Anti-theft protection method for network pictures based on Flash embedded browser
An embedded browser, browser technology, applied in digital data protection, program/content distribution protection, instruments, etc., to achieve the effects of easy popularization, high image fidelity, and protection of interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
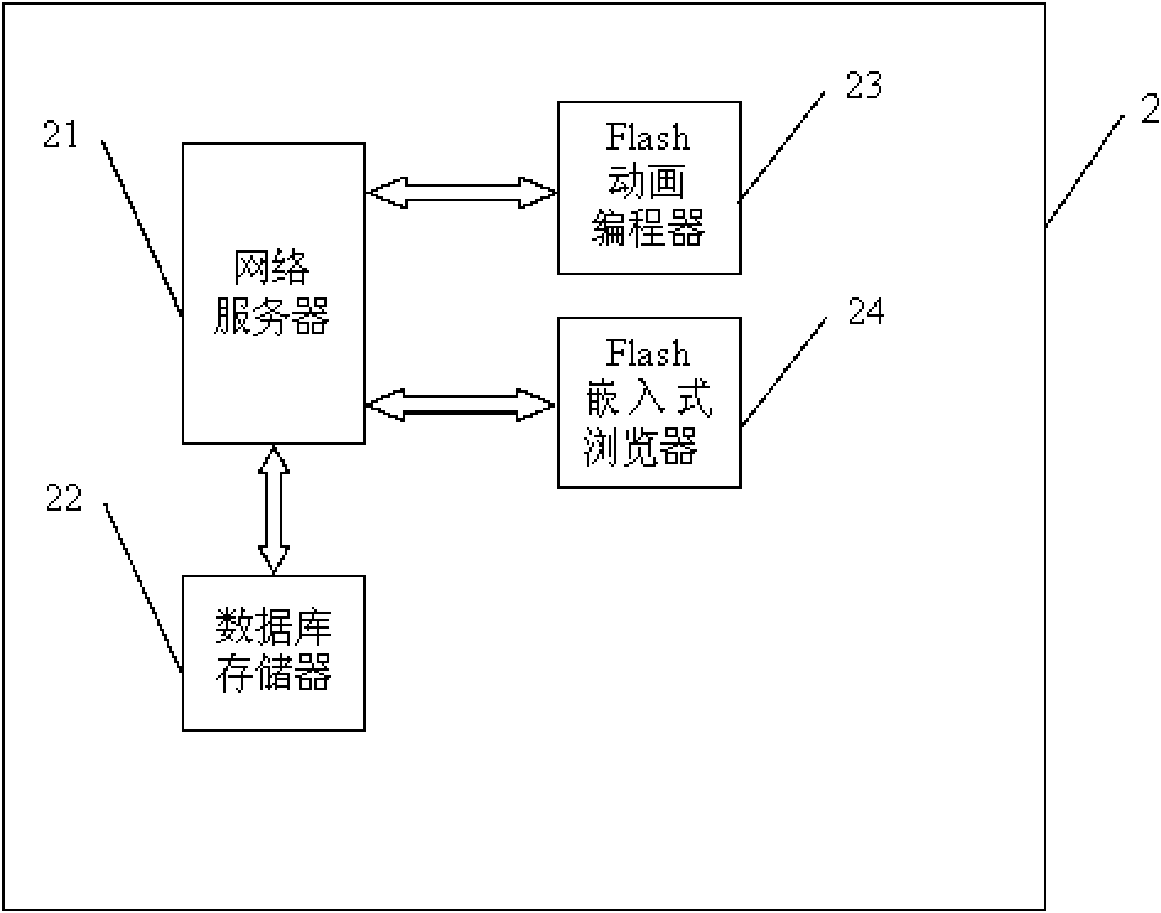
[0066] Embodiment 1: as figure 2 As shown, the network picture anti-theft protection system 2 includes a web server 21, on which the picture anti-theft protection system program is configured and a Flash plug-in and a database memory 22 are installed. The Flash plug-in further includes a Flash animation programmer 23 and a Flash embedded browser 24 . The Flash embedded browser 24 here is a special Flash picture browser, which uses one or more browsers among InternetExplorer, Maxthon, TheWorld, Tencent Traveler to realize embedding, and it supports common pictures such as JPG, BMP, GIF Format. The picture anti-theft protection system program further includes a dynamic reading protection module, an access timeout protection module, a local cache protection module, an address failure protection module, an address encryption protection module, and a picture viewing interference protection module.
