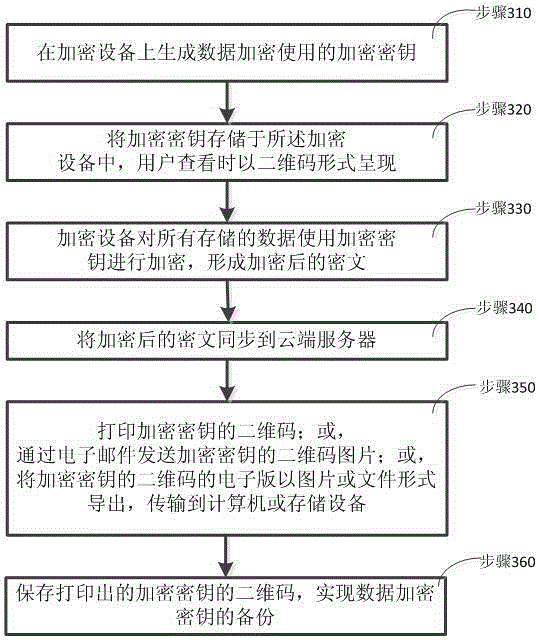
[0107] Such as image 3 As shown, the present invention also provides a backup method of a data encryption key, comprising the following steps:
[0108] Step 310, generating an encryption key used for data encryption at the encryption device;
[0109] Step 320, storing the encryption key in the encryption device, and presenting it in the form of a two-dimensional code when viewed by the user;
[0110] Step 330, the encryption device encrypts all stored data using an encryption key to form encrypted ciphertext;
[0111] Step 340, synchronizing the encrypted ciphertext to the cloud server;
[0112] Step 350, connect the encryption device to the printer, and print the two-dimensional code of the encryption key stored on the encryption device; or,
[0113] Email the QR code of the encryption key stored on the encryption device as a picture; or,
[0114] Export the electronic version of the QR code of the encryption key stored on the encryption device in the form of a picture o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com