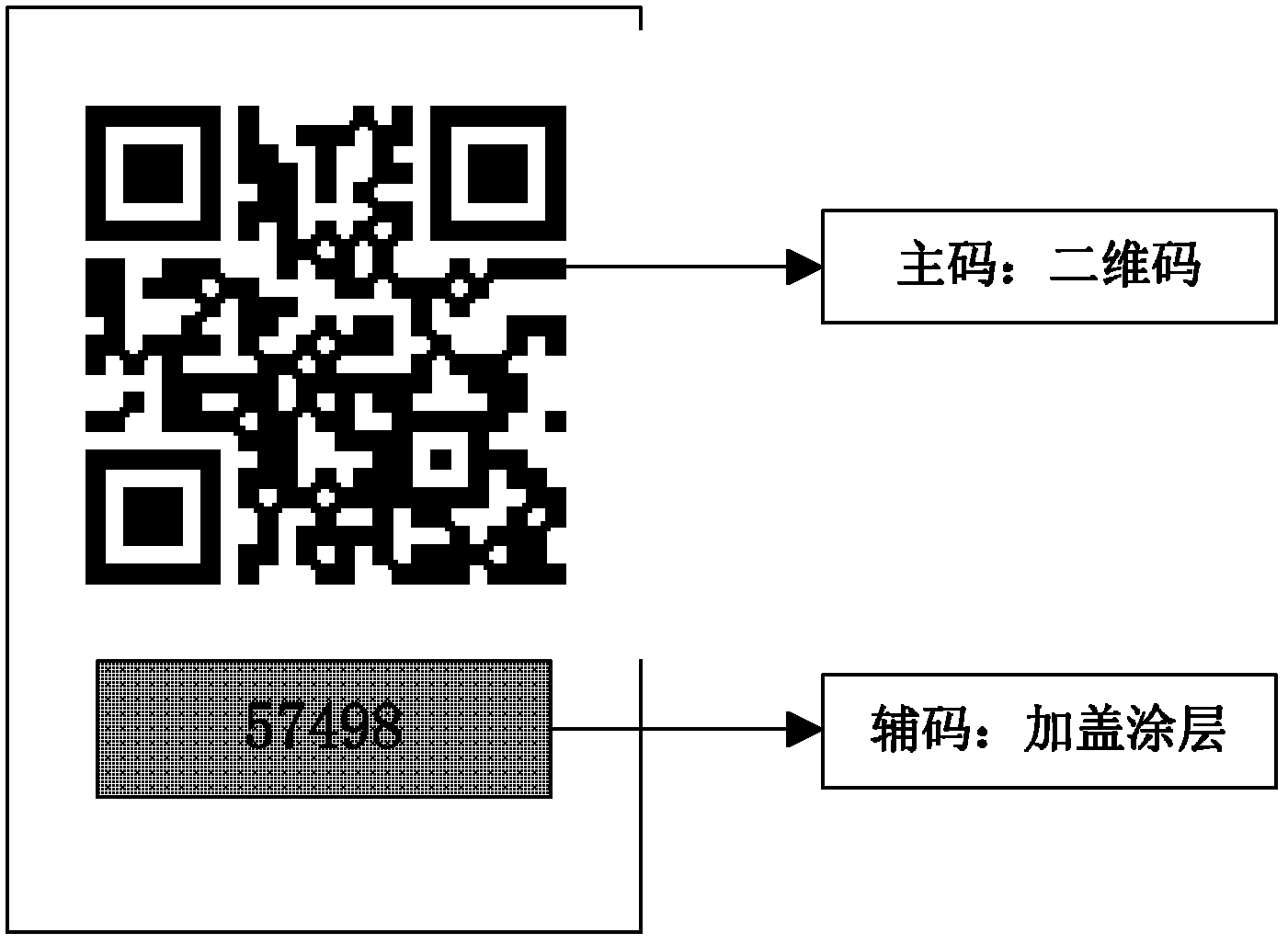
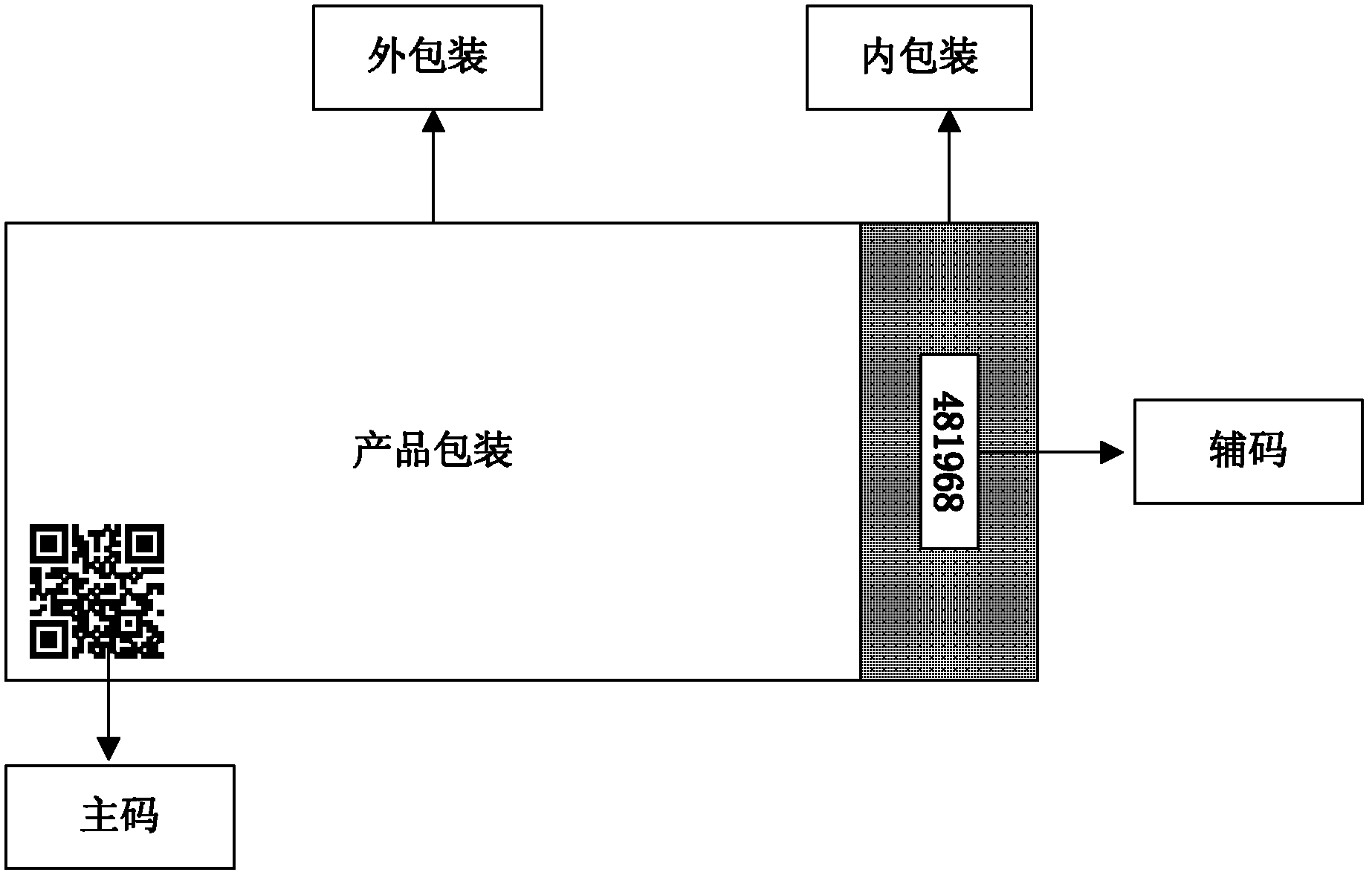
Two-dimensional code-based object identity dual-code identification method
A two-dimensional code and article technology, which is applied in the field of anti-counterfeiting and identification, can solve the problems of not being able to use coating to cover, increase the complexity of production process and production cost, increase the risk of counterfeiting, realize product anti-counterfeiting and integral management, and simplify The effect of the production process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
application example 1
[0047] Application example 1: product anti-counterfeiting
[0048] Currently, two-dimensional code recognition software installed on smart terminals is becoming more and more popular. Some people have proposed the technical idea of using two-dimensional codes for product anti-counterfeiting, but the common practice is to cover all or part of the coating on the two-dimensional code. QR code, and submit the data to the background database to verify the authenticity of the item. This simple two-dimensional code anti-counterfeiting method cannot solve the anti-counterfeiting query problem before the user purchases the product, so the user's enthusiasm for using it is not high.
[0049] In the double-code identification method provided by the present invention, the user can know the authenticity of the product before purchasing, and can also verify the auxiliary code after purchasing. The specific operation process is as follows:
[0050] (1) The user uses an intelligent termi...
application example 2
[0056] Application Example 2: Points Management
