Method for generating and simplifying self-similarity traffic of network key node based on opening/closing source model
A key node and source model technology, applied in the field of electronic information, can solve problems such as complex flow input
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
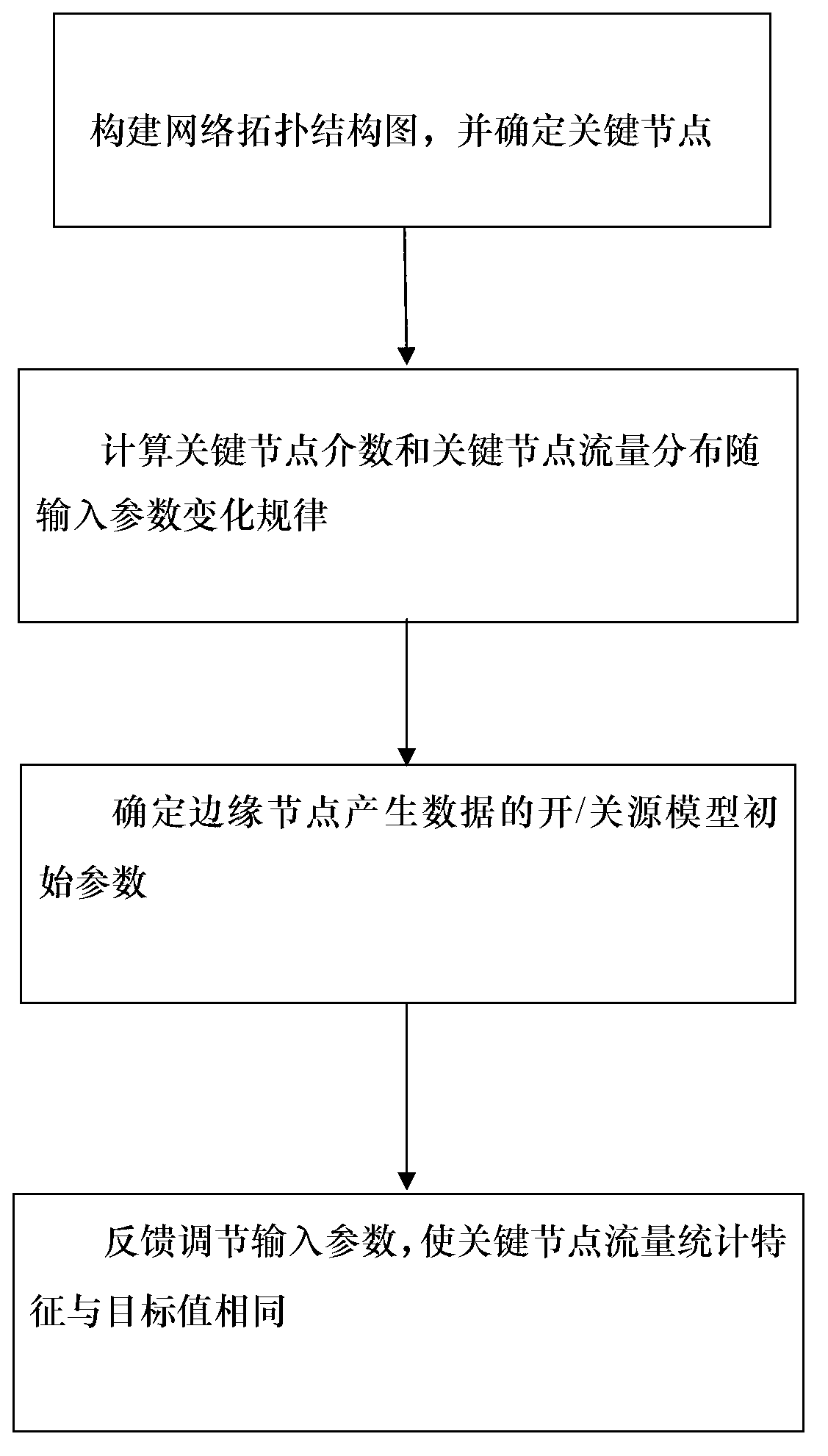
[0070] Secondly, according to the obtained adjacency matrix (A((a ij ) n×n )) to get edge nodes (s) and key nodes (K), the implementation method is as follows:
[0071] (1) Add each column of A to get the node degree vector (v);
[0072] (2) Select the node whose element is 1 in V and store it in S as the edge node, with a total of 656 elements;
[0073] (3) Store the node represented by the largest number in V into K, which is the key node. That is, the node with the largest degree.
