Methods and Apparatus for Enabling Secure Network-Based Transactions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
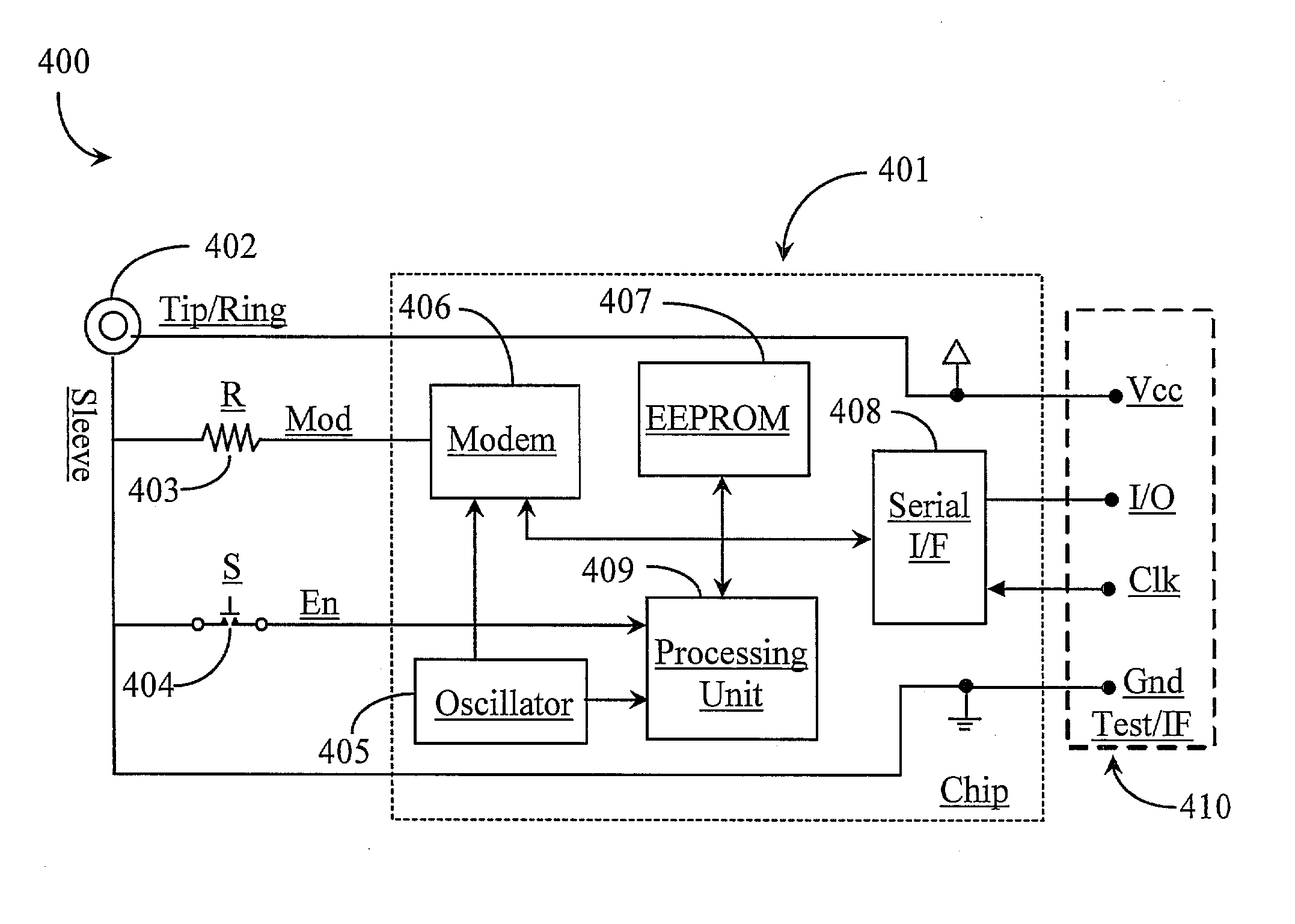
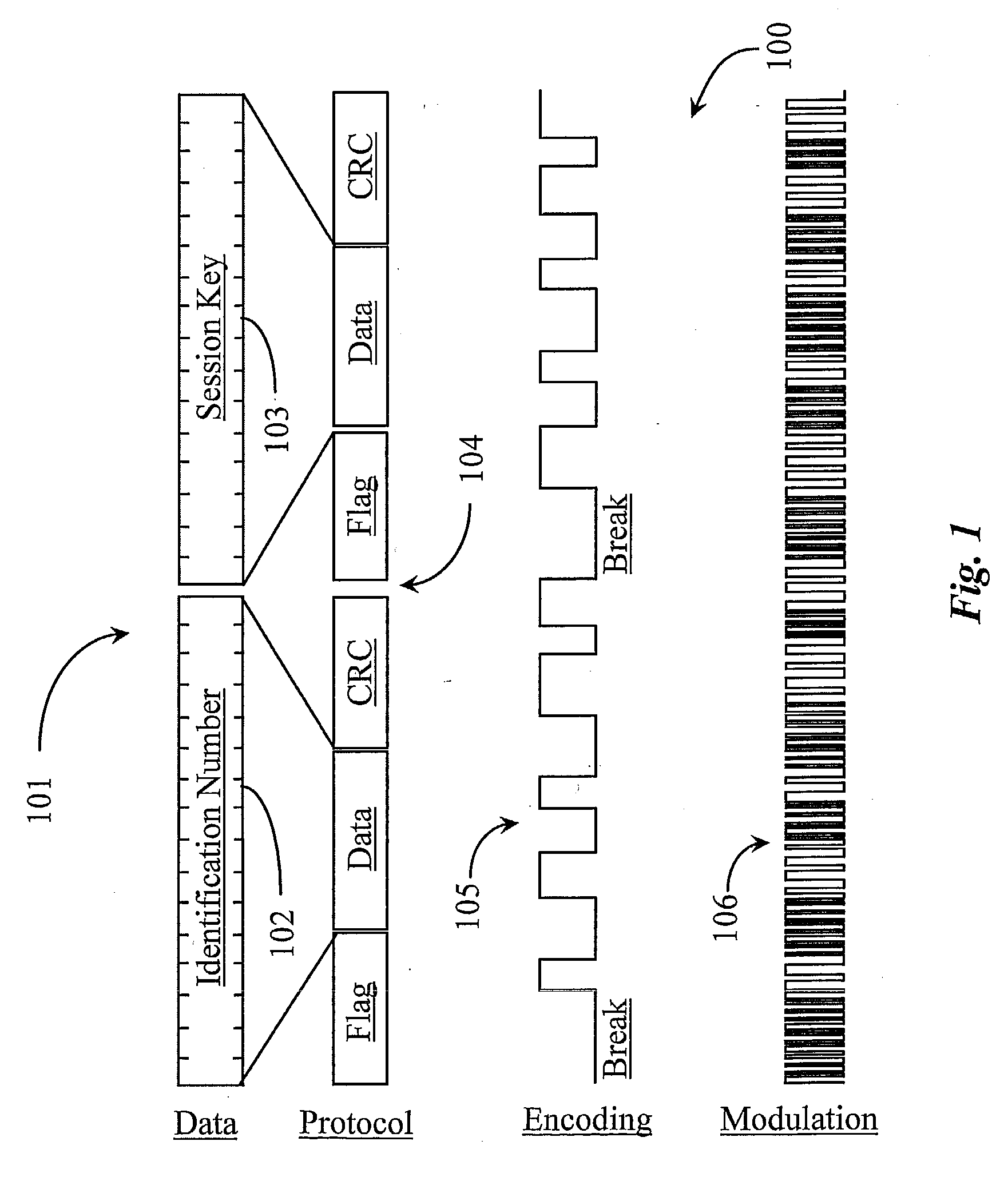
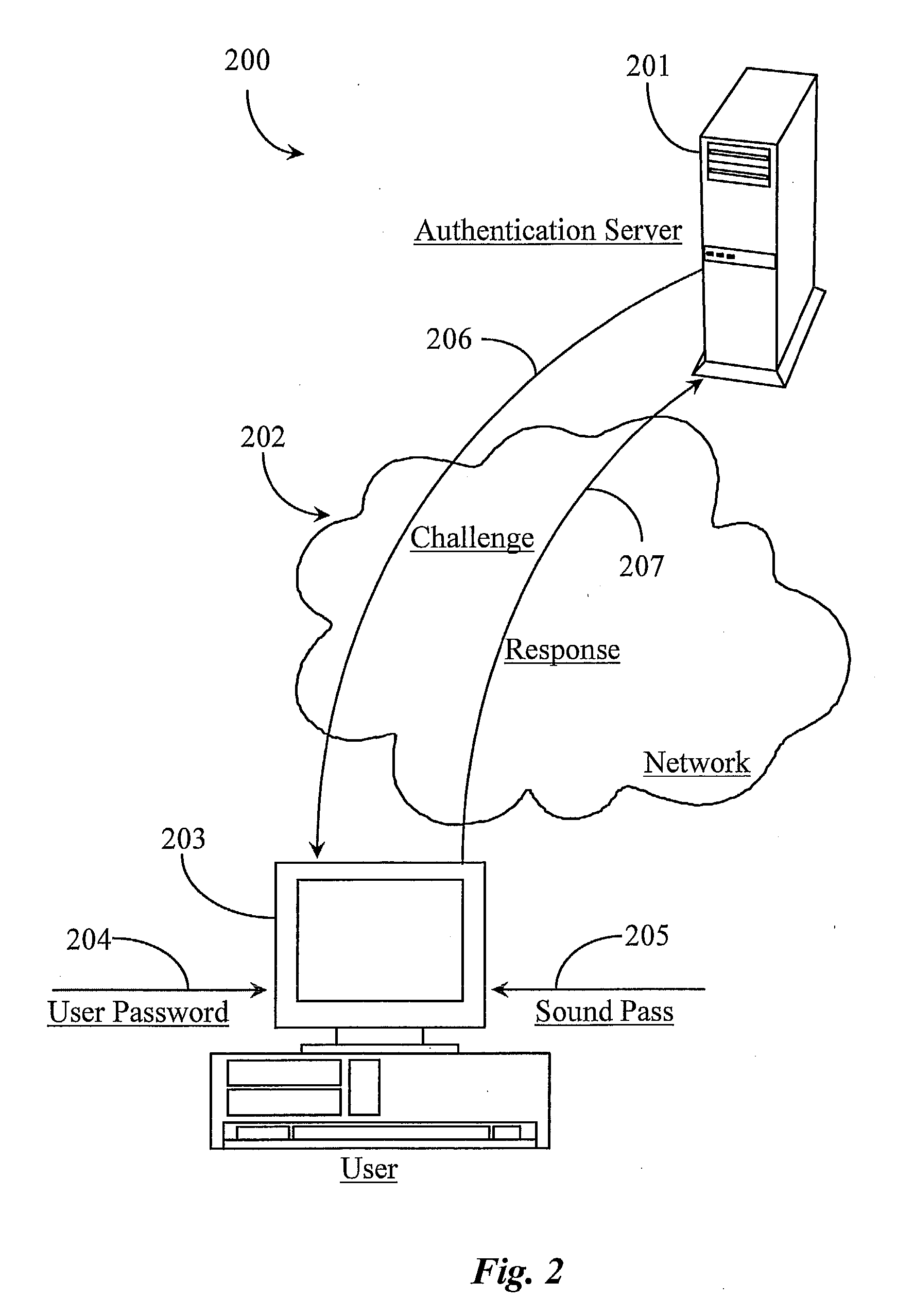
[0032] The inventors provide a system that may be used in a variety of ways using hardware and / or software to provide secure authentication over a network for users and user groups. The present invention is described according to various embodiments and in enabling detail supporting each of those embodiments. More particularly, the system uses a modulated sound consisting at least in part of an identification number and a session key.
[0033] It is important to note herein that in one embodiment, the identification number may, for example, contain 16 digits of data and may be a fixed identification number (ID) or on that is dynamically assigned. It may also be encoded to include an error detection bit. In this case the identification number may also be encrypted with a proprietary key to ensure the provider authorized to provide the software of the invention may practice the invention in a way that is functional.
[0034] The following example demonstrates a configuring and encryption ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com