HTTP secure communication method and system suitable for CDN value-added service platform
A value-added service platform and secure communication technology, applied in transmission systems, electrical components, etc., can solve problems such as failure of security defense capabilities, inability to defend against client reverse cracking, etc., and achieve the effect of defending against replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
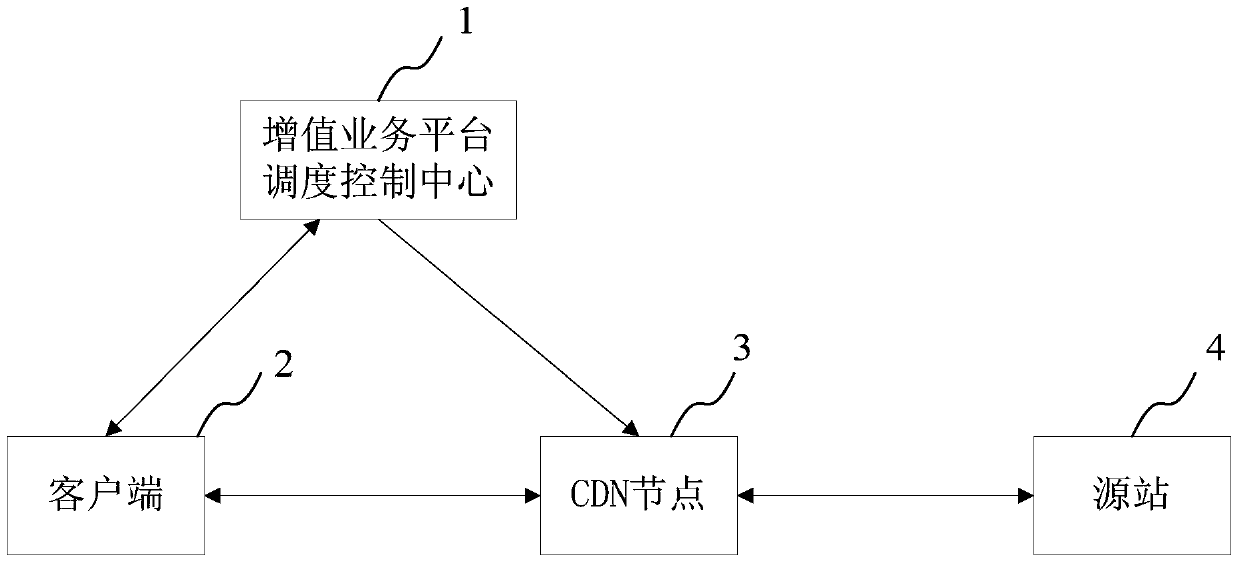
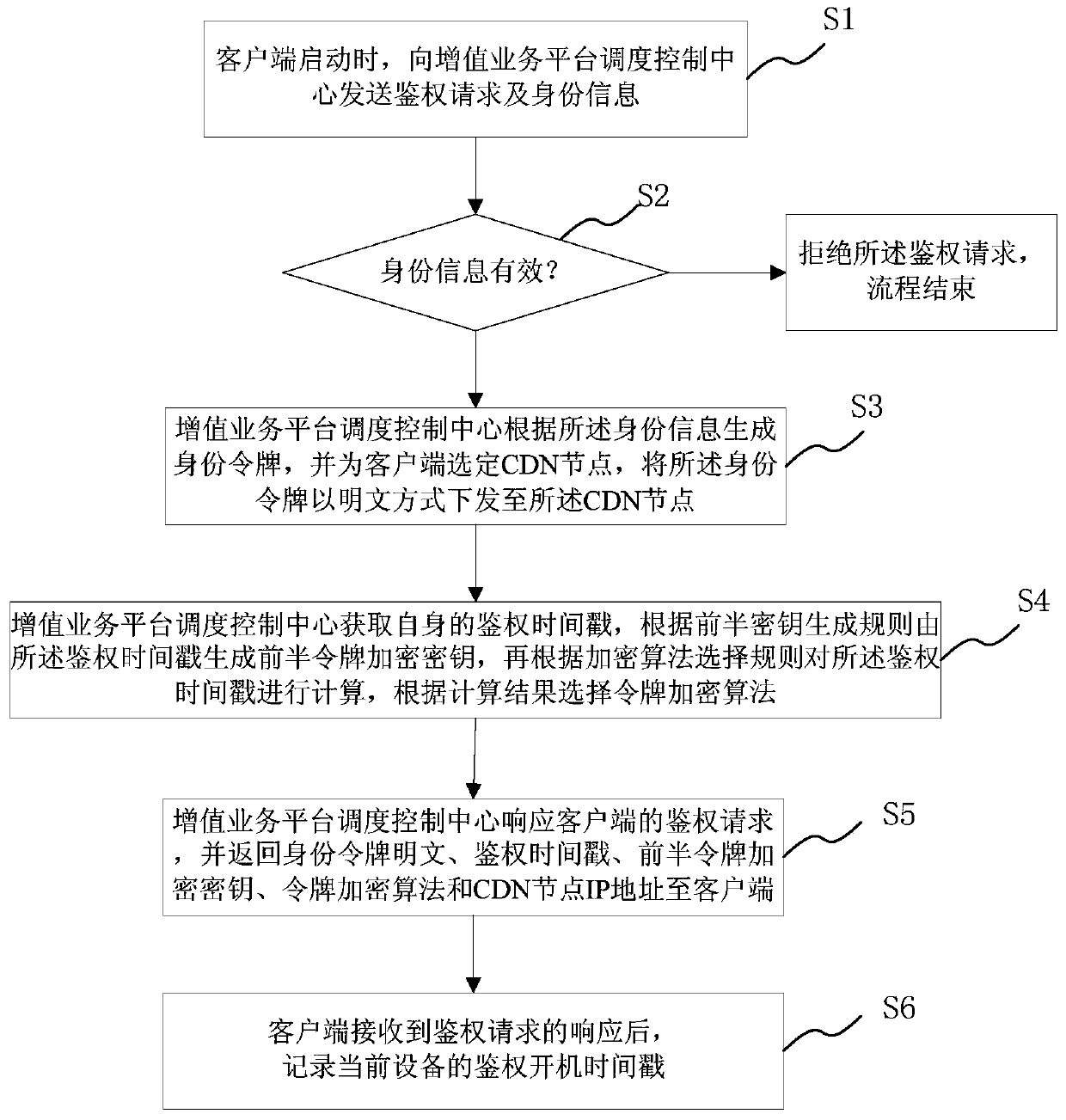
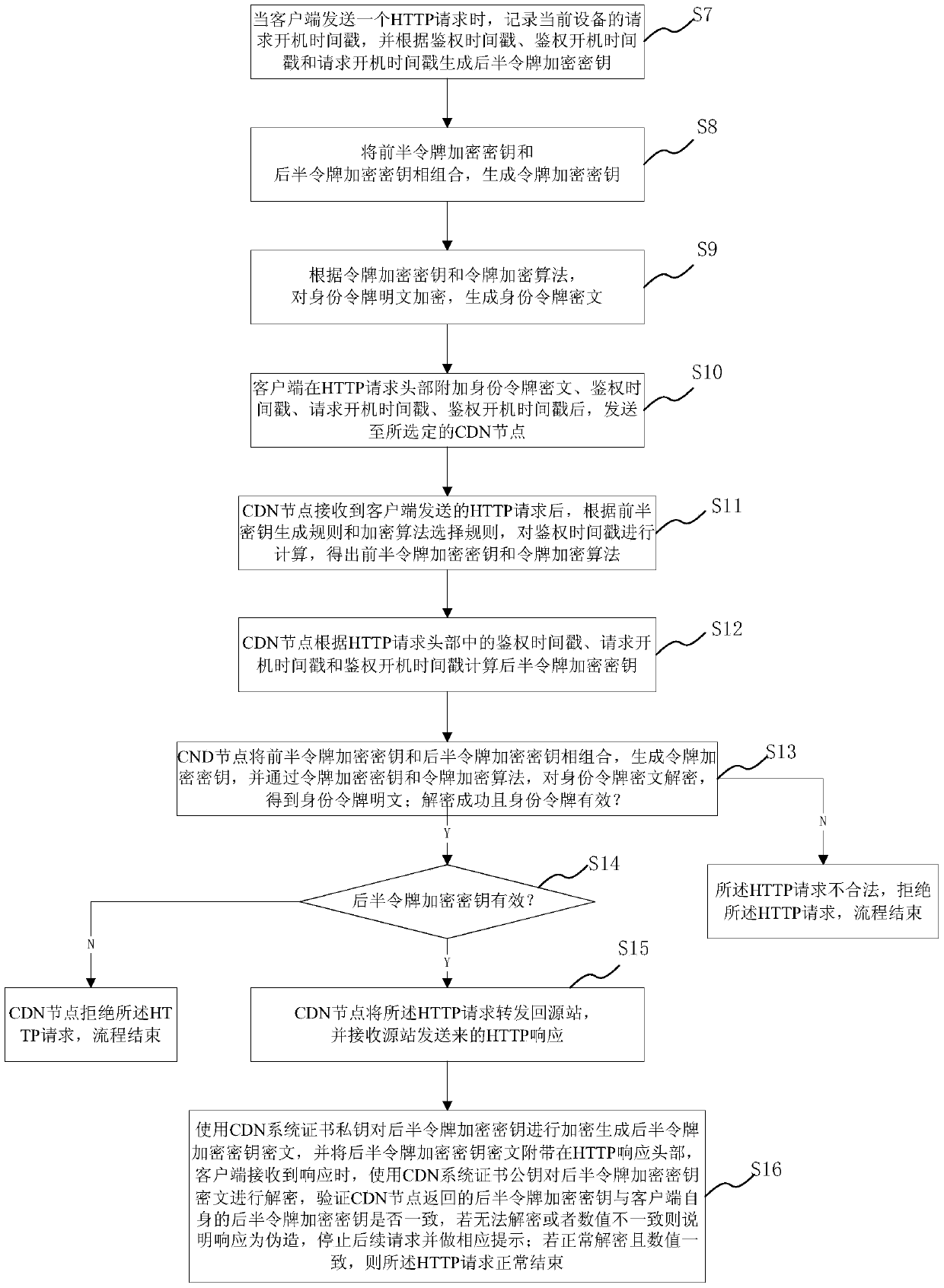
Image
Examples
Embodiment 1
[0083] Example 1: Normal HTTP request
[0084] 1) The client uses HTTPS to initiate a login request, and the content of the request is as follows:
[0085] POST / login HTTP / 1.1
[0086] User-Agent: Test-Client
[0087] Content-Length: 34
[0088] Host: www.cdnvas.com
[0089] {
[0090] username=testusr;
[0091] password=testpwd;
[0092]}
