Public key certificate state obtaining and verification method
A technology of public key certificate and verification method, which is applied in the field of obtaining and verifying the state of public key certificate in network communication, can solve the problems of complex use of the background technology, and achieve the goal of saving bandwidth and computing resources, ensuring freshness, and high security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
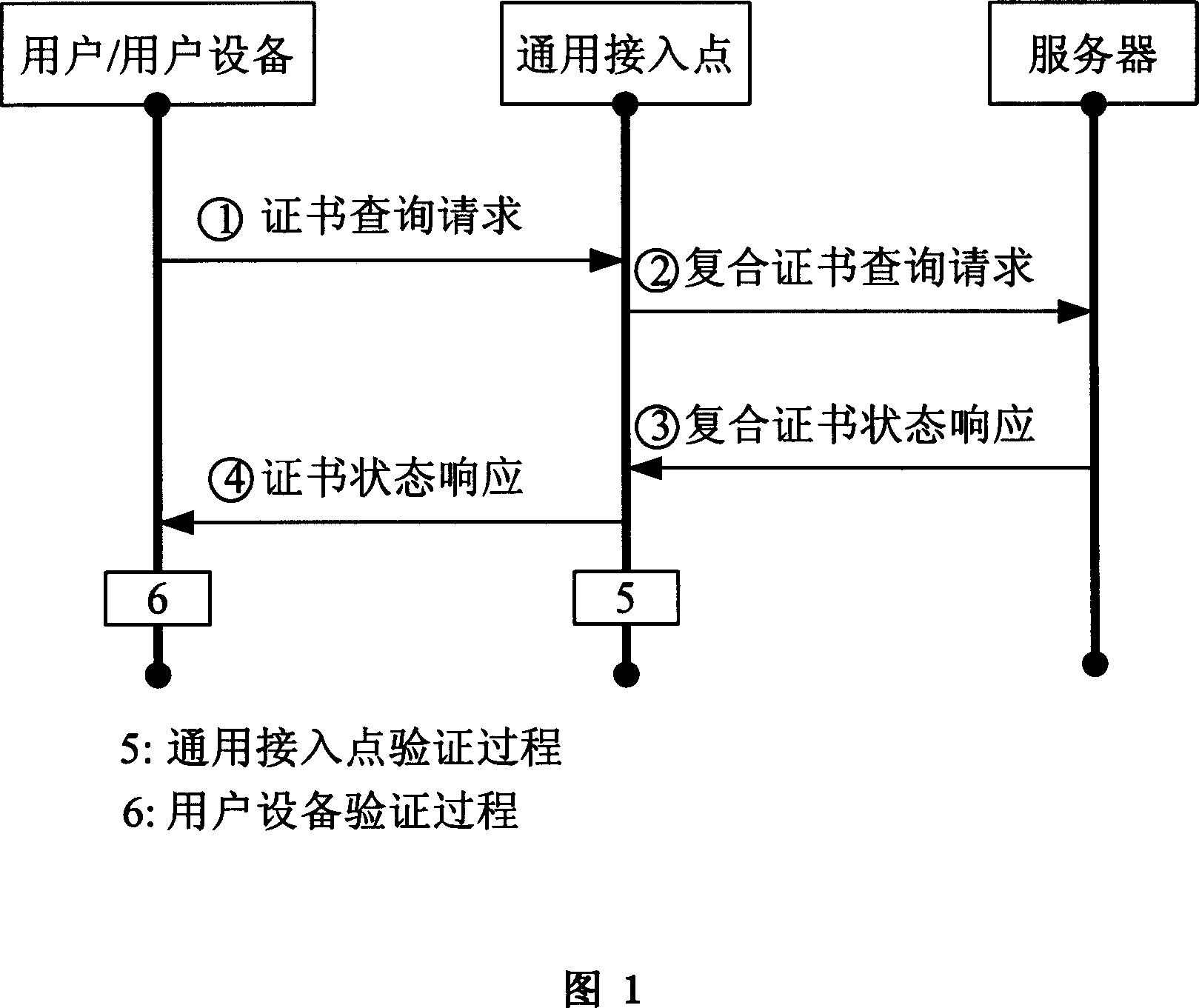
[0060] The participating entity user equipment, universal access point and server of the present invention have all been assigned public key certificates before running the method. The server may provide signatures of certificate authorities trusted by the user equipment and the universal access point respectively. After running this method, the user equipment and the universal access point can obtain the certificate of the other party, and verify the status of the certificate of the other party and itself. The user equipment and the universal access point can obtain their respective public key certificates and the state of the public key certificates of each other through the server. In the present invention,
[0061] m means message;
[0062] U_CA indicates the certificate authority trusted by the user device;
[0063] U_Cert represents the user equipment certificate stored locally by the user equipment;
[0064] U_CA_Cert represents the certificate of the certificate au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com