Mobile Internet security service system
A mobile Internet and security service technology, applied in security devices, electrical components, wireless communications, etc., can solve the problems of Android ecosystem security risks, insufficient supervision and control capabilities, stealing user privacy information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be described in detail below through specific embodiments and accompanying drawings.
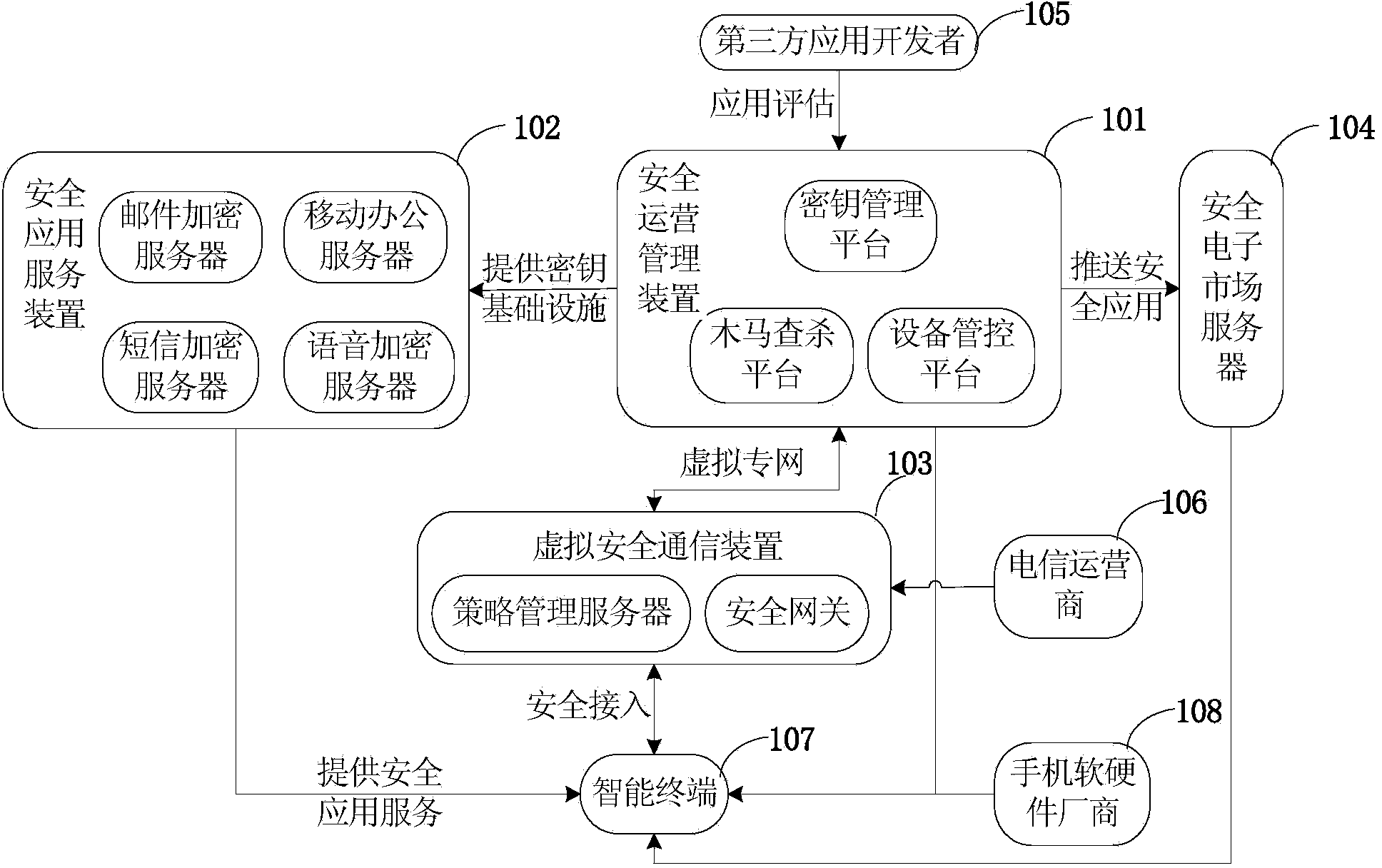
