Method and device for authorizing userí»s terminal in CDMA system
A user terminal, authentication technology, applied in the field of communication, can solve the problem of not finding relevant methods and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
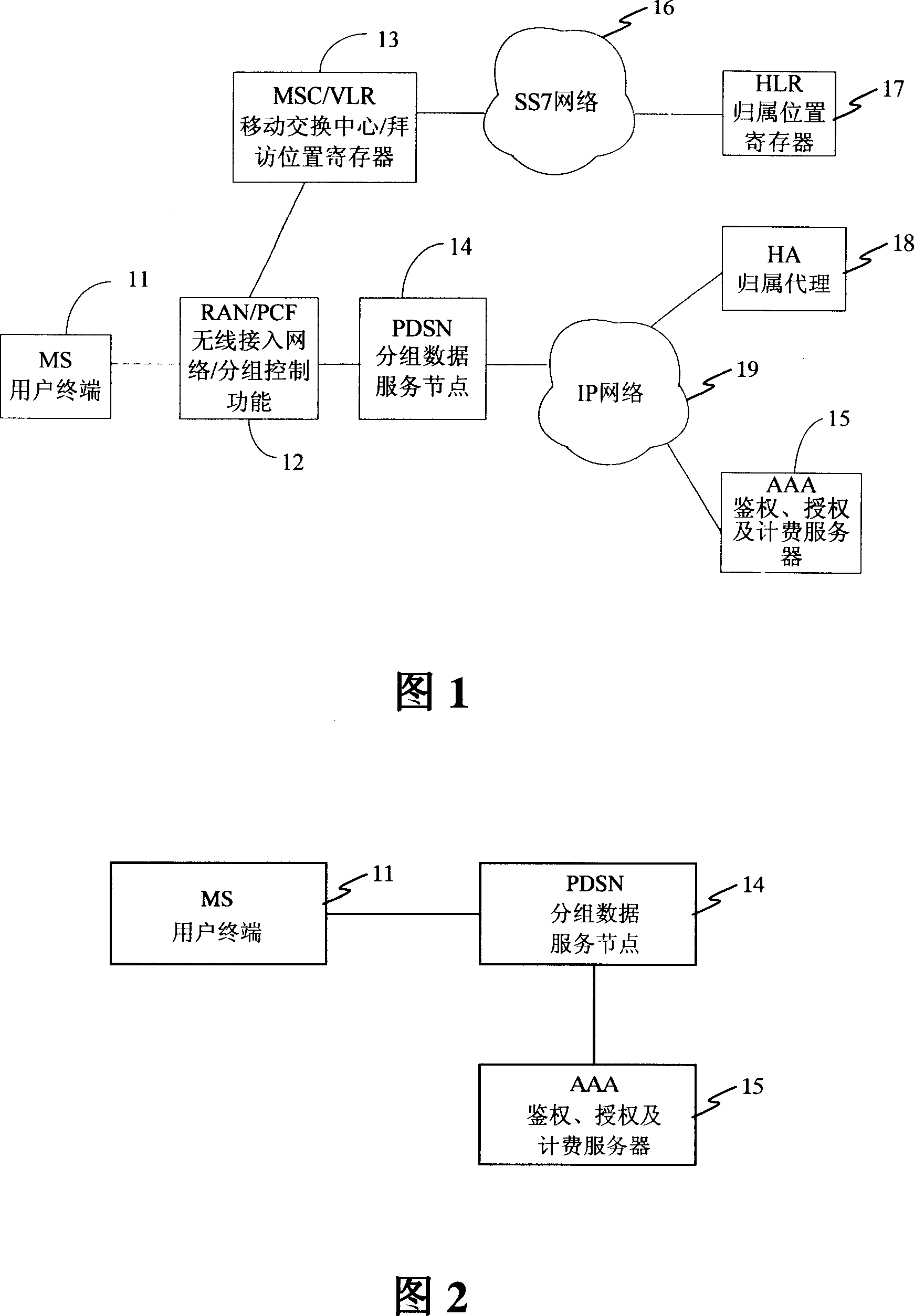
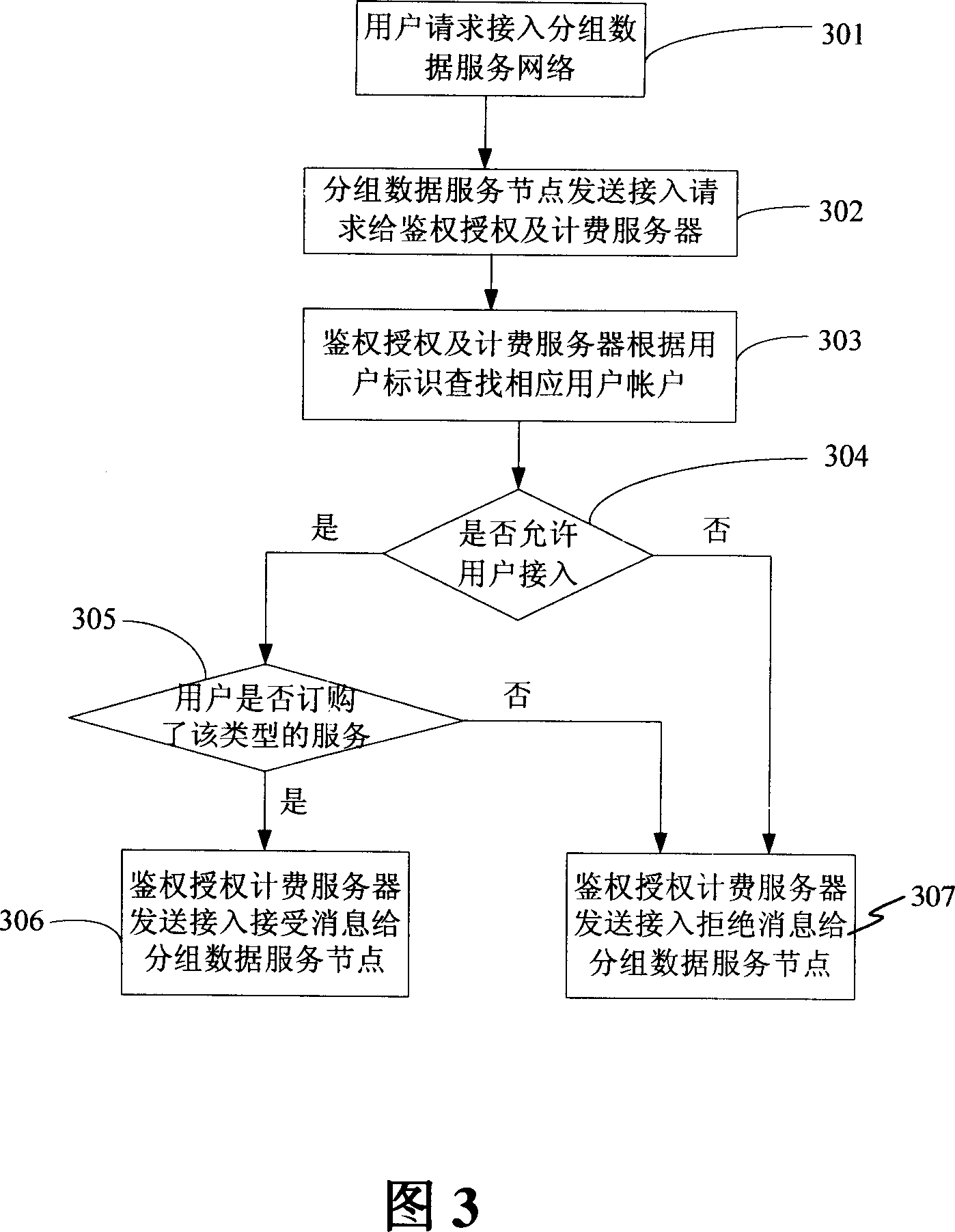
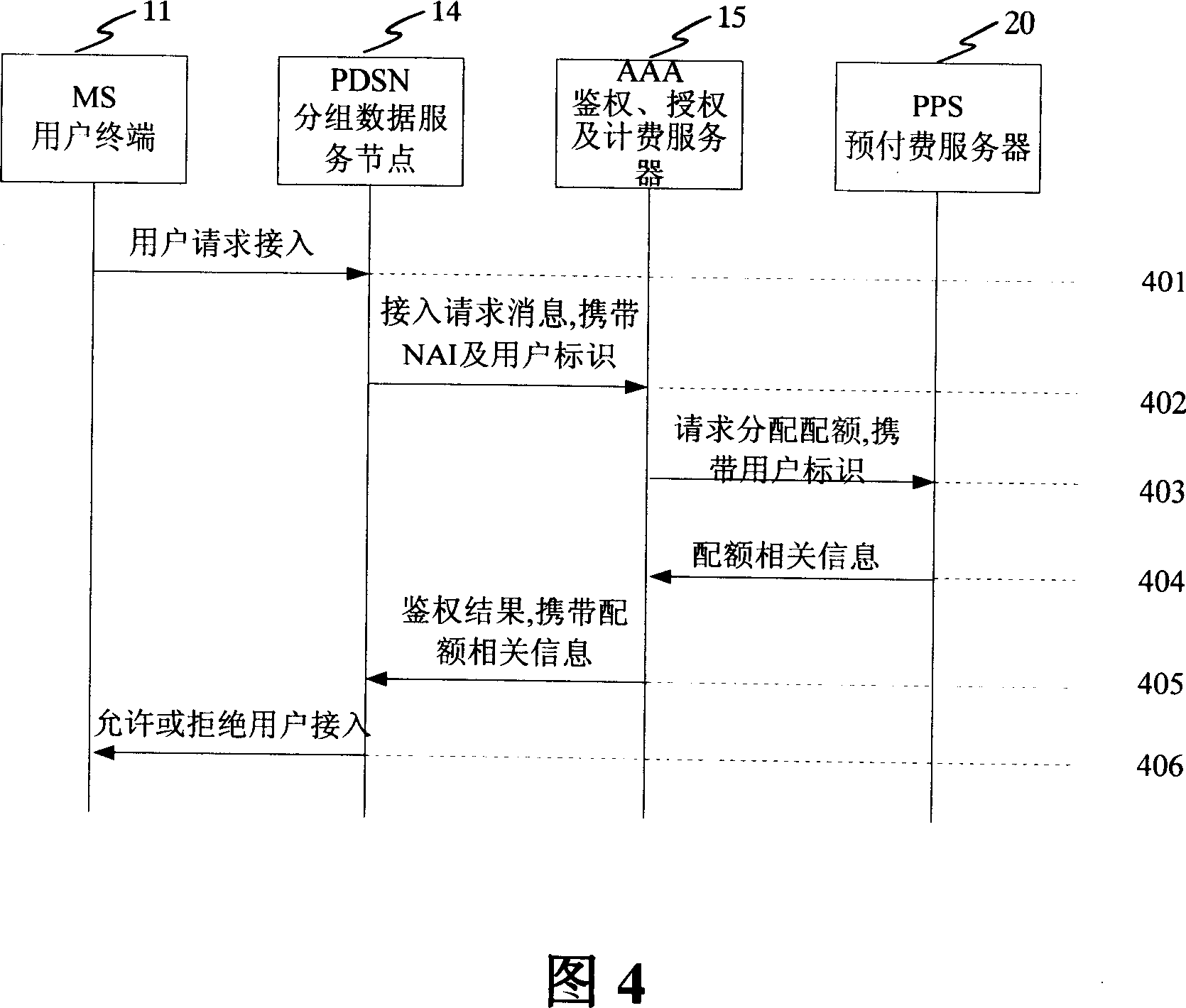
[0034] Please refer to FIG. 1 , which is a network structure diagram of an existing CDMA system. The structure includes: user terminal MS (Mobile Station) 11, Radio Access Network / Packet Control Function (Radio AccessNetwork / Packet Control Function, RAN / PCF) 12, Mobile Switch Center / Visit Location Register (Mobile Switch Center / Visit Location Register) , MSC / VLR) 13, packet data serving node PDSN 14, authentication, authorization and accounting server AAA 15.
[0035] MS 11 uses a public account to access the CDMA packet domain.
[0036] RAN / PCF 12 forwards the user's data service access request to PDSN 14 .
[0037] PDSN 14 provides data access service for MS 11, and provides authentication for the user when MS 11 accesses. At the same time, PDSN 14 collects user charging information when providing data access service for MS 11. The PDSN 14 is connected to a home agent HA (HomeAgent) 18 through an IP (Internal Protocol, Internet Protocol) network 19 .
[0038] MSC / VLR 13 pro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com