[0093] 2) The dispatch control center of the value-added service platform checks the account name and password and confirms that they are valid. Use the MD5 algorithm to calculate the "username_password" to get the user's identity token. MD5(testusr_testpwd)=58d04acca5d09641967d3f28756da156.
[0094] 3) The dispatch control center of the value-added service platform selects a CDN node for the client with an IP address of 123.1.13.76, and issues the identity token to the CDN node. The CDN node stores this identity token in the local database.
[0095] 4) The dispatch control center of the value-added service platform obtains the c...
Embodiment 2
[0127] Example 2: Replay attack
[0128] 1) The attacker intercepts the normal HTTP request sent by the client of the system through sniffing.
[0129] 2) After a period of time, the attacker uses a replay attack on other client devices to send a large number of replay requests that are exactly the same as the intercepted request data.
[0130] 3) When the replay request reaches the node, the node verifies the timestamp.
[0131] 4) The requested timestamp does not comply with the time verification rules, and the request is rejected.
Embodiment 3
[0132] Example 3: Client reverse cracking, stealing identity tokens
[0133] 1) The attacker reverses the client through decompilation and fully understands the encryption and decryption process of the client.
[0134] 2) The attacker intercepts the authentication request by sniffing. Since the authentication request uses HTTPS, the attacker cannot obtain the key and the encryption algorithm used.
[0135] 3) The attacker intercepts the HTTP request by sniffing, and obtains the time stamp and identity token ciphertext.
[0136]4) Since the key is generated by calculating the timestamp according to specific rules, and the algorithm only exists in the control center and nodes, the attacker cannot know the specific rules, so the attacker cannot obtain the key information from the intercepted request.
[0137] 5) The attacker cannot decrypt the ciphertext of the identity token, and the theft of the identity token fails.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com