[0057] In order to encourage consumers to conduct anti-counterfeiting inquiries, the anti-counterfeiting inquiry of auxiliary codes and point management can be combined, so that users can obtain consumption points when conducting anti-counterfeiting inquiries, thereby greatly enhancing consumers' inquiry enthusiasm.
[0058] The operation process of point management is as follows:
[0059] (1) The user uses an intelligent terminal with two-dimensional code recognition software to take pictures of the two-dimensional code generated by the main code;
[0060] (2) Send the identified main code data content to the background server through the wired / wireless network for verification;
[0061] (3) The background server returns the operation page with the auxiliary code input box, prompting the user to input the auxiliary code;
[0062] (4) The user enters the auxiliary code, and after clicking Confirm, the data is sent to the back...
application example 3
[0065] Application Example 3: Item Uniqueness Authentication
[0066] With the development of the national economy, users have more and more demands for collectibles. An important feature of collectibles is the need to ensure the uniqueness of items, which is the key to maintaining and increasing the value of collectibles. Users hope that it is easy to identify the authenticity of collectibles, and manufacturers also hope that their own collectibles will not be counterfeited. The double-code identification method provided by the present invention has a good uniqueness authentication function of items, and can be applied to authenticity authentication of collectibles. The specific operation process is as Figure 7 shown, including the following steps:
[0067] (1) The user uses an intelligent terminal with two-dimensional code recognition software to take pictures of the two-dimensional code generated by the main code;
[0068] (2) Send the identified main code data content...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com