Object reference graph-based Android cellphone malicious software detection method
A technology of malware and detection methods, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems such as the application of VF2 algorithm, achieve wide applicability, avoid code confusion attacks, and reduce system overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0041] Specific embodiment one: a kind of Android mobile phone malware detection method based on the object reference graph of the present embodiment is specifically prepared according to the following steps:
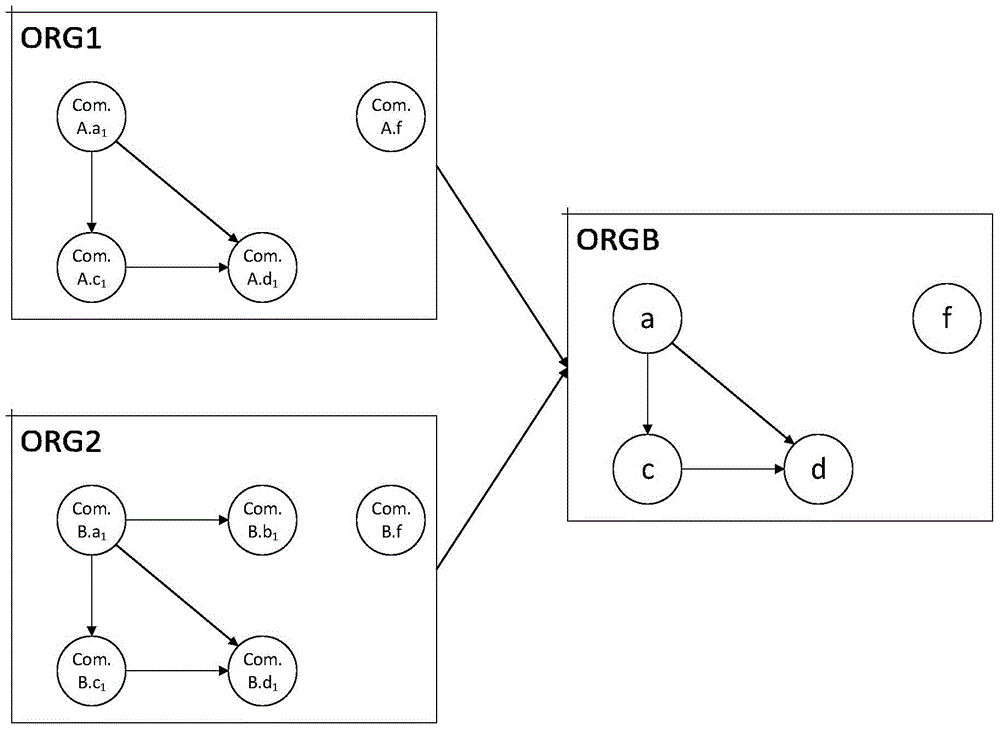
[0042] Step 1. Run the classified malicious programs under the Android platform separately, and extract the corresponding reference relationship graph ORG between objects from the malicious program heap memory; wherein, ORG (Object Reference Graph) is an object reference graph, which is a binary group ORG =(N, E), N is a collection of nodes in the graph, and each element in N represents the class of the generated object; E∈N×N is a collection of reference relationships between objects; the object is the object in the ORG graph Nodes and edges represent the reference relationship between objects; ORG is the abbreviation of object reference graph; ORG is a directed graph, the nodes in the graph represent objects, and the edges represent the reference relationship between o...
specific Embodiment approach 2
[0061] Specific embodiment 2: The difference between this embodiment and specific embodiment 1 is that in step 1, the timing of extracting the corresponding reference relationship graph ORG between objects from the malicious program heap memory is specifically:
[0062] Malicious programs are usually hosted in normal programs, and the malicious code will be executed only under certain trigger conditions; and different trigger conditions, the programs executed by malicious code will be different, which leads to different ORG graphs obtained in different periods. are different, so it is necessary to study the timing of extraction;
[0063] Through the analysis of various types of malicious programs, we found that the malicious behavior of malicious programs is usually extracted at the following times:
[0064] (1) Start with the host program;
[0065] (2) Start with the boot;
[0066] (3) Self-start after the program is closed;
[0067] (4) Start under specific trigger condit...
