Privilege minimizing method based on capability
A technology of minimization and capability, which is applied in the field of security and privilege minimization to prevent the abuse of operating system privileges, and can solve problems such as reduction, privilege abuse security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
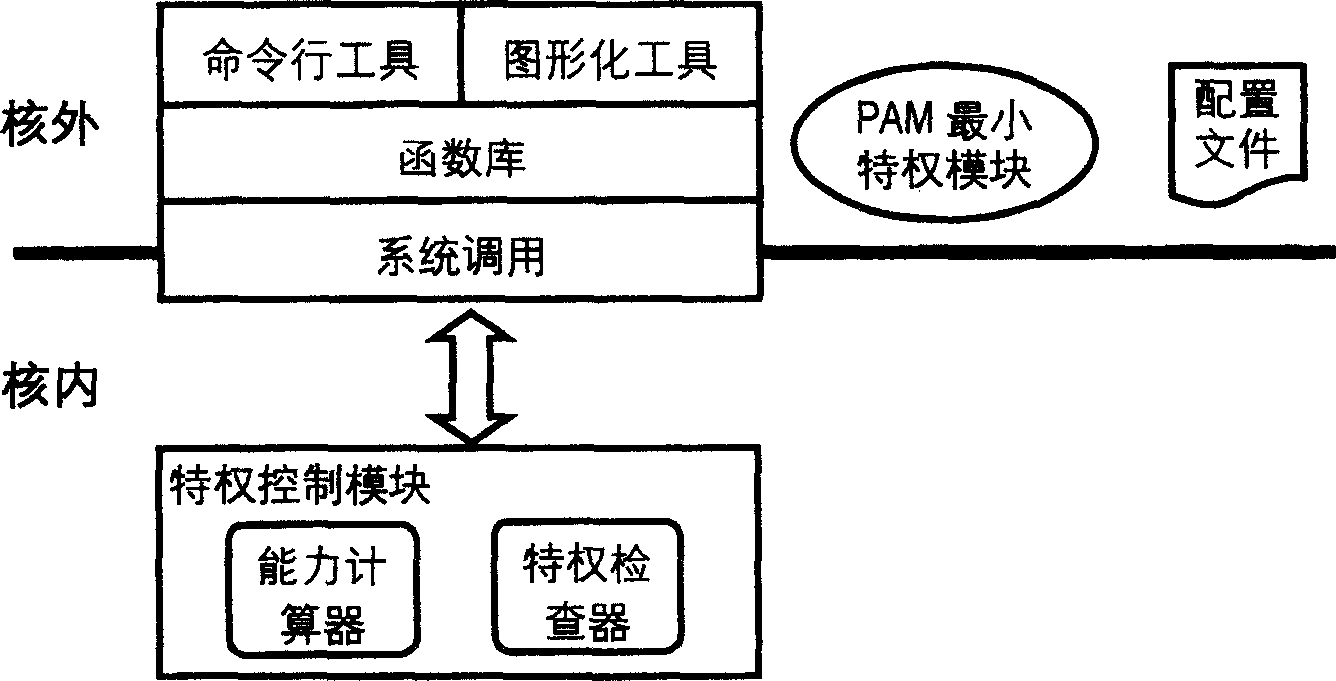
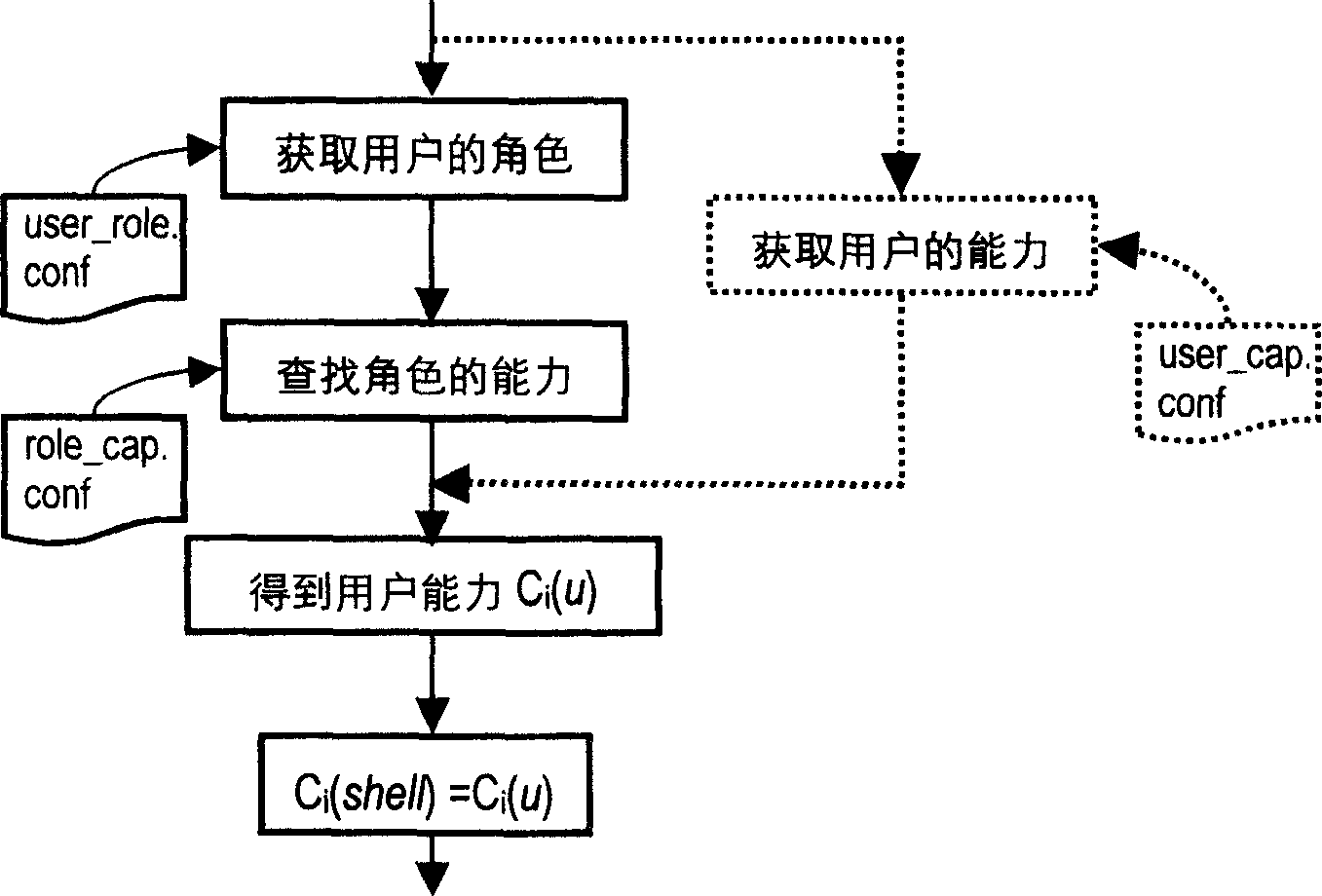
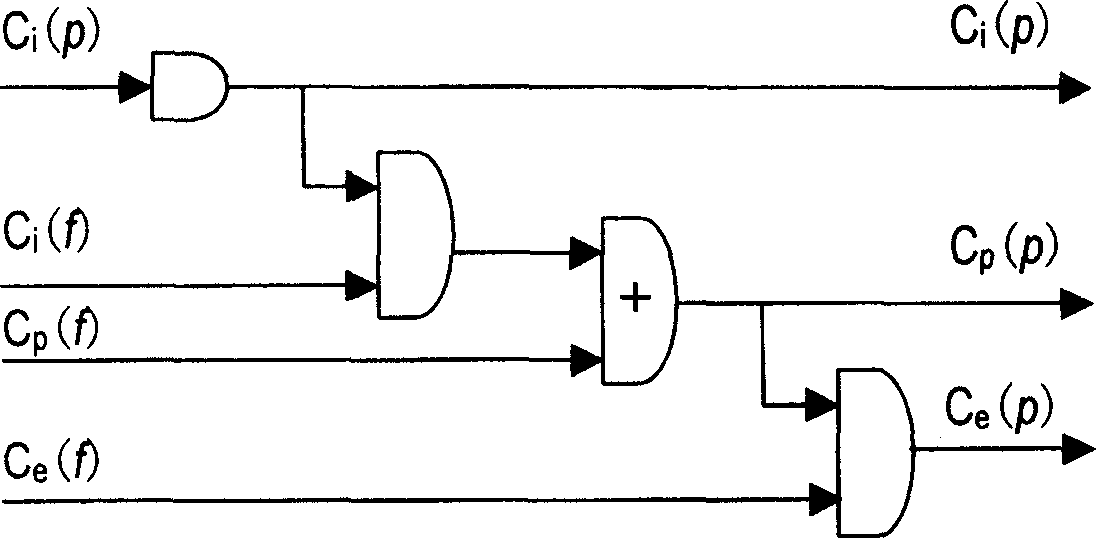
[0040] figure 1It is a structural diagram of the capability-based privilege minimization model of the present invention. The model is divided into two parts: the inner core and the outer core. The inner core is composed of a privilege control module and a system call implemented in a dynamic module manner, and the outer core is composed of a PAM minimum privilege module, It consists of function libraries, command line tools and graphical tools. The privilege control module mainly includes a capability calculator and a privilege checker. The capability calculator calculates the final privilege of the process according to the logical relationship of the capability when exec process; the privilege checker judges whether the process has the corresponding access privilege at each privilege operation point; the privilege control The module uses system calls to provide the user layer with the capability status of viewing files, setting the capability status of files, viewing the capa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com