Tactics executing point and linking method of it and intrusion detection system
An intrusion detection system and policy execution technology, which is applied in the field of network security to prevent attacks, improve efficiency, and improve overall protection capabilities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
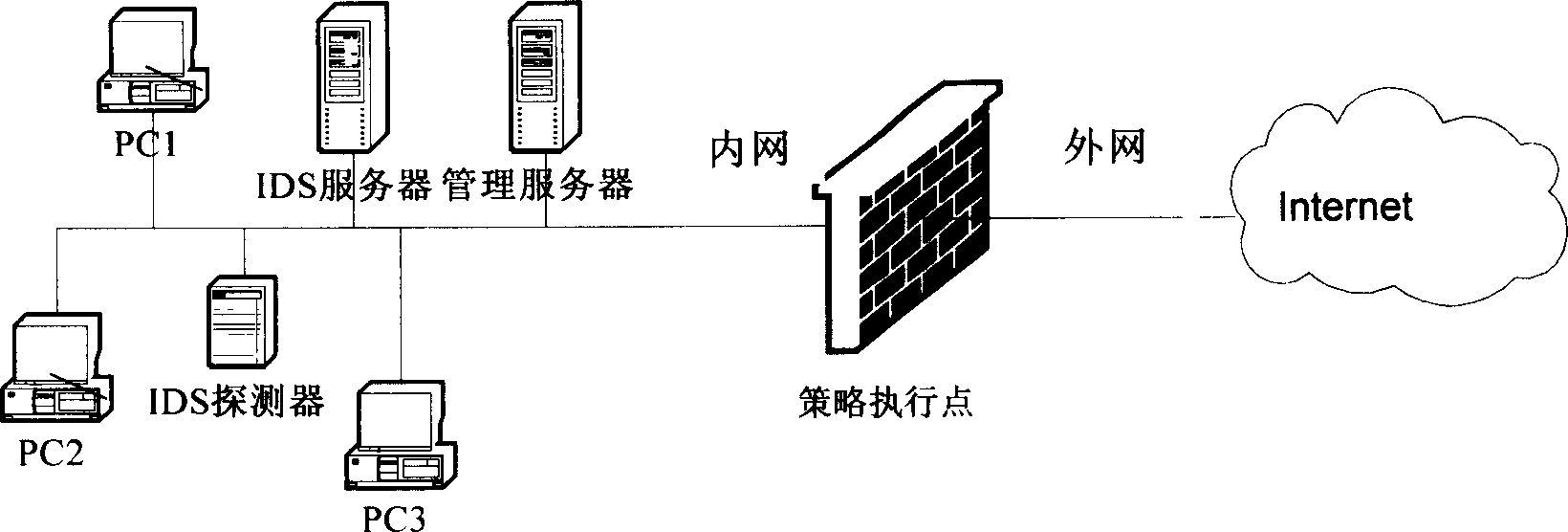
[0038] Such as figure 2 Shown: the present invention provides a method for linking a policy enforcement point with an intrusion detection system, comprising the following steps:
[0039] Establish a linkage connection directly between the intrusion detection system and the policy enforcement point;
[0040] Maintain communication between the policy enforcement point and the intrusion detection system;
