Vulnerability detection method and device
A vulnerability detection and vulnerability technology, applied in software testing/debugging, platform integrity maintenance, etc., can solve problems such as inaccurate vulnerability detection, and achieve the effect of solving inaccurate detection, real-time accurate detection, and strong real-time performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0021] According to an embodiment of the present invention, an embodiment of a vulnerability detection method is provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, although A logical order is shown in the flowcharts, but in some cases the steps shown or described may be performed in an order different from that shown or described herein.
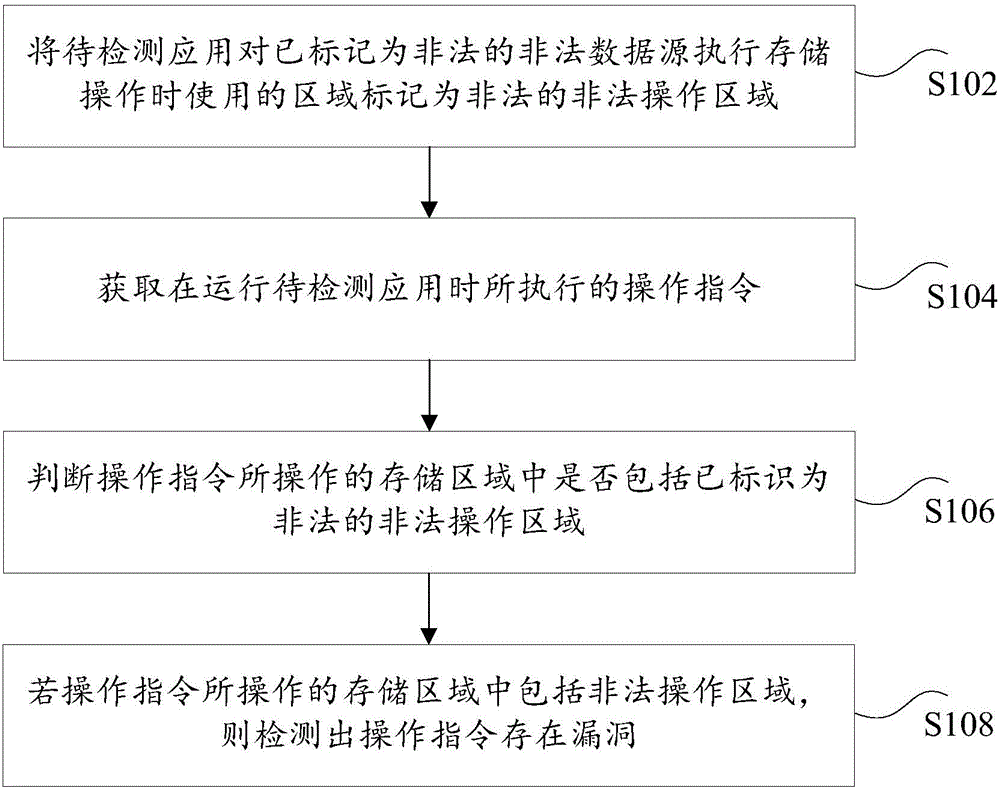
[0022] According to an embodiment of the present invention, a vulnerability detection method is provided, such as figure 1 As shown, the detection method can be realized through the following steps:
[0023] Step S102: mark the area used by the application to be detected when performing a storage operation on the illegal data source marked as illegal as an illegal illegal operation area.
[0024] Step S104: Obtain an operation instruction executed when the application to be detected is running.
[0025]...
