Authentication method and device based on authentication equipment
A technology for authenticating equipment and authenticating data, which is applied in the field of information security, can solve problems such as password leakage, personal privacy information that is vulnerable to attack, and loss, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
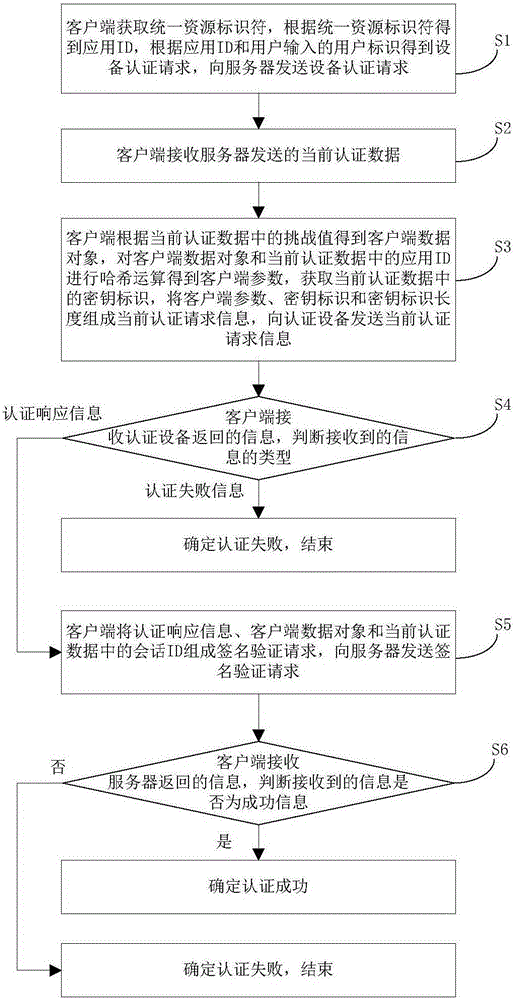
[0052] Embodiment 1 of the present invention provides an authentication method based on an authentication device, such as figure 1 shown, including:
[0053] Step S1: The client obtains a uniform resource identifier, obtains an application ID according to the uniform resource identifier, obtains a device authentication request according to the application ID and the user ID input by the user, and sends the device authentication request to the server;
[0054] Step S2: the client receives the current authentication data sent by the server;
[0055] Step S3: The client obtains the client data object according to the challenge value in the current authentication data, performs a hash operation on the client data object and the application ID in the current authentication data to obtain the client parameters, and obtains the key identifier in the current authentication data , compose the client parameter, the key identifier and the key identifier length into the current authentic...
Embodiment 2
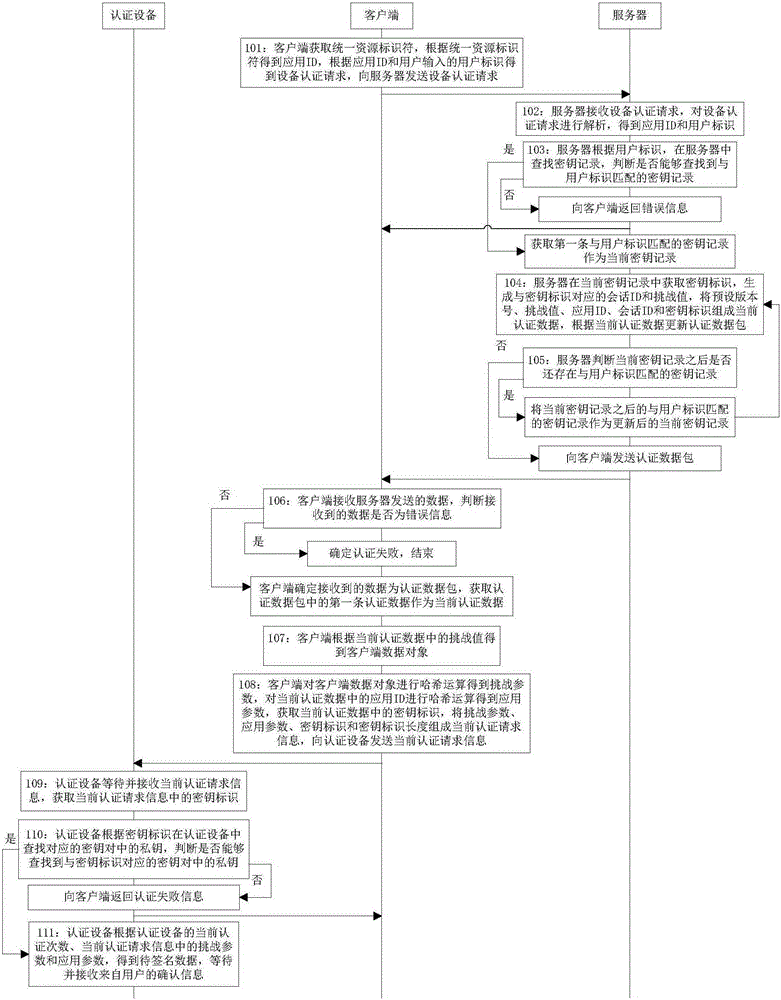
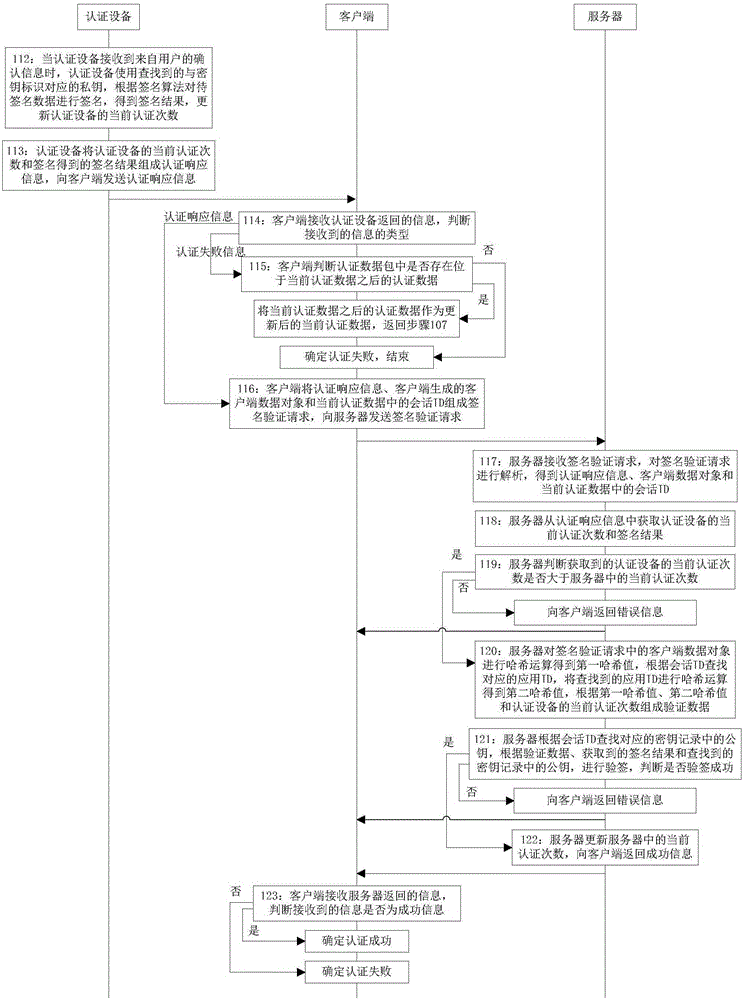
[0070] Embodiment 2 of the present invention provides an authentication method based on an authentication device, such as Figure 2 to Figure 3 shown, including:
