Universal safety strategy constituting method
A technology of security policy and construction method, applied in the field of mobile communication and information security, can solve problems such as security guarantee restrictions, and achieve the effect of good support, scalability and compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] According to the content of the invention, we introduce the specific implementation manner of the invention with examples.
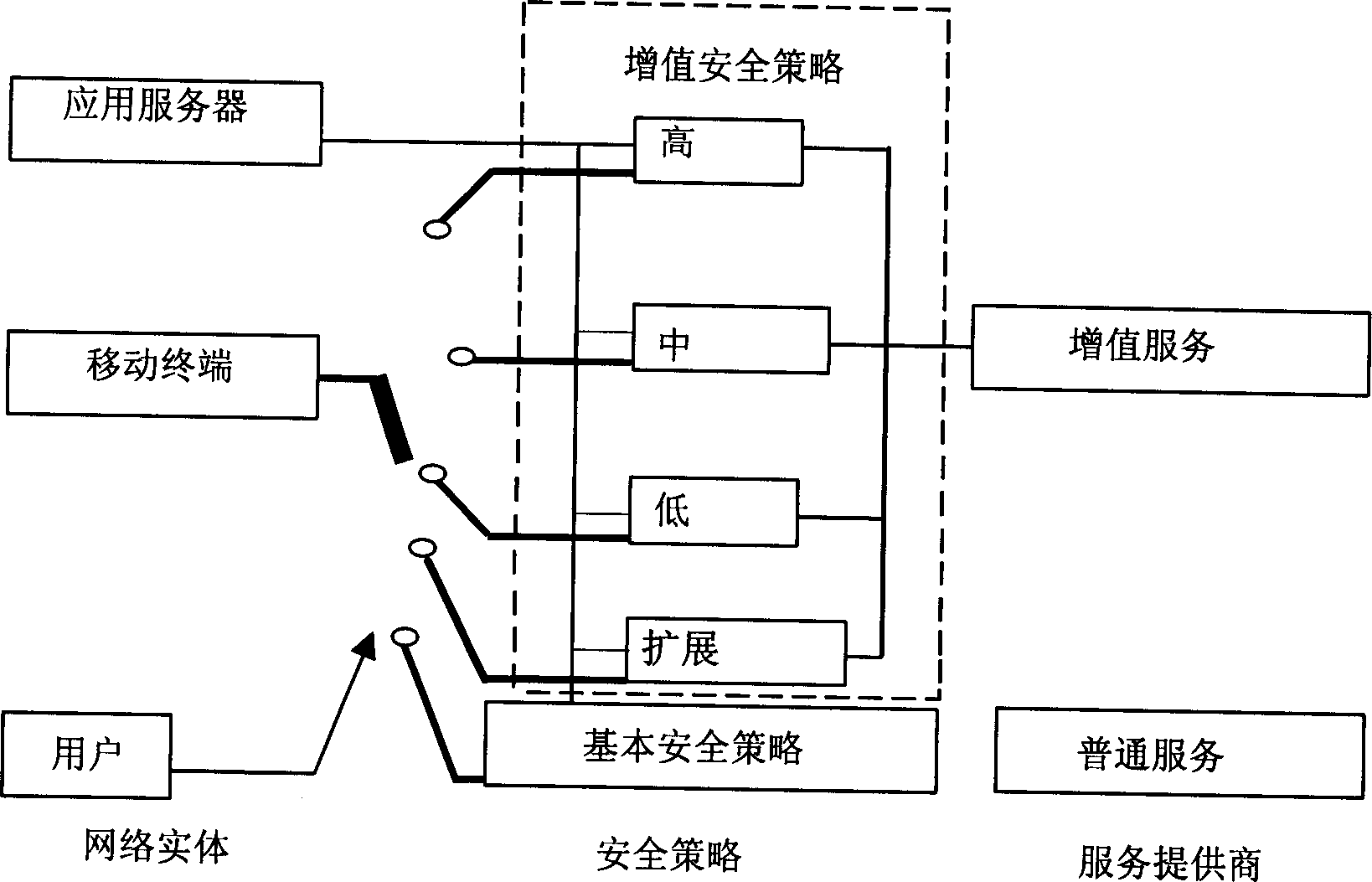
[0036] It is assumed that operators classify mobile general security policies according to security threats. combine figure 1 The framework of the security policy in the paper expounds the construction method of the general security policy.
