Cross-trust-domain authentication method used for distributed network system
A distributed network and cross-trust domain technology, applied in the field of cross-trust domain authentication, can solve the problems of system efficiency bottleneck, difficult hardware implementation, and inability to effectively solve cross-domain interactive authentication, so as to avoid creation and maintenance costs and reduce operation cost effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
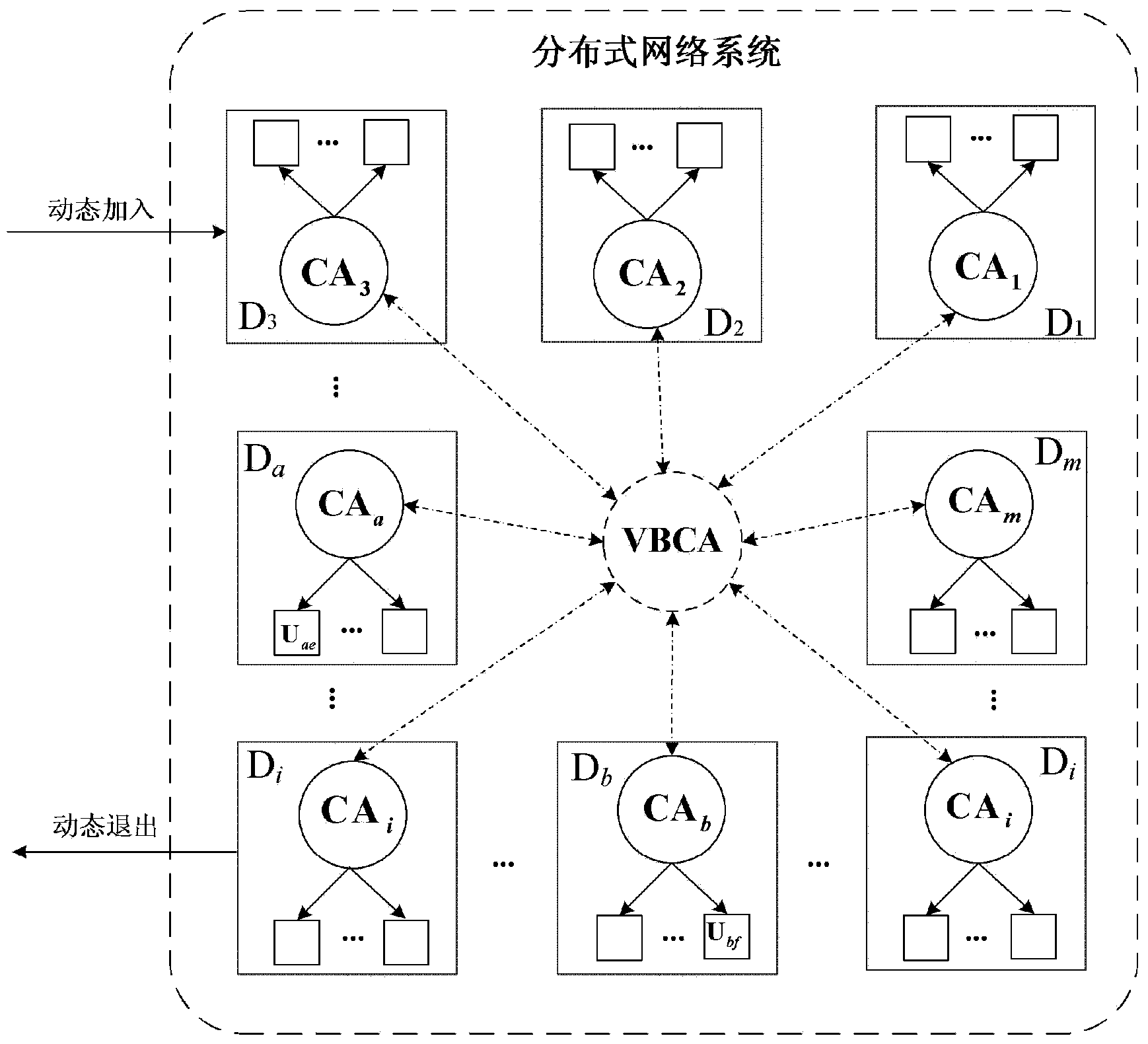
[0064] see figure 1 , an embodiment of the present invention is a cross-trust domain authentication method for a distributed network system, the specific steps of which are as follows:
[0065] A. Creation of Virtual Bridge Certification Center
[0066] A1. All members of the distributed network system trust domain D i (i=1,2,...,m) public parameters of the common selection system: the elliptic curve E on the finite field GF of the cryptographic algorithm and the q-order base point P on the elliptic curve E, the secret sharing threshold t, where i is the serial number of the member trust domain, m is the number of member trust domains, and q is the large prime factor of the order of the elliptic curve E;
[0067] A2. All members trust domain D i According to the organizational model of the distributed network system and the cooperative relationship between the trust domains, negotiate and publish the trust domain D of each member i The permission set V i ,satisfy Among ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com