Quantum encryption method for realizing safety communication
A technology of quantum encryption and secure communication, which is applied in the field of quantum encryption to realize secure communication. It can solve the problems of uncontrollable quantum key transmission content and poor encryption protocol security, and achieve the effect of loose coupling and clear functions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The quantum encryption method for realizing secure communication of the present invention will be further described in detail below in conjunction with the accompanying drawings.
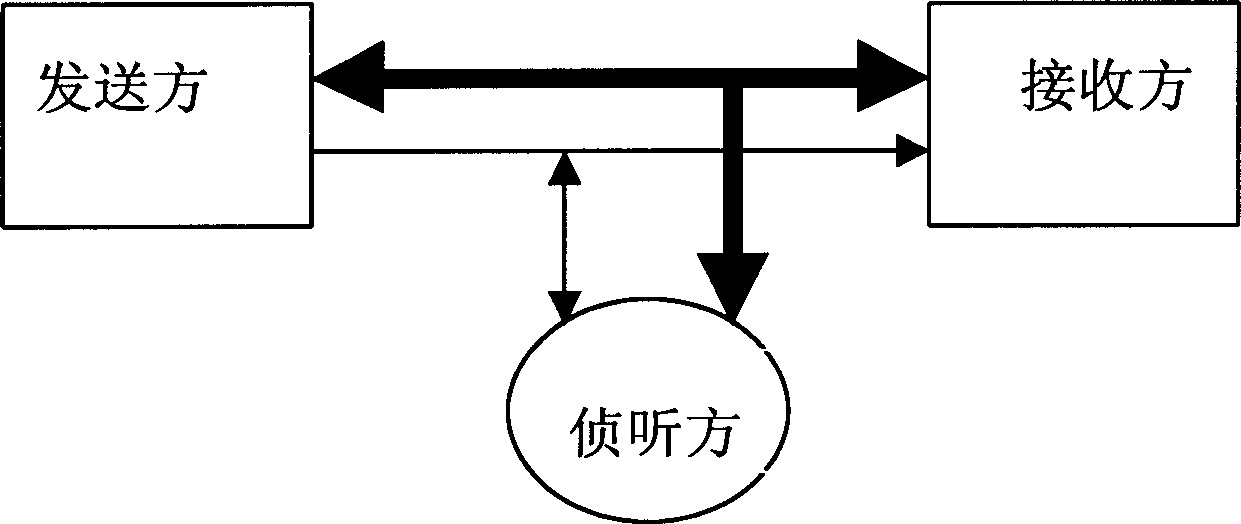
[0031] The quantum encryption method of the present invention to realize secure communication utilizes the same channel configuration as the quantum key release method, combined with the classical encoding method, to realize content-controllable quantum secure communication, and its channel structure is the same as that of the quantum key release method, as shown in figure 1 shown. There are two channels required: classical channel and quantum channel, in figure 1 In , the thick horizontal line represents the classical channel, and the thin horizontal line represents the quantum channel.
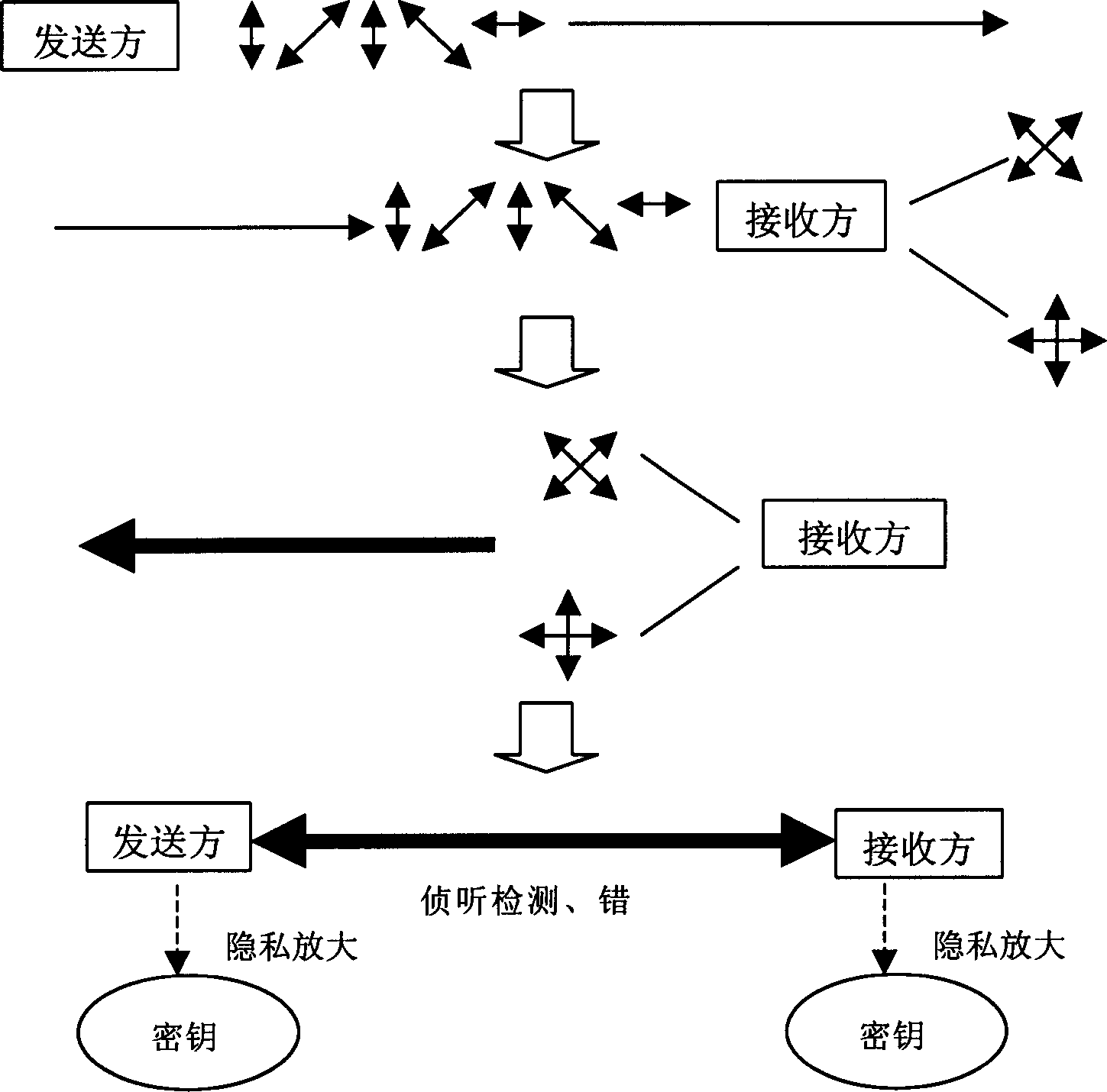
[0032] figure 2 It is a schematic flow chart of the quantum key distribution method, which has been introduced in detail in the background technology, and will not be repeated here.