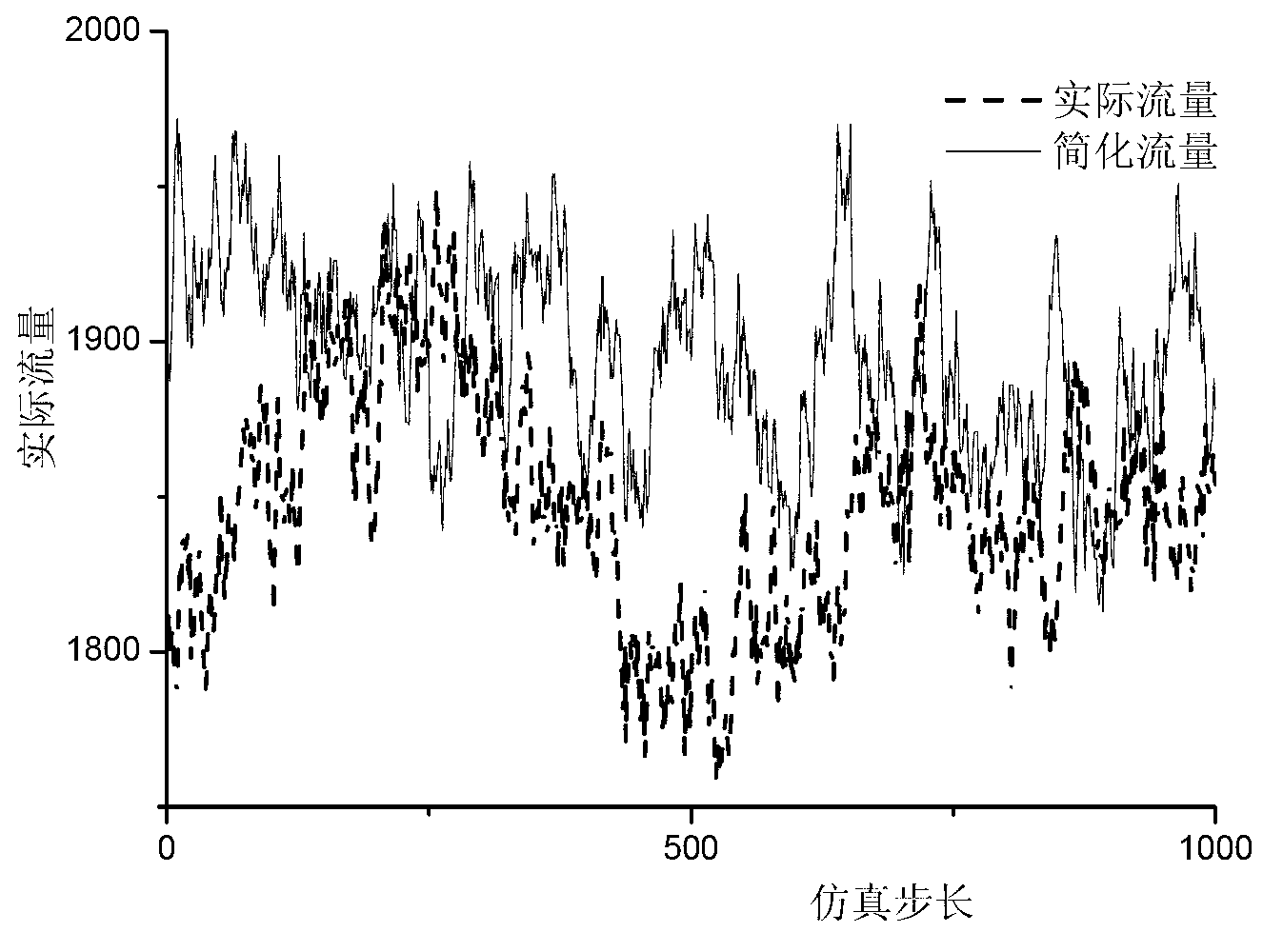
[0074] Step 2: Calculate the betweenness of key nodes and the change law of flow distribution of key nodes with input parameters
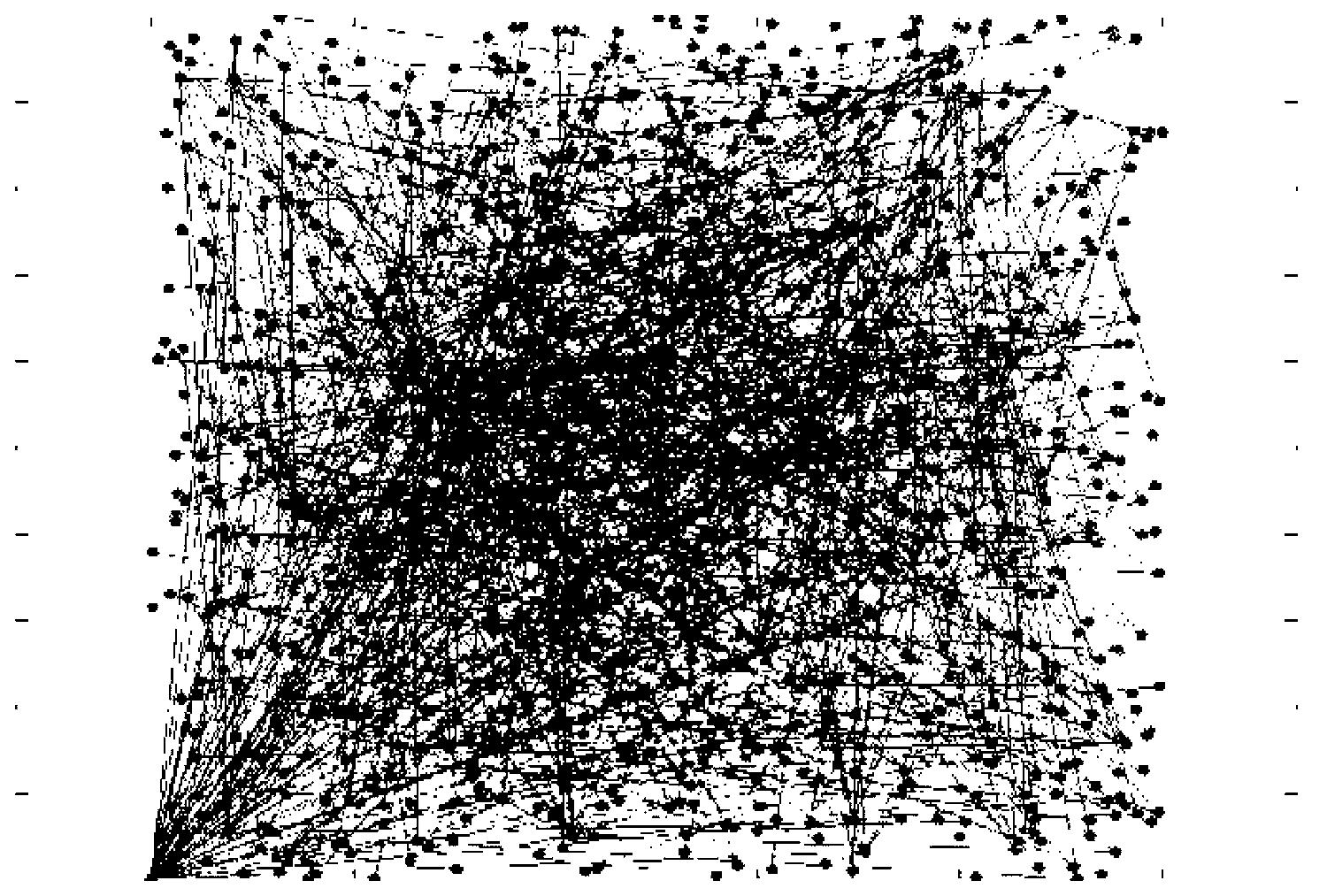
[0075] According to the adjacency matrix obtained in step 1, directly draw its topology map in Matlab, such as figure 1 As shown, the following determines the betweenness of key nodes and explores statistical laws. The implementation steps are as follows:
[0076] (1) For each edge node s(i), the target node T(j) is randomly selected with equal probability, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com