[0041] The intrusion detection system detects the attack behavior, and the policy enforcement point responds to the attack processing result.
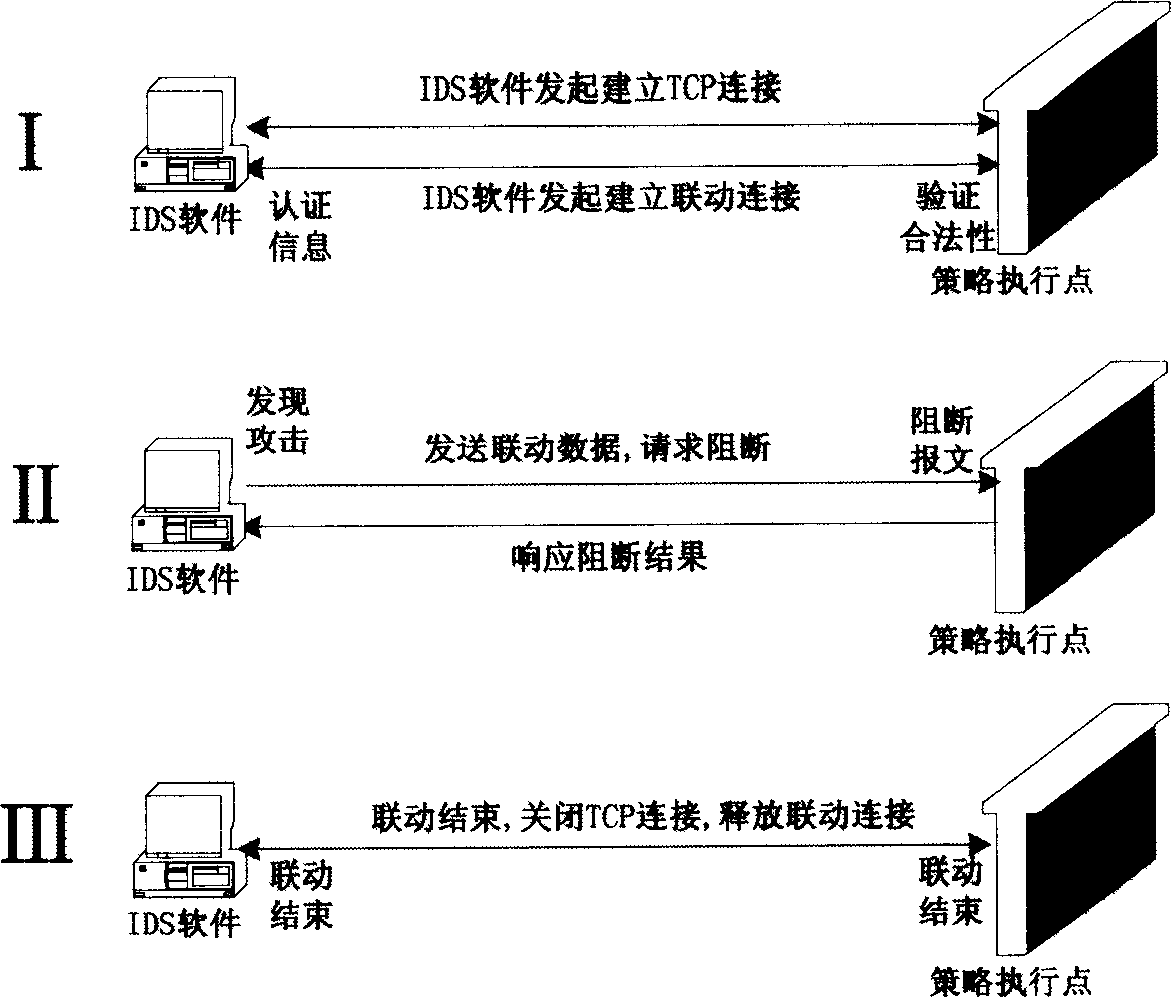
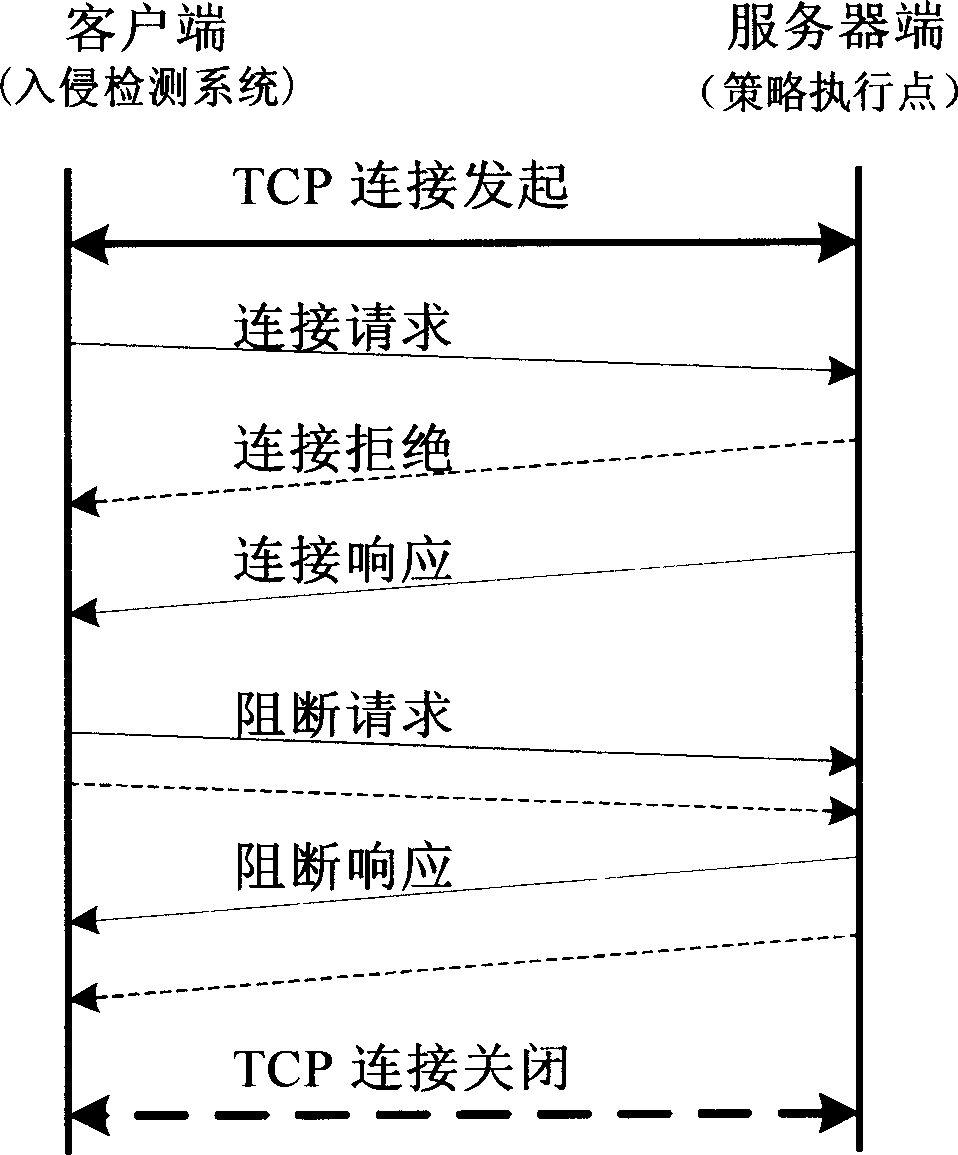
[0042] Further, the process of establishing a connection between the policy enforcement point and the intrusion detection system includes at least the following steps:
[0043] Step 1: The IDS software initiates the establishment of a linkage connection, initiates the linkage connection, and the connection request message carries the relevant information of the IDS software;
[0044] Step 2 The policy enforcement point checks the re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com