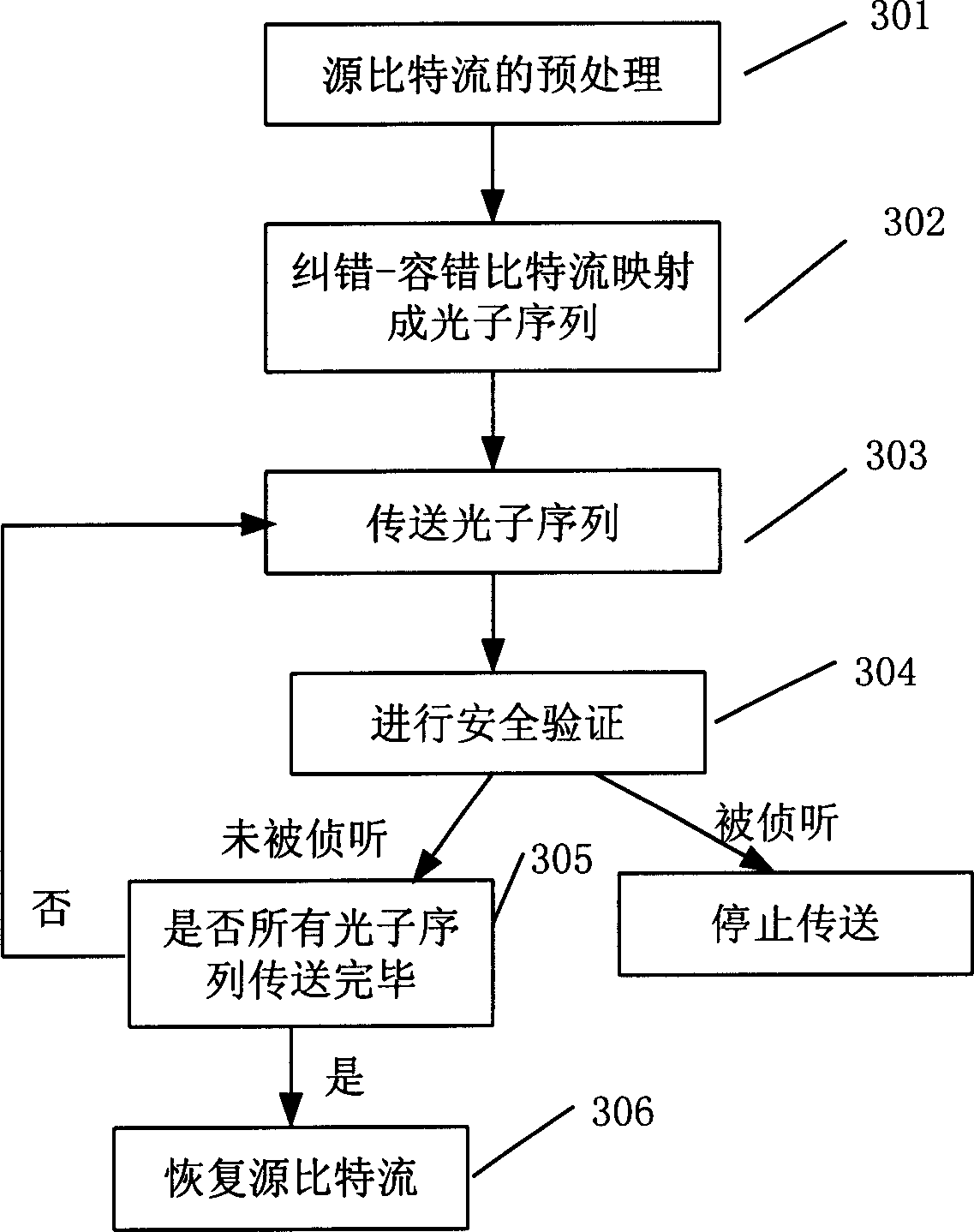
[0033] see below ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com