Attack defending system and attack defending method
a technology of attack defense and system, applied in the field of security countermeasure technique in the computer network, can solve the problems of ineffective detection or defense of attacks, loss of network speed, and problems beyond conventional techniques, and achieve the effect of effective defens
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
first embodiment
[0104]1.1) Structure
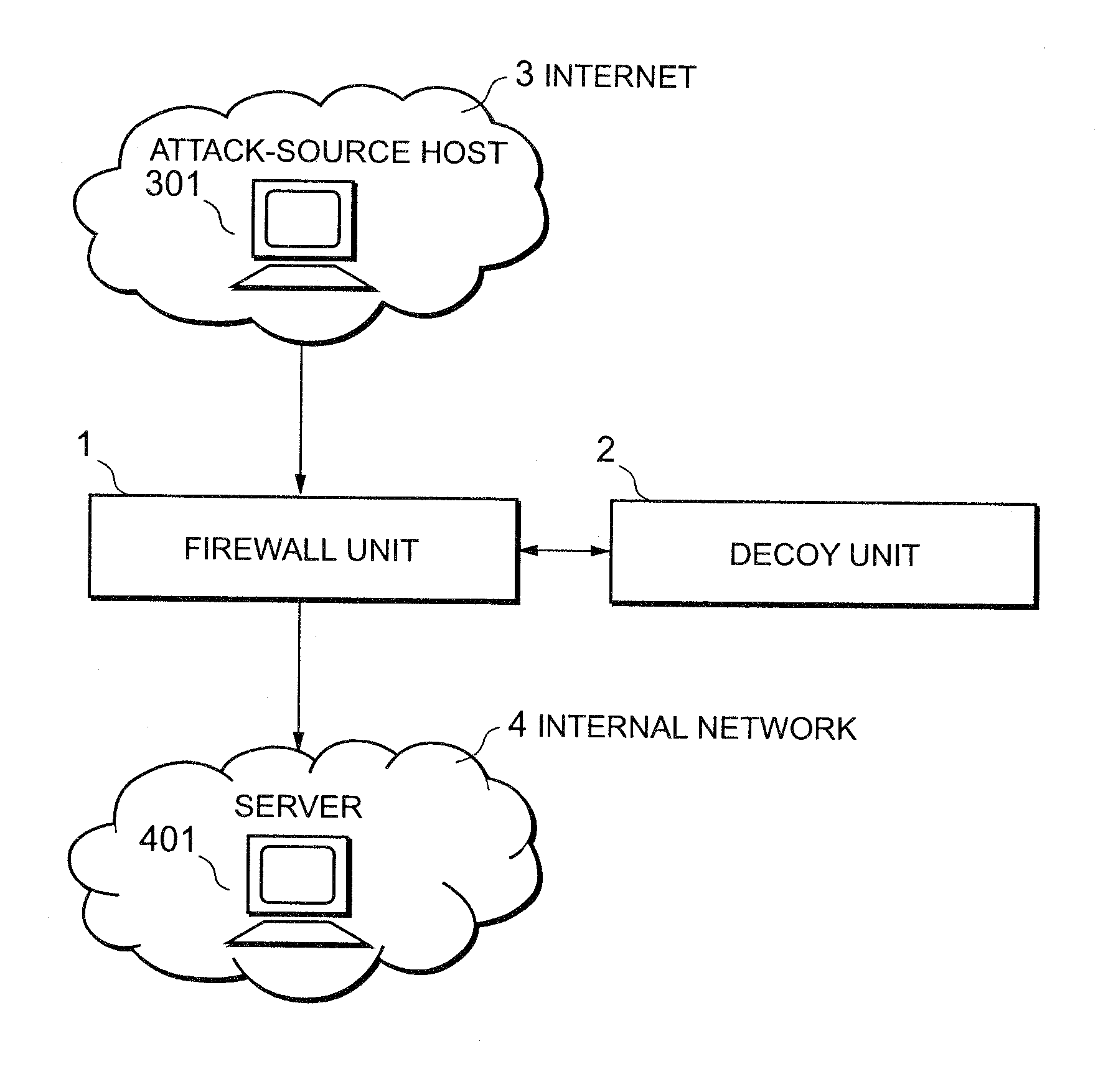
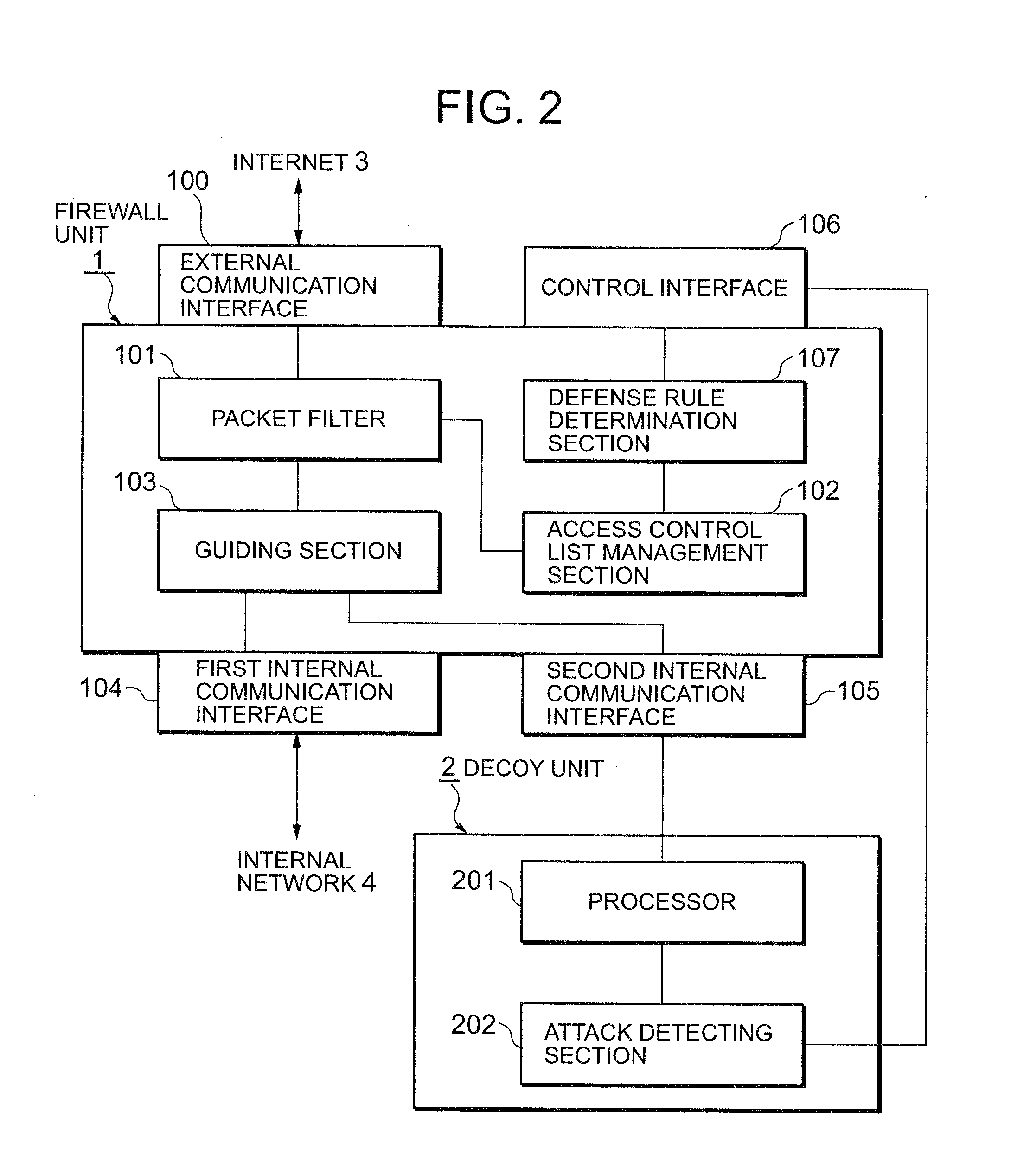
[0105]Referring to FIG. 2, the firewall unit 1 is connected with the Internet 3 through an external communication interface 100 and is connected with the internal network 4 through a first internal communication interface 104.
[0106]A packet filter 101 is connected between the external communication interface 100 and a guiding section 103, and executes packet filtering according to access control rules obtained from an access control list management section 102. As described later, the packet filter 101 transfers an IP packet received from one of the external communication interface 100 and the guiding section 103 to the other, or discards the received packet without transferring it.
[0107]A packet accepted by the packet filter 101 is sent to the guiding section 103. The guiding section 103 refers to a guiding list (FIG. 5), which will be described later, to guide the IP packet received from the packet filter 101 to either of the first internal communication interf...
second embodiment
[0159]2.1) Structure
