Abnormal detecting method based on fuzzy nervous network
A fuzzy neural network and anomaly detection technology, applied in data exchange network, data exchange through path configuration, digital transmission system, etc., can solve inflexibility and other problems, achieve the effect of reducing dimensionality and improving operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further elaborated below in conjunction with the accompanying drawings.
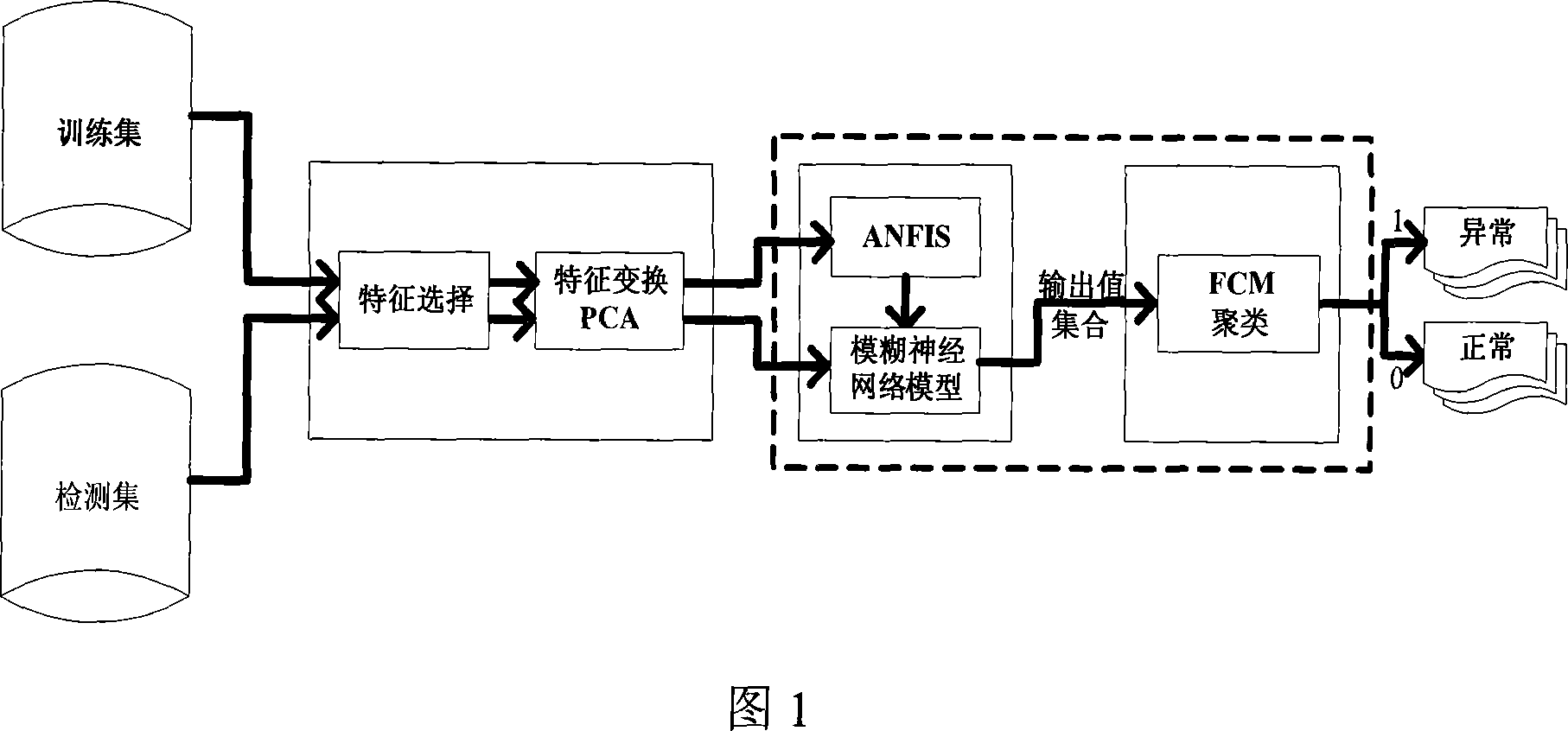
[0025] As shown in Figure 1, the anomaly detection method based on fuzzy neural network mainly includes two stages: training stage and detection stage. In the training stage, firstly, the input network connection vector is obtained from the network connection data vector training sample set, and then the feature vector is generated after feature selection and feature transformation, and then the feature vector is sent to the fuzzy neural network, using ANFIS, (Adaptive Fuzzy Neural Network Inference system) is trained until it reaches a stable state, and the fuzzy neural network model is obtained. In the detection stage, firstly, the input network connection vector is obtained from the network connection data vector training sample set, which is preprocessed to generate a feature vector, and then the feature vector is sent to the trained fuzzy neural network model to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com