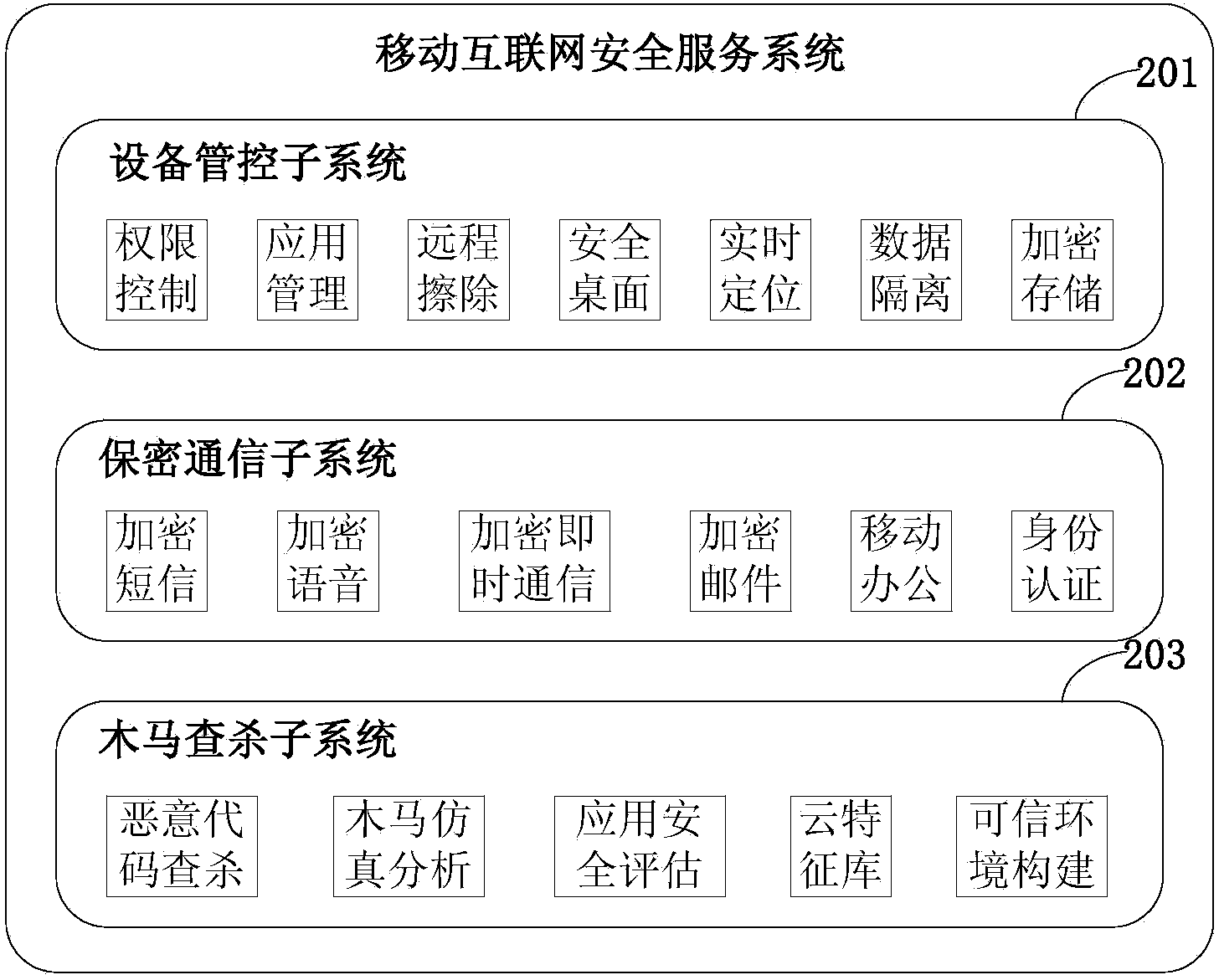
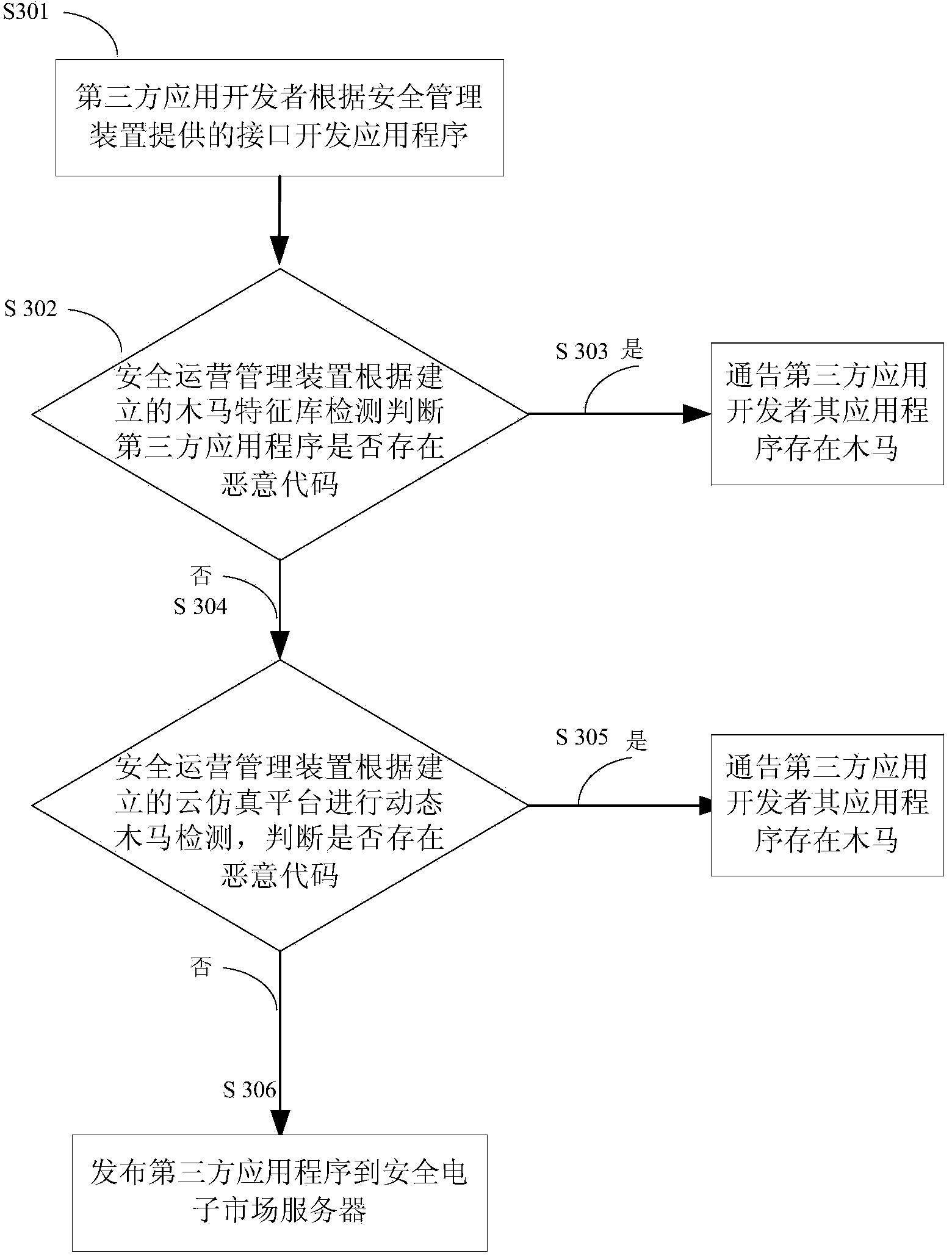
[0027] figure 1 It is a diagram describing the relationship between devices of the mobile Internet security service system of the present invention. Such as figure 1 As shown, the security operation management device 101 provides functions of key distribution and management, mobile device control, malware detection and evaluation, and software testing and evaluation, including key management platform, device management and control platform, and Trojan horse detection and killing platform, which are the core of the entire security service system core manager. The key management platform distributes the key during the registration process of the smart terminal, manages the entire life cycle of the terminal key, and performs identity authentication during the user login process. The device management and control platform and the smart terminal operating syst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com