specific Embodiment approach 3
[0069] Specific embodiment three: the difference between this embodiment and specific embodiment one or two is that in step one, the classified malicious programs under the Android platform are run separately, and the reference relationship graph ORG corresponding to objects is extracted from the malicious program heap memory Specific process:
[0070] The object reference graph ORG is obtained under the Android platform; the main reason for this is that the exported original heap memory file (Hprof) is too large, and the file size is in M; therefore, it is necessary to analyze the original heap memory file (Hprof) under the Android platform. Effective information in the file is extracted and transmitted to the server, thereby reducing the amount of transmitted data;
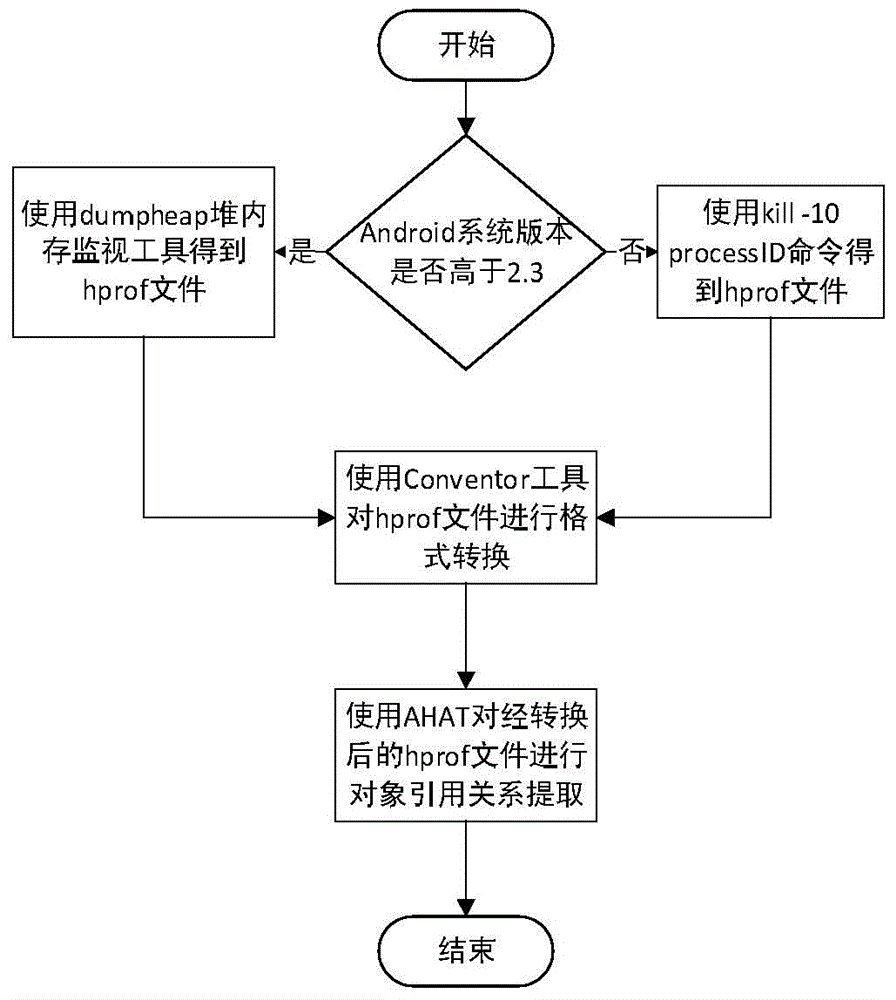
[0071] Obtaining the object reference graph under the Android platform is divided into 3 steps; figure 1 shown;
[0072] (1) Export the original heap memory file; the Android SDK provides a feature-rich memor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com