Embodiment 2
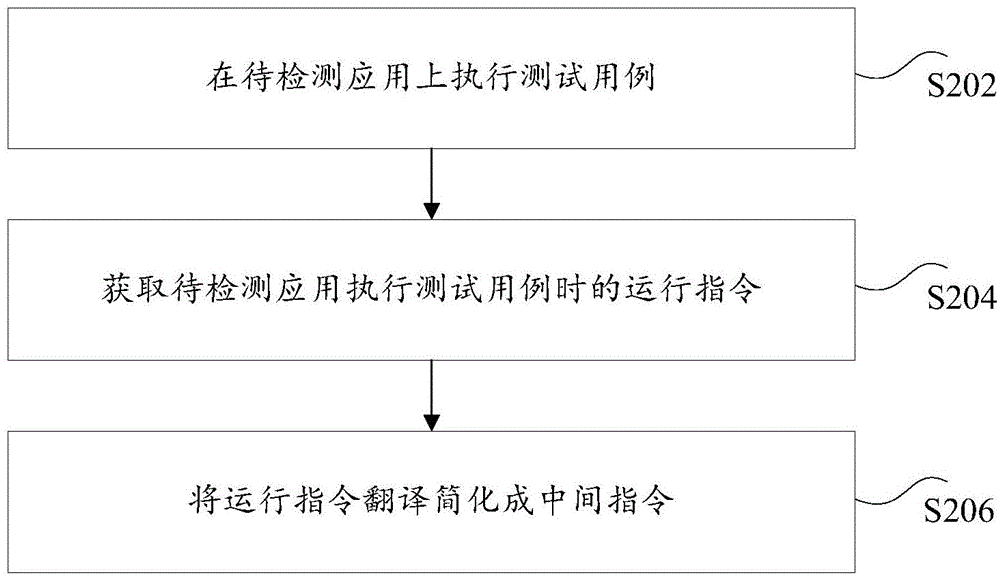
[0110] According to an embodiment of the present invention, a vulnerability detection device is also provided, which can be implemented by the method involved in the embodiment, and the implementation process of the present application will be described in detail below.
[0111] Figure 5 is a schematic structural diagram of a vulnerability detection device according to an embodiment of the present invention.
[0112] Such as Figure 5 As shown, the device may include: a marking module 10 , an instruction acquisition module 20 , an area judgment module 30 , and a vulnerability detection module 40 .
[0113] Wherein, the marking module is configured to mark the area used when the application to be detected performs a storage operation on the marked illegal data source as an illegal illegal operation area.
[0114] The instruction acquiring module is configured to acquire an operation instruction executed when the application to be detected is running.
[0115] The area judgi...
Embodiment 3
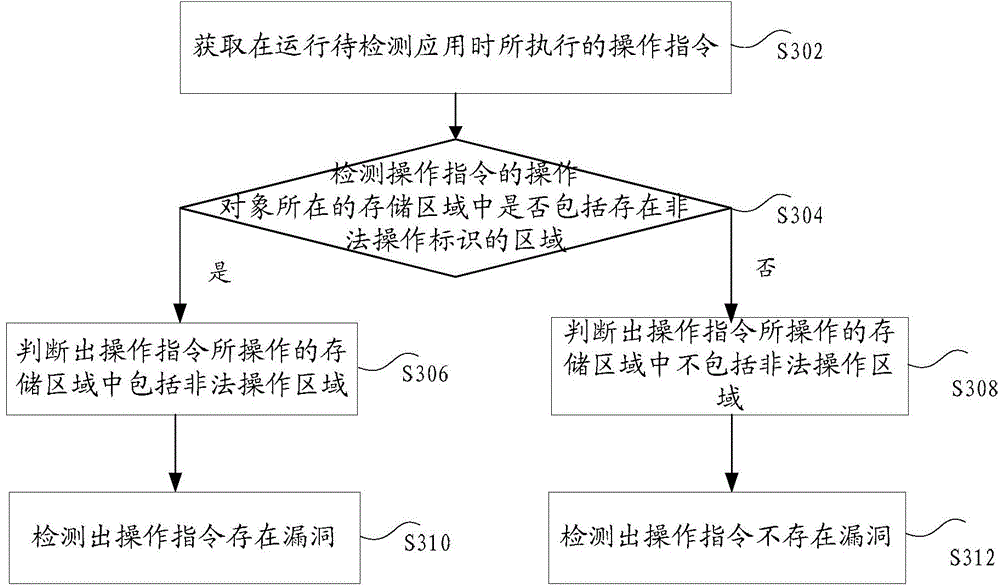
[0148] The embodiment of the present invention also provides a terminal. Optionally, in this embodiment, the above-mentioned terminal may execute the vulnerability detection method, and the vulnerability detection device in the above-mentioned embodiment may be set on the terminal.
[0149] Figure 6 is a structural block diagram of a terminal according to an embodiment of the present invention. Such as Figure 6 As shown, the terminal 50 may include: one or more (only one is shown in the figure) processors 51 , a memory 53 , and a transmission device 55 .
[0150] Among them, the memory 53 can be used to store software programs and modules, such as the program instructions / modules corresponding to the vulnerability detection method and device in the embodiment of the present invention, and the processor 51 executes various functions by running the software programs and modules stored in the memory 53. A functional application and data processing, that is, to realize the ab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com