[0071] Step 101: the client obtains a uniform resource identifier (UniformResourceIdentifier), obtains an application ID according to the uniform resource identifier, obtains a device authentication request according to the application ID and the user identifier input by the user, and sends the device authentication request to the server;
[0072] Specifically, if the client is a browser, the client obtains the header field of the uniform resource identifier accessed as the application ID; if the client is an Android system, the client obtains the key identifier of the signed Android installation package. The content is used as a uniform resource identifier; if the client is an iOS system, the client obtains the content of the IOS application identifier as a uniform resource identifier;
[0073] For example, in thi...
Embodiment 3
[0123] Embodiment 3 of the present invention provides an authentication method based on an authentication device, such as Figure 4 to Figure 6 shown, including:
[0124] Step 201: the client obtains a uniform resource identifier (UniformResourceIdentifier), obtains an application ID according to the uniform resource identifier, obtains a device authentication request according to the application ID, the application identifier, and the user identifier input by the user, and sends the device authentication request to the server;
[0125]Specifically, if the client is a browser, the client obtains the header field of the uniform resource identifier accessed as the application ID; if the client is an Android system, the client obtains the key identifier of the signed Android installation package. The content is used as a uniform resource identifier; if the client is an iOS system, the client obtains the content of the IOS application identifier as a uniform resource identifier; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com