Network safety guarded distributing invading detection and internal net monitoring system and method thereof
A technology for network security and intrusion detection, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems affecting data flow speed, lack of internal network monitoring, poor scalability, etc., to improve fault tolerance and reliability, The effect of standardizing the behavior of internal operators and blocking external intrusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
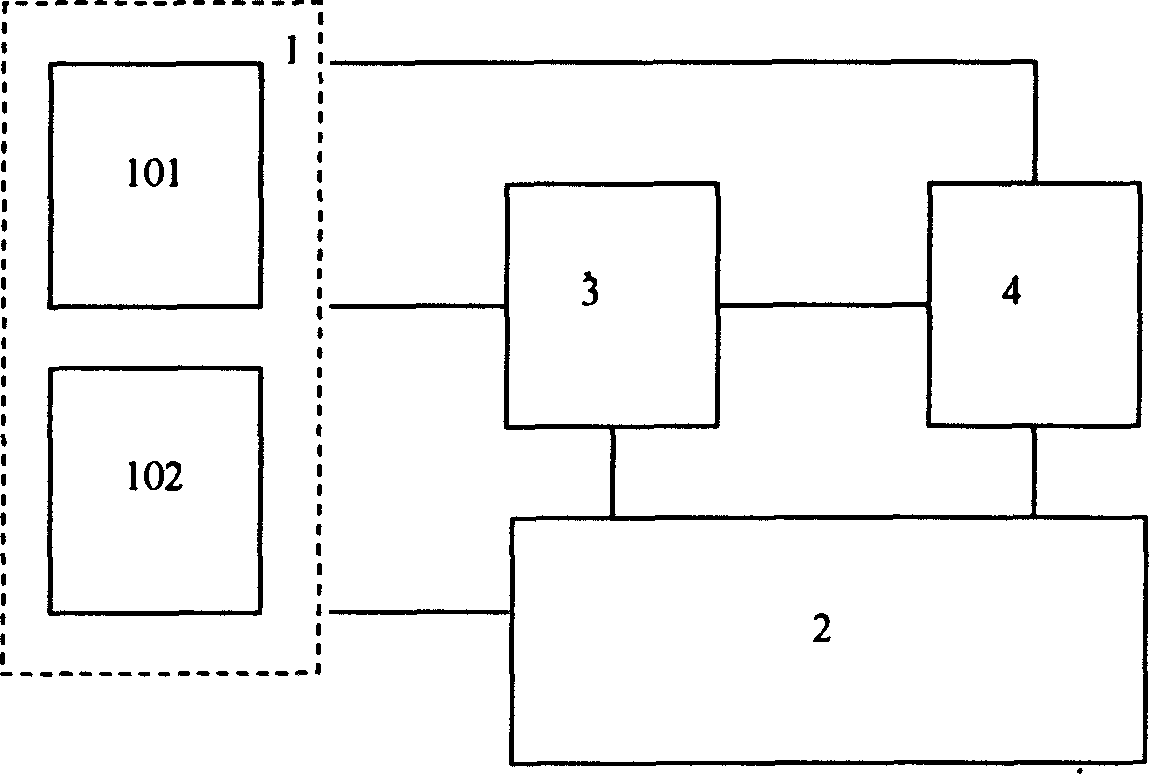
[0022] For an embodiment of the network security protection system of the present invention, see figure 1 . The distributed intrusion detection and intranet monitoring system for network security protection has a three-layer distributed structure, including a detector 1, a central controller 