Information management system, information processor, and information management method
An information management system and information processor technology, applied in the field of information management systems, can solve the problems of lower security level and higher address book information processing efficiency, and achieve the effect of improving security level and processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
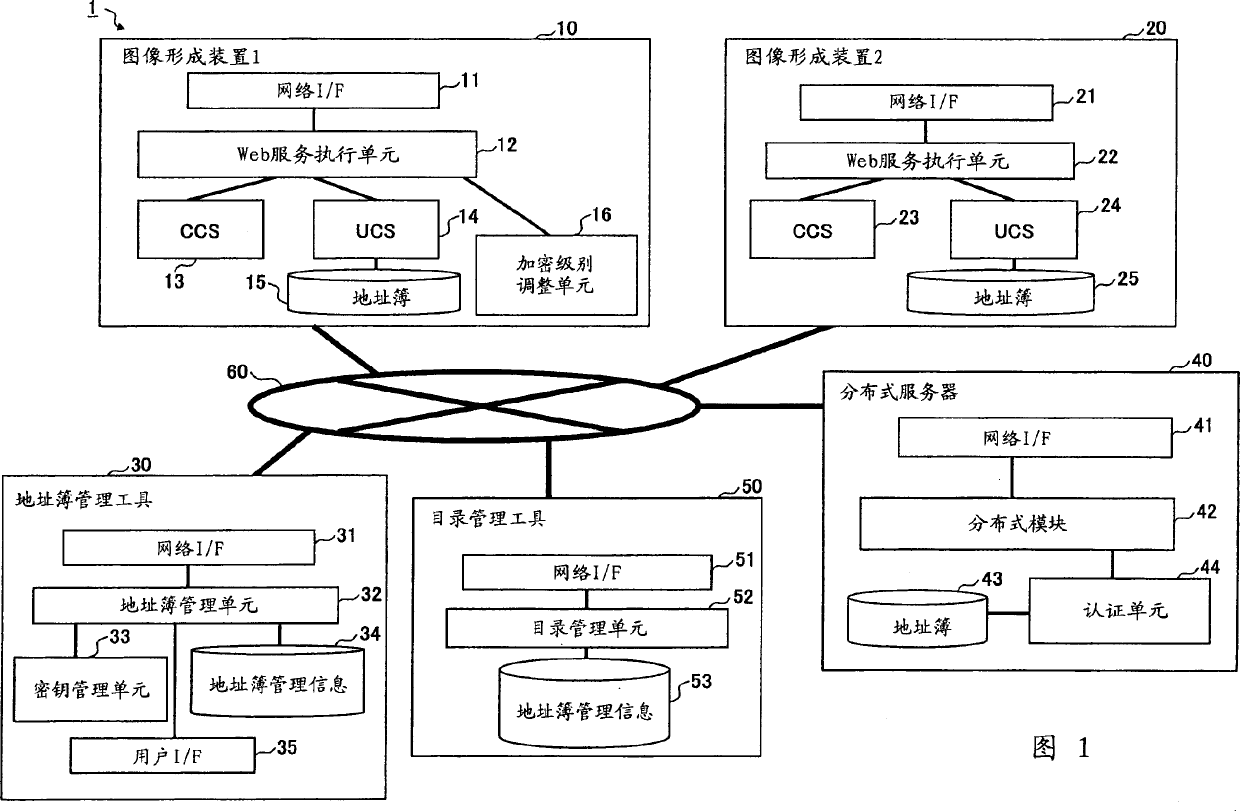
[0074] FIG. 4 is a sequence diagram showing processing performed by the address book management system 1 according to Embodiment 1 of the present invention. The sequence diagram shows an example of transferring a key when transferring address book information. Here, it is assumed that the image forming apparatus 10 and the image forming apparatus 20 use the same encryption system and decryption system.
[0075] In step S1 , the user operates the operation panel 161 of the image forming apparatus 10 to instruct editing of user information contained in the address book 15 . In response to the guidance, the Web service execution unit 12 edits the user information contained in the address book 15 through the UCS 14 .
[0076] Next in step S2, the Web service execution unit 12 determines the encryption range, that is, whether to encrypt all address book information, or only encrypts the password; and uses the key A to perform encryption within a predetermined range.
[0077] FIG....
Embodiment 2
[0087] FIG. 6 is a sequence diagram showing processing executed by the address book management system 1 according to Embodiment 2 of the present invention. This sequence diagram shows an example in which the key C of the distribution server 40 is used as a public key (hereinafter referred to as a public key). Here, the distributed server 40 may be provided by (included in) the image forming apparatus 20 .
[0088] In step S20, the distributed server 40 executes administrator authentication processing and device capability acquisition processing. FIG. 7 is a sequence diagram of an example of administrator authentication processing and device capability acquisition processing.
[0089] Proceeding to step S31 , the distribution module 42 of the distribution server 40 transmits a manager authentication request to the image forming apparatus 10 through the network I / F 41 and the network 60 . Manager authentication information is included in the manager authentication request in s...
Embodiment 3
[0102] FIG. 8 is a sequence diagram showing processing executed by the address book management system 1 according to Embodiment 3 of the present invention. The sequence diagram shows an example in which the key C of the image forming apparatus 10 is used as the common key. Here, the distributed server 40 may be provided by the image forming apparatus 20 .
[0103] In step S40, the distributed server 40 executes the administrator authentication process and the device capability acquisition process as shown in the flowchart of FIG. 7 . Proceeding to step S41 , the distributed module 42 of the distributed server 40 issues a key acquisition request to the image forming apparatus 10 through the network I / F 41 and the network 60 .
[0104] Proceeding to step S42 , the Web service execution unit 12 of the image forming apparatus 10 transmits a response to the key acquisition request issued at step S41 to the distribution server 40 through the network I / F 11 and the network 60 . The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com