Wireless local area network security communication method based on quantum key distribution
A quantum key distribution, wireless local area network technology, applied in the field of identity authentication and key negotiation implementation, can solve the problems of lack of key confirmation, lack of security properties, disconnection between authentication and key negotiation, etc., to improve security and prevent middlemen Effects of tampering and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] The present invention will be described in further detail below in conjunction with the accompanying drawings.
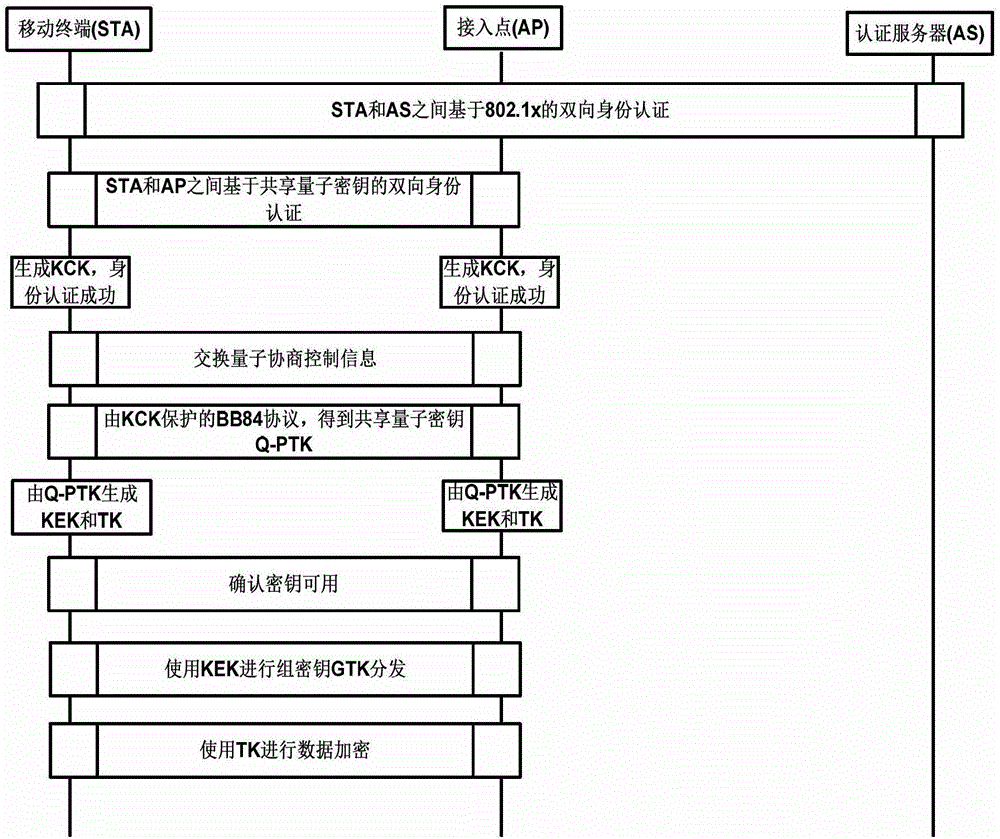
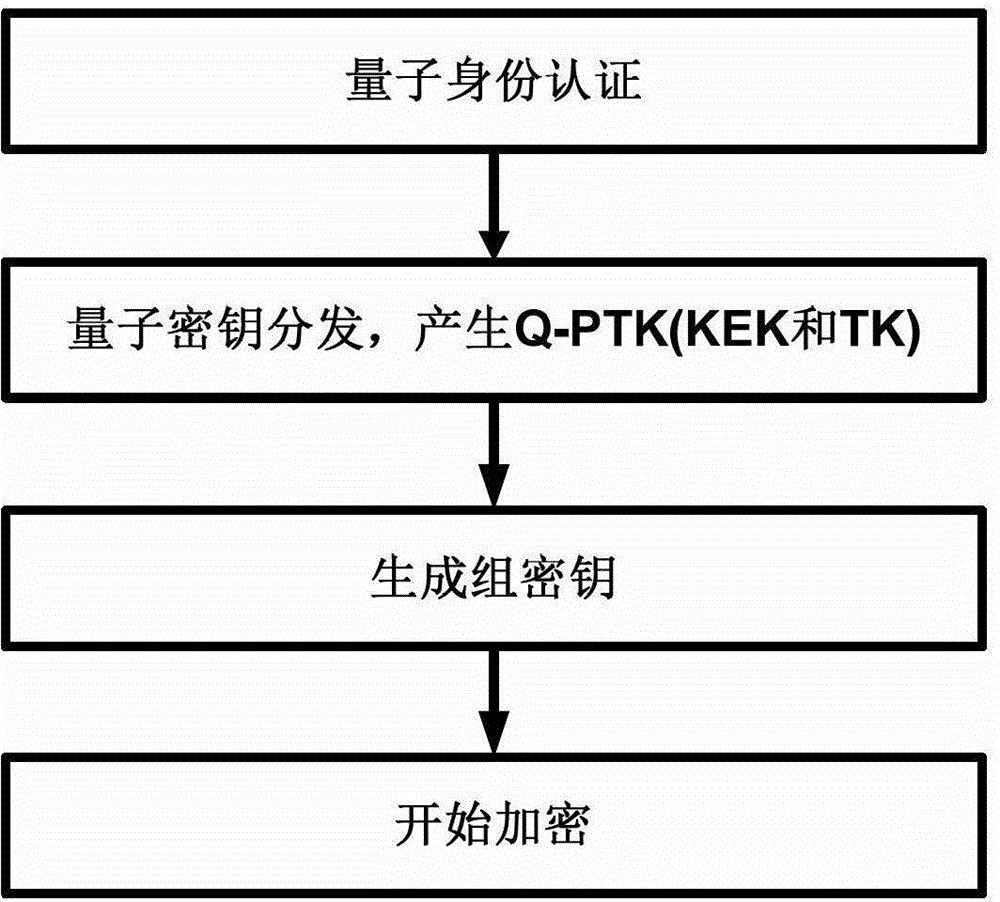
[0069] The present invention proposes a new quantum key-based identity authentication and handshake protocol method, such as figure 