Security management method and system for networked computer users
A network computer and security management technology, applied in the field of network computer user security management and systems, can solve problems such as inconvenient use and error-prone
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
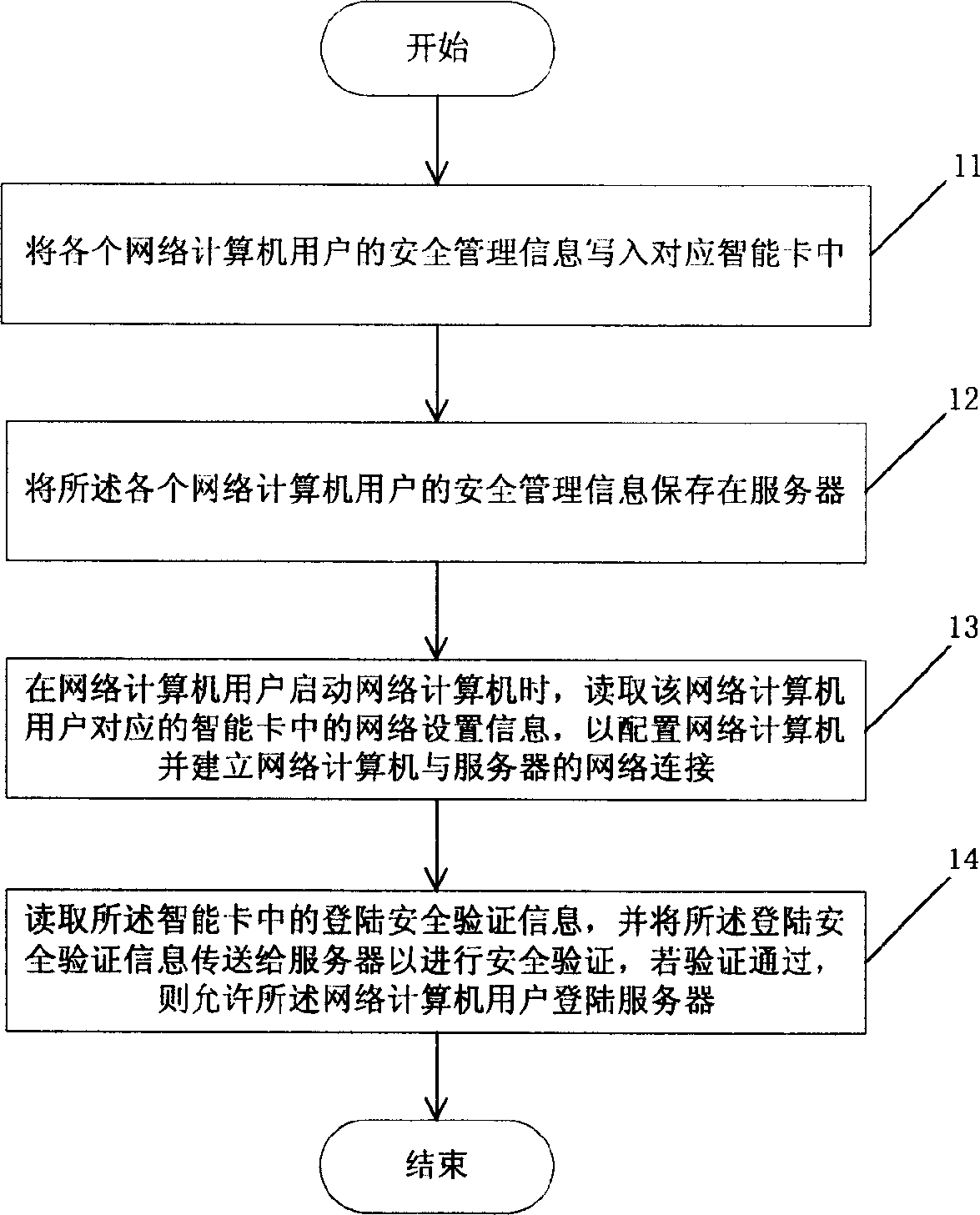
[0045] In order to realize the security management of network computer users through smart cards, the server of this embodiment and the client network computer it carries are all provided with a smart card read-write device, and the smart card read-write device includes a smart card read-write chip and a smart card slot.
[0046] In addition, smart cards, software written for smart cards and circuits developed are also required. For example, the management software that resides in memory is set on the server and its configured network computer terminal. After the server or network computer terminal is started, the program resides in the memory. , activate the smart card driver, initialize the smart card driver module to start the smart card reading and writing device, and for the network computer, if the user does not insert the smart card after starting, the management software will also remind the user to insert it. Since these are basic technologies for smart card applicatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com