Graphic interchange format (GIF) image encryption method based on compressed encoding
A technology of compression coding and encryption method, which is applied in the field of digital image encryption, can solve the problems of great impact on security, inability to adjust encryption strength adaptively, increase ciphertext volume, etc., achieve good security, maintain format compatibility, and The effect of encryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
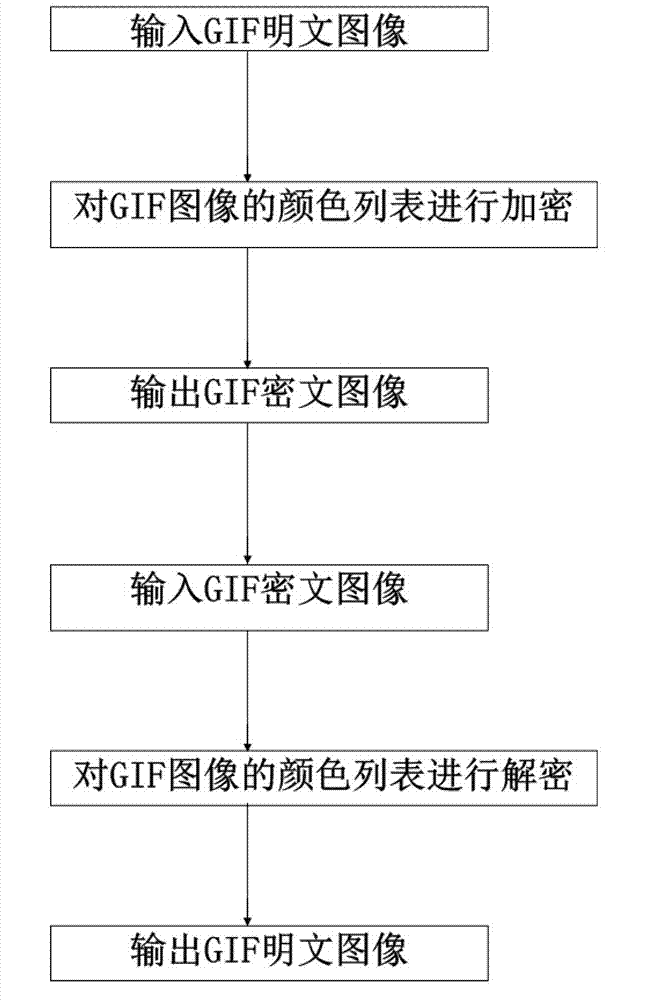
[0072] Embodiment one: if figure 1 Shown, a kind of GIF image encryption method based on compression coding is characterized in that comprising the following steps:
[0073] Step 1. Input the GIF plaintext image;
[0074] Step 2, the color list of GIF image is encrypted; The described color list of GIF image is encrypted according to the following steps:
[0075] Set the key stream as K={K n ∣0n <1}, n is a positive integer, and the key stream is obtained by iterative piecewise linear chaotic map, which is prior art and can be accurately understood by those of ordinary skill in the art, so it will not be explained too much here; set the GIF image Each color component in the color list of is T(x,y), T(x,y)∈[0,255], x, y are integers and x∈[0,255], y∈[0,2];
[0076] The value K in the keystream n Multiply by 255 and round to get K n '; Set the color list of the encrypted GIF image as T'(x,y); calculate Get the color list of the encrypted GIF image;
[0077] The key strea...
Embodiment 2
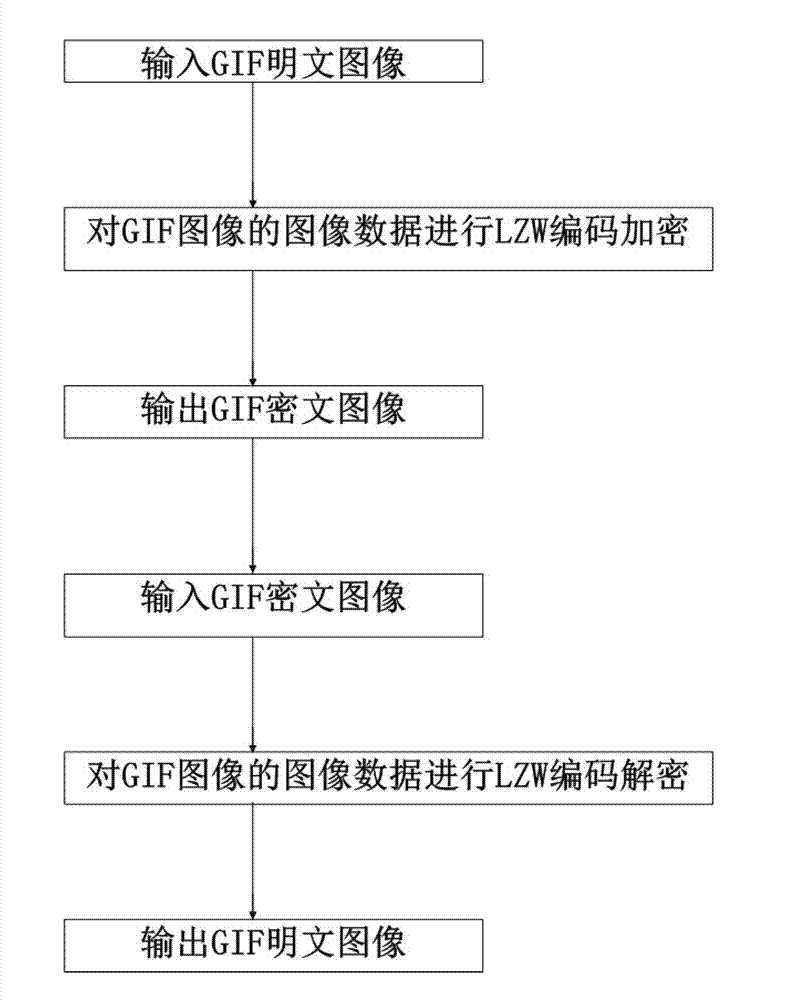
[0084] Embodiment two: if figure 2 Shown, a kind of GIF image encryption method based on compression coding comprises the following steps:
[0085] Step 1. Input the GIF plaintext image.
