Data integrity verification method suitable for embedded processor
An embedded processor and data integrity technology, applied in the direction of electrical digital data processing, instrumentation, error detection/correction, etc., can solve the problem of high cost of missing, unable to meet the requirements of embedded system applications, and the number of hash tree layers , many nodes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] Below in conjunction with accompanying drawing and example the present invention is described in further detail.
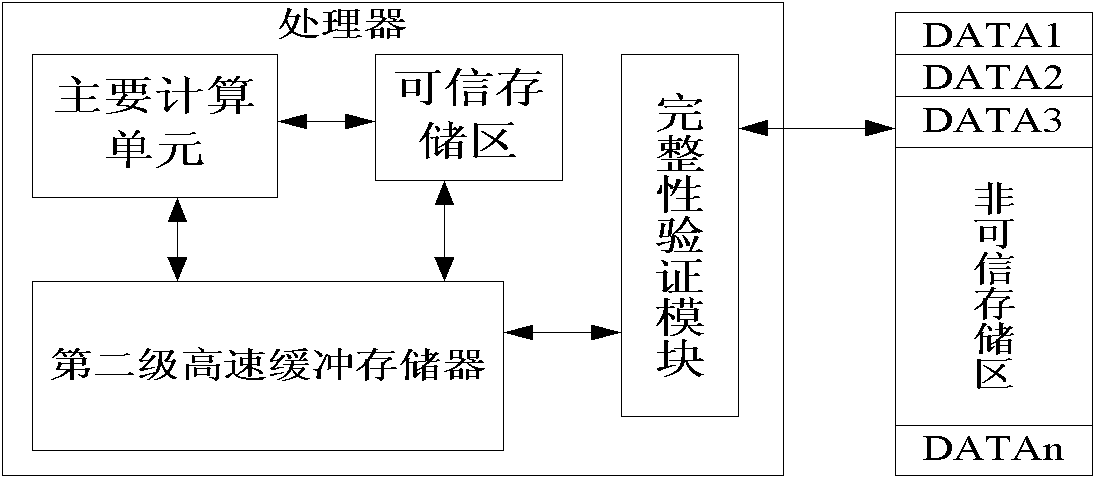
[0067] figure 2 A schematic diagram of the location of the data integrity verification method provided by the present invention in the overall architecture of the processor, that is, to implement this method requires an additional integrity verification module in the existing processor. figure 2 The non-trusted storage area refers to the memory outside the processor chip, and the trusted storage area refers to the memory inside the processor chip.
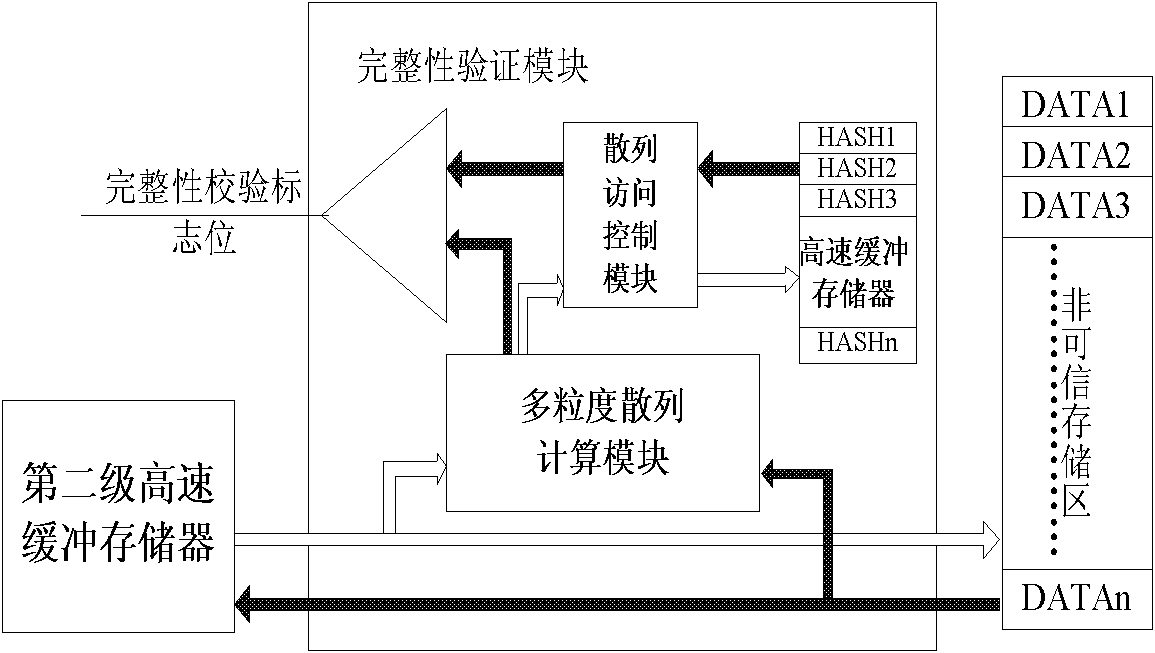
[0068] Such as image 3 As shown, a cache memory is introduced in the integrity verification module for storing node values of the hash tree, hereinafter referred to as the hash cache. In addition, the integrity verification module also includes two parts, which are the multi-granularity hash calculation module and the hash access control module. The multi-granularity hash calculation module is a circuit ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com