[0067] The dynamic reading protection module is used to provide dynamic reading ...
Embodiment 2
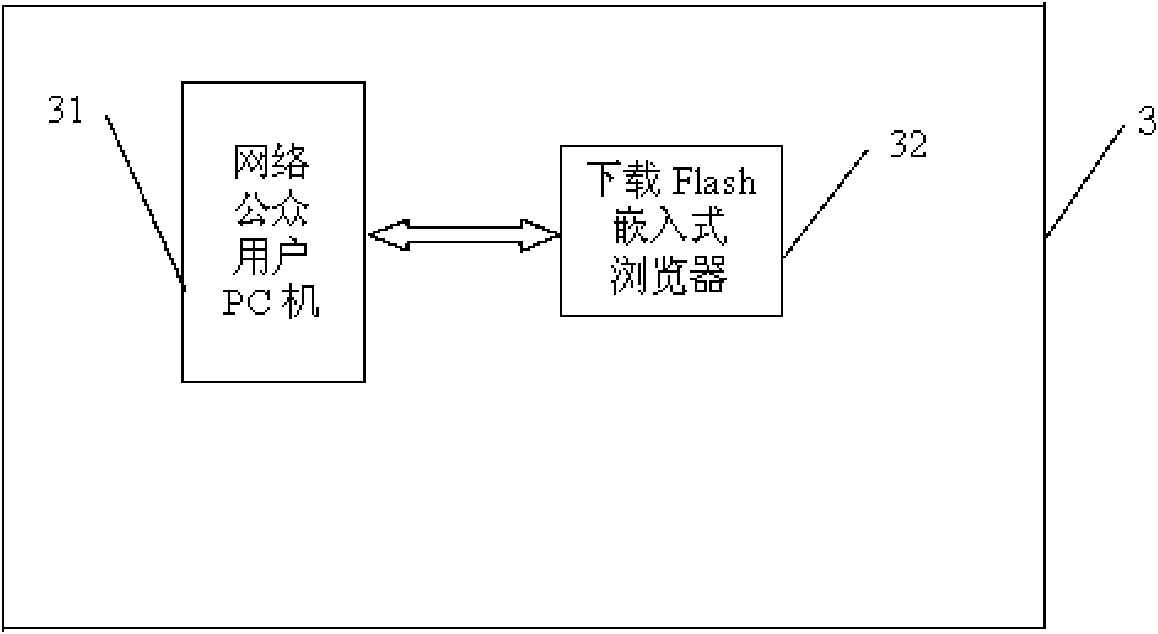
[0118] Embodiment 2: network picture anti-theft system client 3 comprises network public user PC, it can download and install Flash embedded browser 32 automatically after it opens the webpage of above-mentioned professional visualization network platform, embedded in the webpage of professional visualization network platform a plurality of embeddings image browser. All the other are with embodiment 1.
