Divulging secret prevention U disk
An anti-leakage and privacy technology, applied in the direction of information storage, static memory, digital memory information, etc., can solve the problems of leaking enterprises, file proliferation, and difficulty in ensuring information security, so as to prevent illegal leakage and prevent the spread of malicious programs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
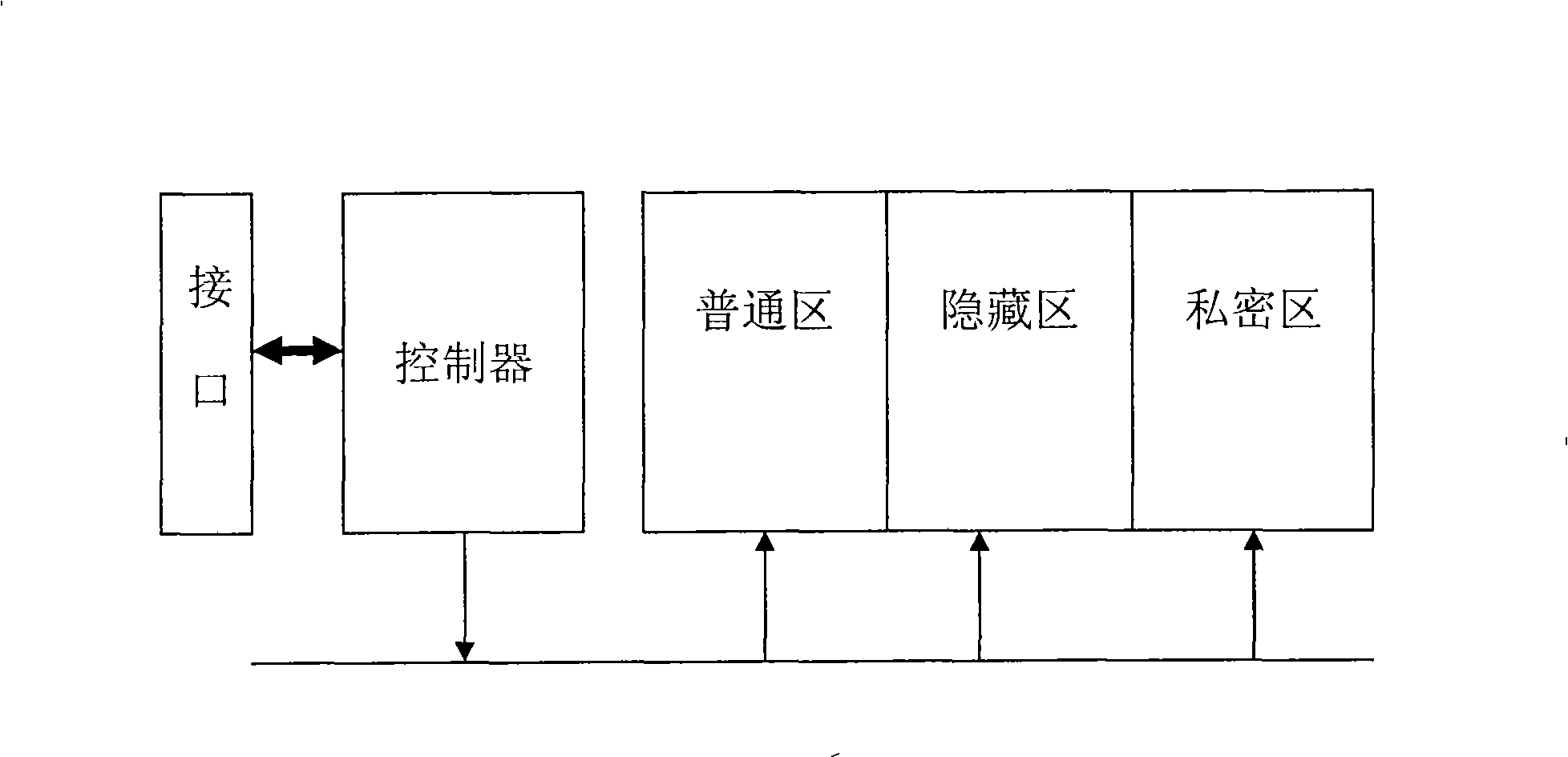
[0008] Comparing with accompanying drawing 1, its structure is that the output / input end of the USB control interface is connected with the input / output end of the controller correspondingly;
[0009] The USB control interface sets the data partition of the Flash memory, and the data partition includes a common area, a hidden area, and a private area.
[0010] The common area is implanted with a login program, and the common area is set as read-only. It makes it impossible for malicious programs to infect.
[0011] The said private area is to store user information and user authentication information, which cannot be read.
[0012] What is said is that the hidden area is the information embedded in the monitoring program, which is also unreadable.
[0013] Described controller uses USB controller (model CBM209X).
[0014] When in use, set the interface access password, so that malicious programs and non-administrators cannot directly read and write the data area of the U ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com