[0037] (1) Divide the security level;
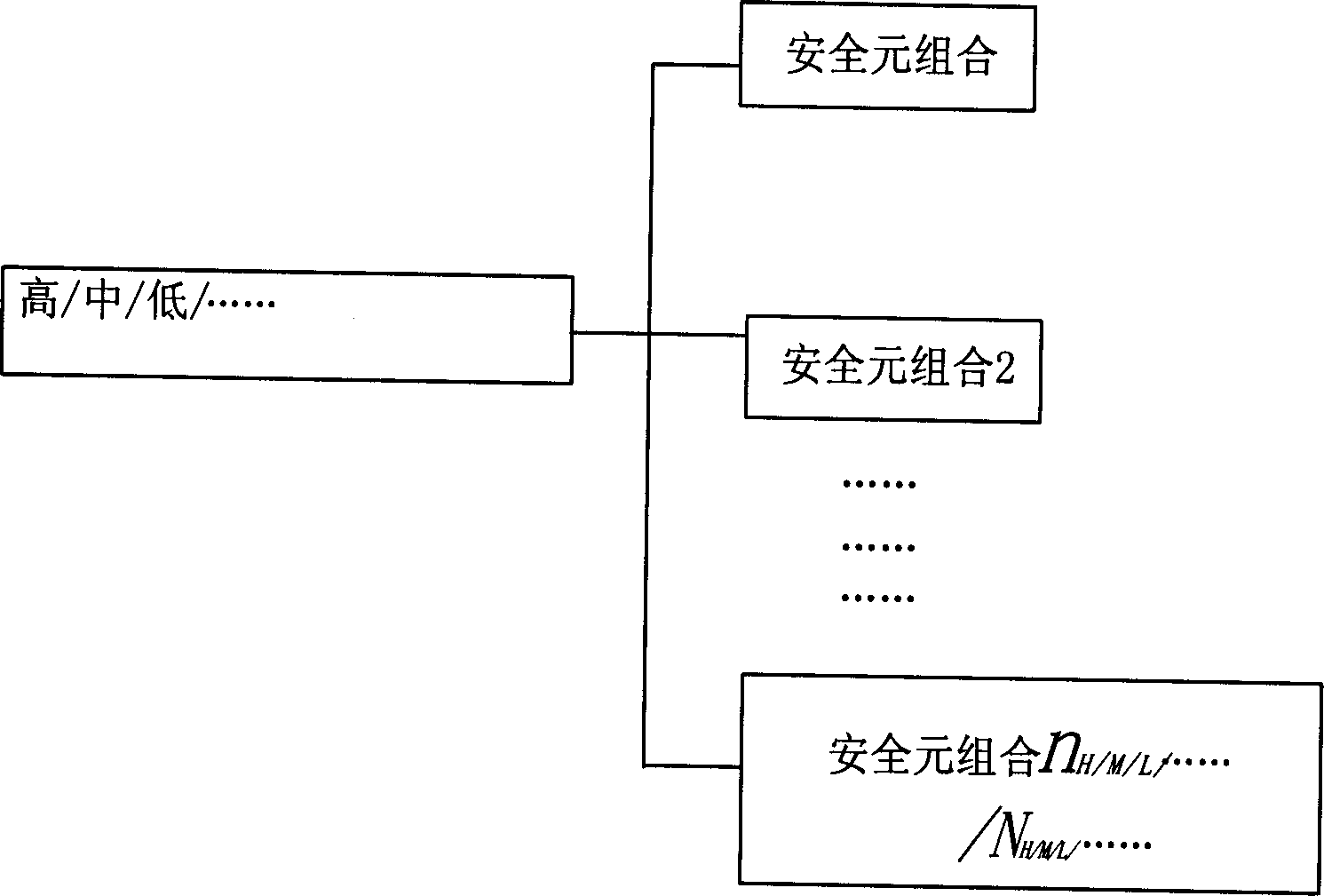
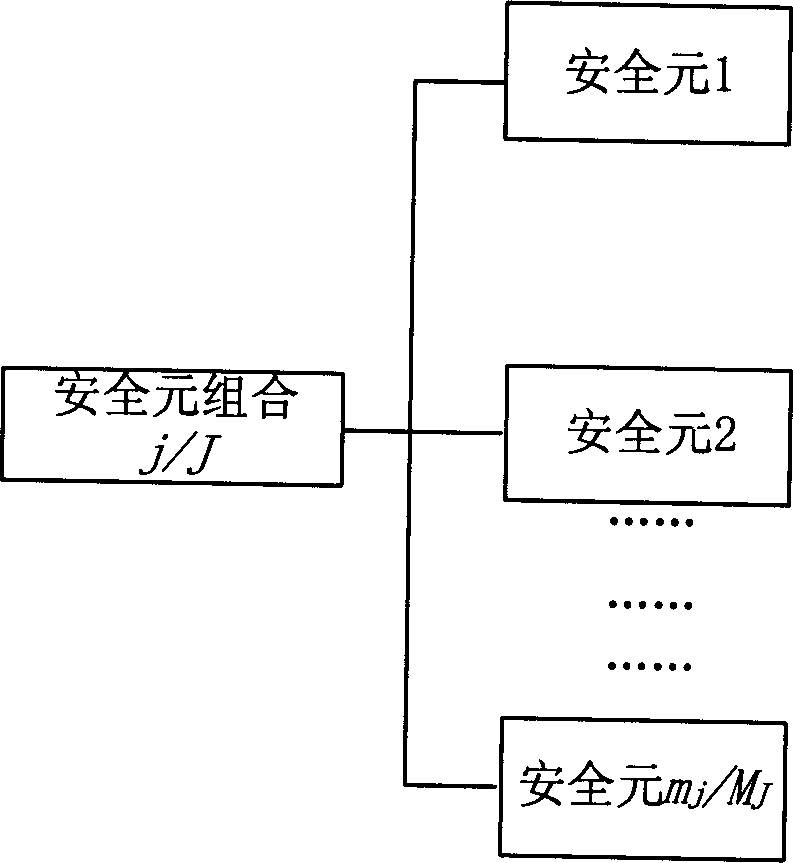
[0038] Assume that the operator divides the security requirements into two categories according to the different security requirements of various services provided to users by operators in the market: 1. At a specified time, there are idle lines for communication between mobile terminals and application services. 2. Provide a secure communication line. For category 2, the business needs security guarantees of three security intensities. Strong security guarantee, free from any attack; medium security guarantee, satisfying most communications. Low security, able to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com