2, a management monitoring center 3 and a background database 4. The detector 1 includes a network detector 101 and a host detector 102 . The network detector 101 and the host detector 102 are connected with the central processing unit 2 , the management monitoring center 3 and the background database 4 .
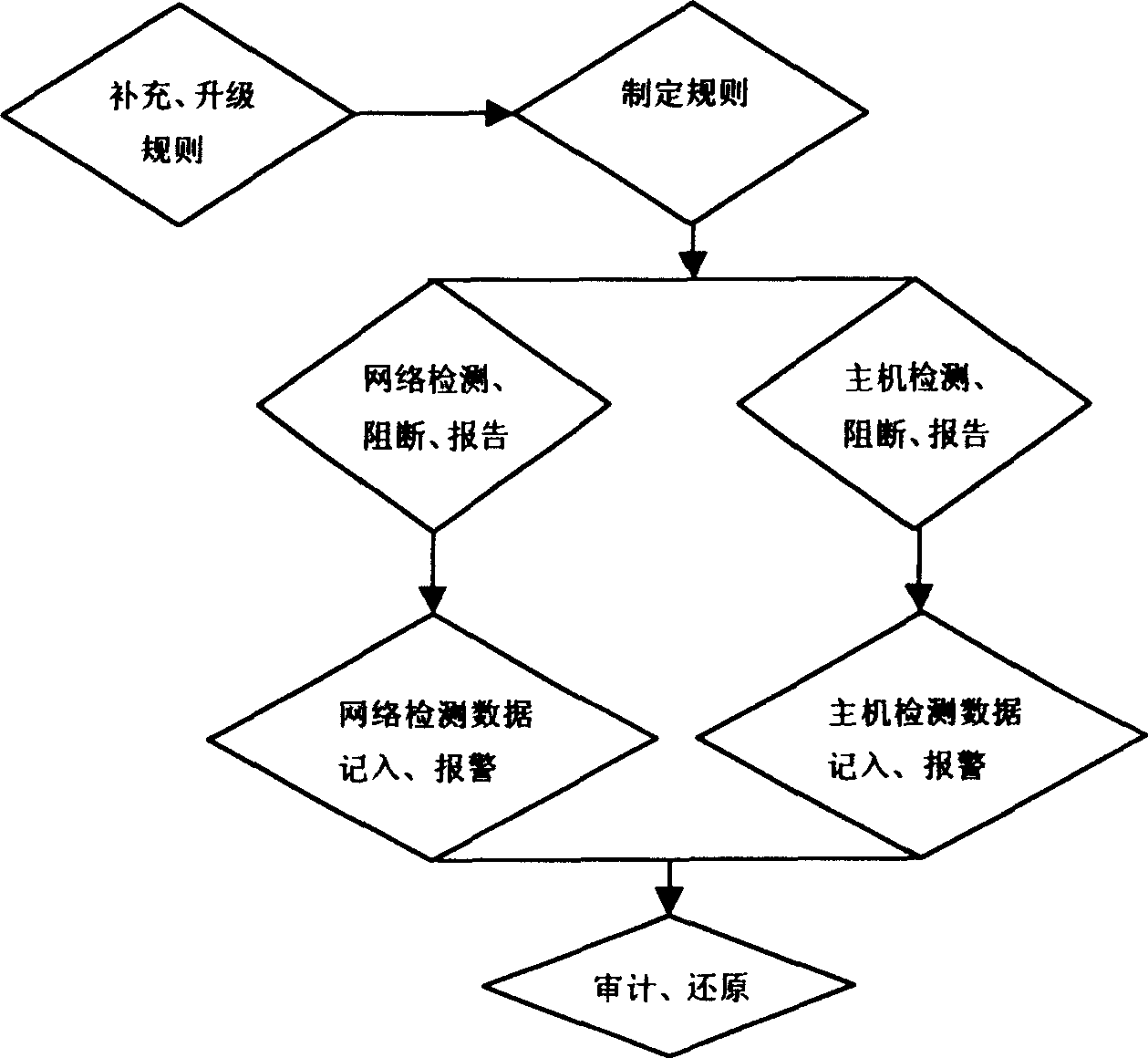
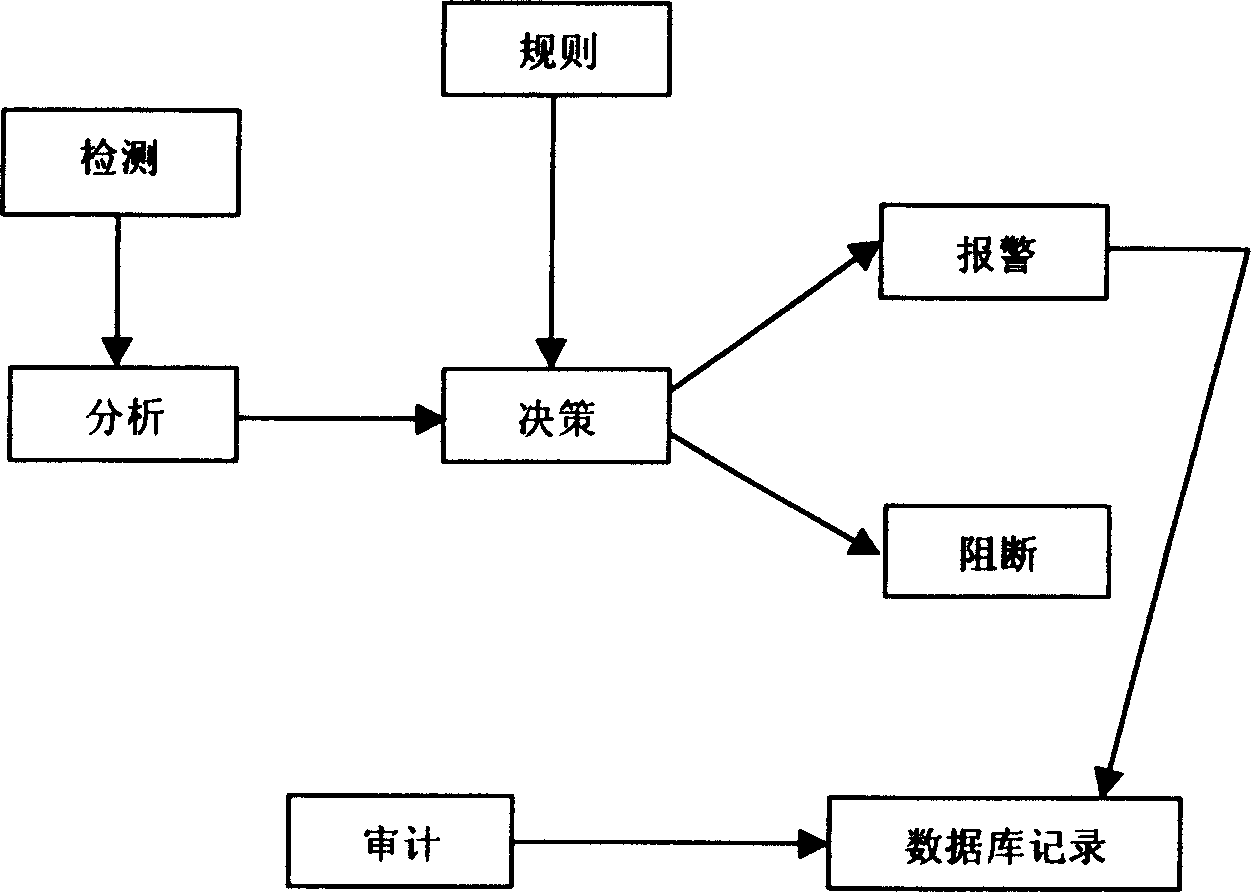
[0023] Embodiment Network detector 102 is distributed in sensitive parts of the network, based on advanced network message capture technology, monitors the data flow of the network in real time, analyzes the data flow in real time according to the security rules formulated by the management and monitoring center 3, and finds network attacks or network attacks. In the case of violation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com