Database data encryption and decryption method and system based on database connection pool
A database, encryption and decryption technology, applied in the field of database security information, can solve the problems of large amount of data in the encryption and decryption interface, slow processing process, long debugging period, etc., and achieve the effect of high encryption level, convenient decryption, and high expansion efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
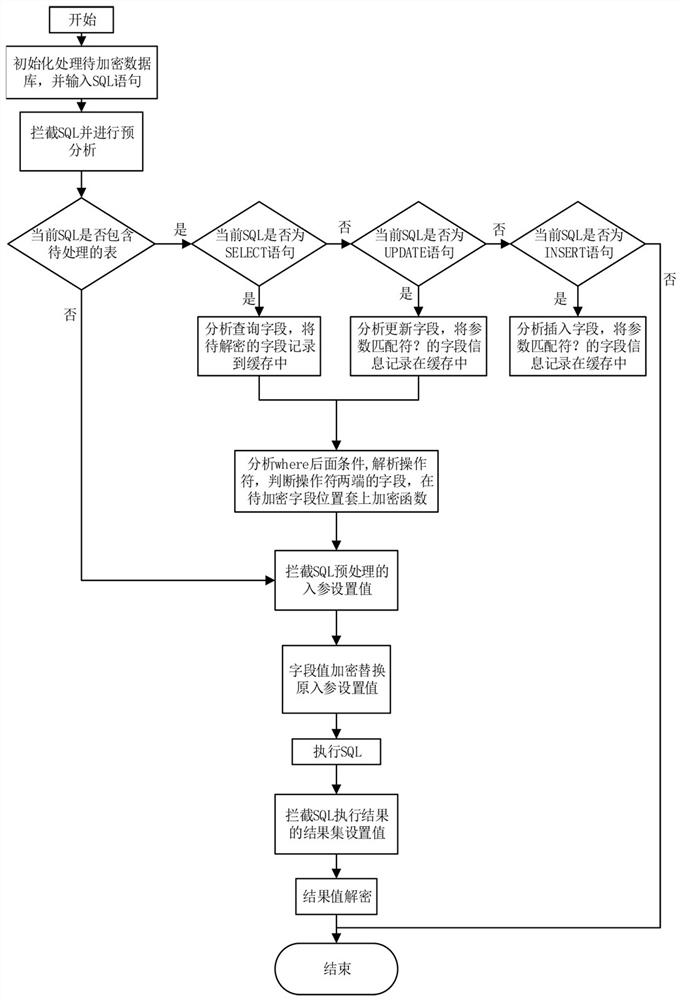
[0042] The database encryption and decryption method based on the database connection pool comprises the following steps:
[0043] S1: Perform initialization processing on tables and fields of the database to be encrypted, and input SQL execution statements, wherein the initialization processing includes configuring tables and fields to be encrypted in the database to be encrypted and decrypted. The SQL execution statement is the application statement of the database, including querying, adding, updating, and deleting a piece of data.
[0044]Perform initialization processing in SQL parsing. The SQL parser includes SqlAnalysisMeta, which is the metadata recorded after parsing SQL. It is mainly thread variables that store field information and traverse the entire life cycle of SQL execution. Contains two fields, columnSet and parameterIndexSet, and a SqlAnalysisMeta thread variable, where columnSet is the field to be encrypted and decrypted, and parameterIndexSet is the subscri...
Embodiment 2
[0092] The database encryption and decryption system based on the database connection pool includes a memory and a processor, the memory stores instructions, and the instructions are suitable for being loaded by the processor and performing the following steps:
[0093] Perform initialization processing on tables and fields of the database to be encrypted, and input SQL execution statements, wherein the initialization processing includes configuring tables and fields to be encrypted in the database to be encrypted and decrypted.
[0094] Intercept the SQL execution statement and perform field analysis on it. When the SQL execution statement includes the tables and fields of the database to be encrypted and decrypted, the statement type is judged; otherwise, the input parameter setting value replacement operation is performed.
[0095] Determine the type of the SQL execution statement:
[0096] When the SQL execution statement type is a SELECT statement, the query field is anal...
Embodiment 3
[0108] Database initialization is the configuration class for the fields of tables that need to be encrypted, that is, SqlCryptoConfig.
[0109] During initialization, configure the entity (key) and field array (value) to be encrypted in tableColumMap. In this embodiment, the database is a list of personnel and their corresponding data such as age and gender.
[0110] Enter the filter SqlAnalysisFilter: intercept the SQL statement. In this embodiment, the command "select name from tb_user where name=Han Meimei" input by the operator means that the SQL is executed to query the item information whose name is Han Meimei.
[0111] First, judge through the statement field that the current SQL is a Select statement, and judge whether the tables and fields of the Select statement are in SqlCryptoConfig. If the result exists, the field queried by the Select statement, that is, the entry information corresponding to Han Meimei needs to be decrypted. Store the query field to be decryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com