[0086] Step 2, carry out LZW encoding encryption to the image data of GIF image: described carry out LZW encoding encryption to the image data of GIF image and carry out as follows:
[0087] S1. Initialize the dictionary and scramble the dictionary; wherein the scrambling of the dictionary is performed according to the following steps:
[0088] A1, initialize the dictionary so that the dictionary contains all single characters;
[0089] A2. Set the index of the element currently to be scrambled as i, and initialize the value of i to the number len of elements contained in the current dictionary;
[0090] A3. Calculate r is a random number; exchange the elements of i and r in the dictionary;
[0091] A4. Calculate i'=i-1; when i'≥2, return to step A2, otherwise end scrambling.
[0092...
Embodiment 3
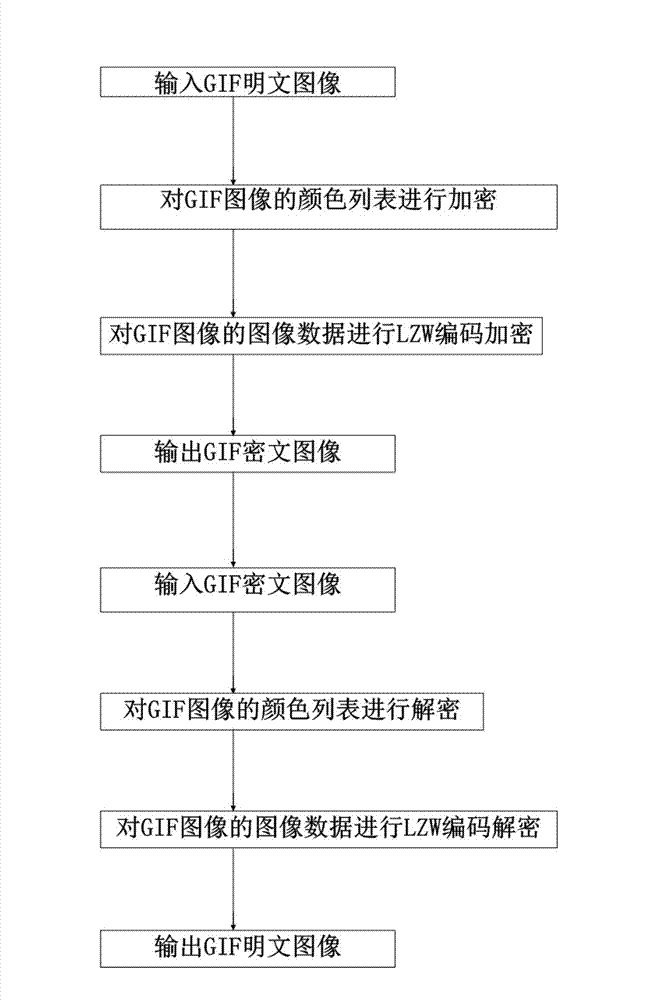
[0119] Embodiment three: as image 3 Shown, a kind of GIF image encryption method based on compression coding comprises the following steps:
[0120] Step 1. Input the GIF plaintext image;
[0121] Step 2, encrypt the color list of the GIF image and carry out LZW encoding encryption to the image data of the GIF image:
[0122] The described color list of the GIF image is encrypted according to the following steps:
[0123] Set the key stream as K={K n ∣0n <1}, n is a positive integer; the key stream is obtained by iteration of the piecewise linear chaotic map, and each color component in the color list of the GIF image is set as T(x, y), T(x, y)∈[ 0,255], x, y are integers and x∈[0,255], y∈[0,2];
[0124] The value K in the keystream n Multiply by 255 and round to get K n '; Set the color list of the encrypted GIF image as T'(x,y); calculate Get the color list of the encrypted GIF image;
[0125] The image data of the GIF image is carried out to LZW encoding and encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com