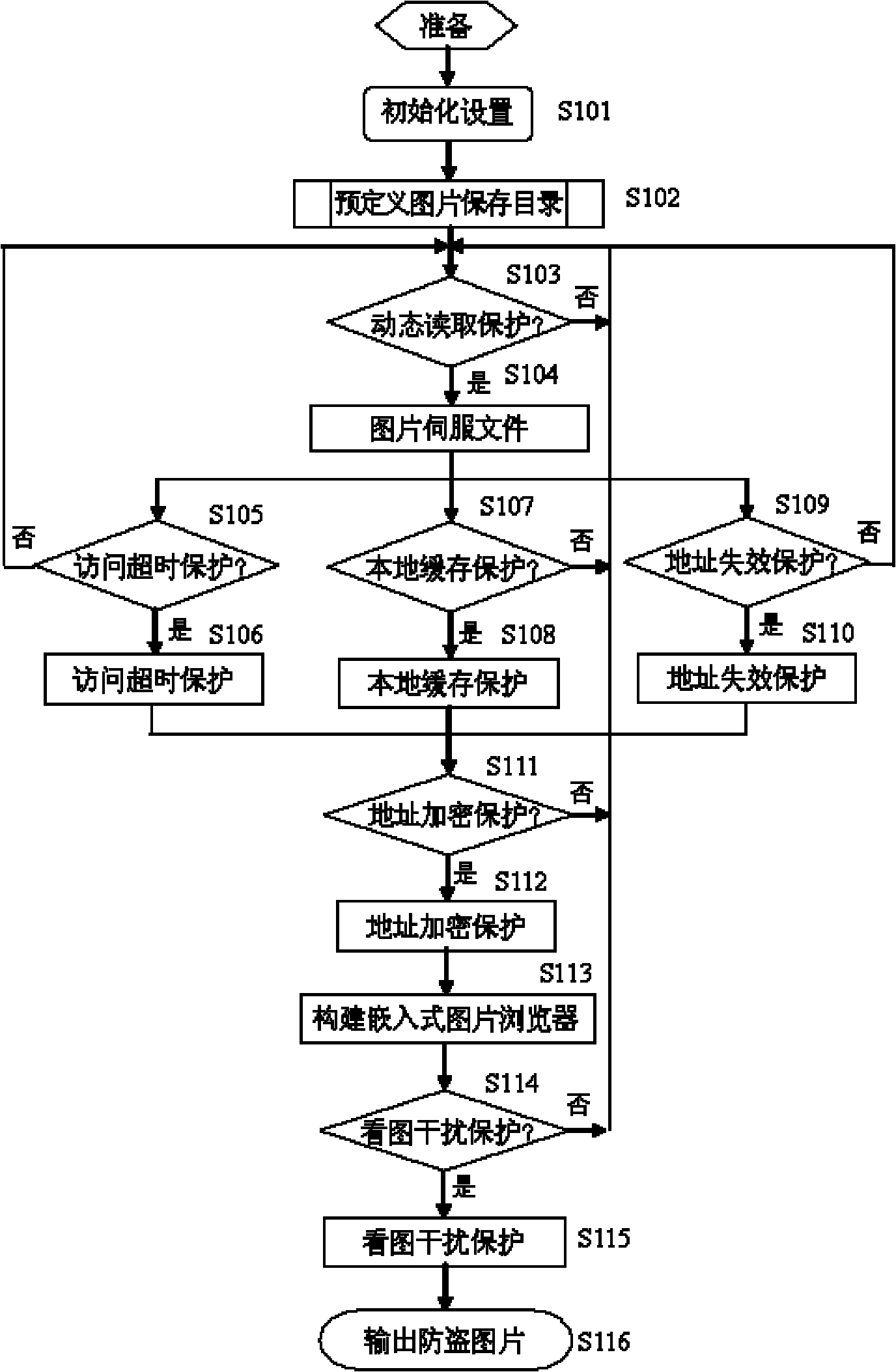
[0119] control figure 1 The shown flow chart of the network picture anti-theft protection program based on the Flash embedded browser is explained as follows:
[0120] (1) Dynamic reading protection: general network resources are stored in the WWW directory, open to any user on the Internet. If the image resource is stored in this way, the possibility of being stolen will be greatly increased; in order to avoid this problem and continue to ensure the public display of the image, this method adopts a dynamic response strategy: the image is stored in a folder other than the WW...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com