[0160]Referring to FIG. 15, a firewall unit 5 according to a second embodiment of the present invention is provided with a confidence management section 502 added to the firewall unit 1 of the first embodiment as shown in FIG. 2, and is further provided with a guiding section 501 instead of the guiding section 103. The guiding section 501 is capable of determining a packet forwarding direction depending on a confidence level. Hereinafter, blocks similar to those previously described with reference to FIG. 2 are denoted by the same reference numerals and detailed descriptions on them will be omitted.
[0161]In FIG. 15, when having received a packet, the guiding section 501 outputs the source IP address of the received IP packet to the confidence management section 502 and obtains a corresponding confidence level. When having received the confidence level, the guiding section 501 compares the confidence level with a predetermined threshold value and, depending on its...
third embodiment
[0188]FIG. 22 shows a firewall unit of an attack defending system according to a third embodiment of the invention and FIG. 23 shows an example of the firewall unit. A firewall unit 6 in the third embodiment has the guiding section 501 and the confidence management section 502 which are connected as shown in FIG. 15 in addition to the guiding section 103 in the firewall unit 1 as shown in FIG. 2.
[0189]More specifically, as shown in FIG. 23, a second guiding section 501 may be provided as a subsequent stage of a first guiding section 103. To the contrary, the second guiding section 501 may be provided as a previous stage of the first guiding section 103.
[0190]In either of these structures, effective protection can be achieved against worm-like attacks carried out by randomly selecting IP addresses and active targeting attacks. Furthermore, even when a host is infected with a worm after the host has been trusted by the second guiding section 501, the decoy unit 2 can inspect whether a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com