2 As shown, the complete identity authentication and key agreement process based on quantum key is divided into four parts, the first part is identity authentication based on quantum key, and the second part obtains the quantum segment transmission shared by both parties through quantum key distribution Key Q-PTK, further divide Q-PTK into KEK and TK. The third part generates group temporary key GTK, which is used to encrypt broadcast information and is an optional part of the protocol. The last part of the encryption process begins.
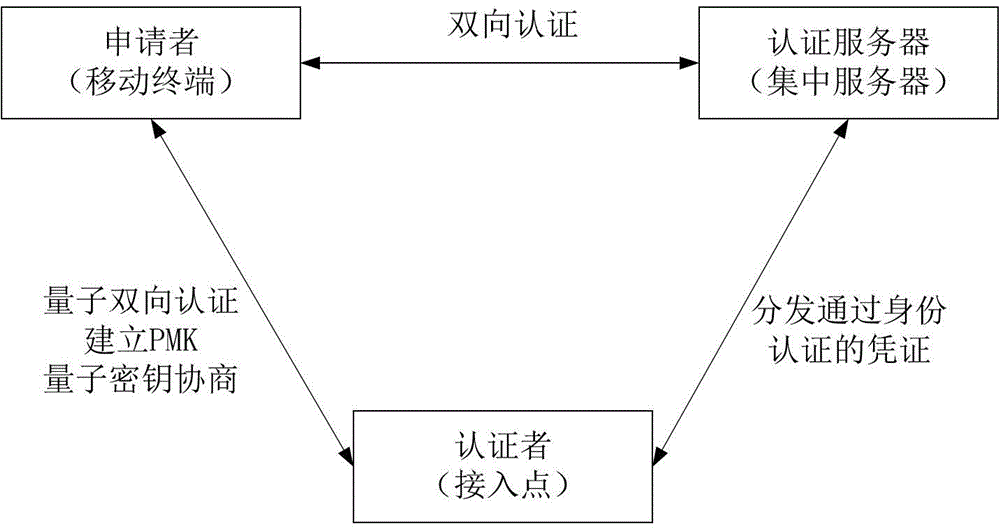
[0070] In identity authentication and security access technology, the three parts involved in authentication are applicant (wireless access terminal STA), authenticator (ie wireless access point...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com